An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Environ Health Perspect
- v.125(3); 2017 Mar


Rethinking Environmental Protection: Meeting the Challenges of a Changing World
From climate change to hydraulic fracturing, and from drinking water safety to wildfires, environmental challenges are changing. The United States has made substantial environmental protection progress based on media-specific and single pollutant risk-based frameworks. However, today’s environmental problems are increasingly complex and new scientific approaches and tools are needed to achieve sustainable solutions to protect the environment and public health. In this article, we present examples of today’s environmental challenges and offer an integrated systems approach to address them. We provide a strategic framework and recommendations for advancing the application of science for protecting the environment and public health. We posit that addressing 21st century challenges requires transdisciplinary and systems approaches, new data sources, and stakeholder partnerships. To address these challenges, we outline a process driven by problem formulation with the following steps: a ) formulate the problem holistically, b ) gather and synthesize diverse information, c ) develop and assess options, and d ) implement sustainable solutions. This process will require new skills and education in systems science, with an emphasis on science translation. A systems-based approach can transcend media- and receptor-specific bounds, integrate diverse information, and recognize the inextricable link between ecology and human health.
Environmental and public health scientists and decision-makers are addressing new and complex environmental challenges that impact human well-being and ecological health. Energy demands have increased, and sources and approaches to developing energy are changing, raising questions about environmental and human health impacts. Land use patterns are evolving, and land use decisions can impact air, land, and water quality, and consequently, human health. Agriculture and manufacturing are also changing as technology advances. With these changes the focus of environmental protection has expanded beyond local effects and to increasingly recognize the global impacts of human activity on ecological and human health, aptly described as “wicked” problems ( Churchman 1967 ; Rittel and Webber 1973 ; Stahl 2014 ).
Wicked problems exist on various spatial scales that unfold over long temporal scales and have possible global implications. They are difficult to define, unstable, and socially complex; have no clear or single solution or end point; and extend beyond the understanding of one discipline or responsibility of one organization ( NRC 2012 ). Because of the complex interdependencies, efforts to solve one aspect of a problem may reveal or create other problems ( NRC 2012 ). Based on these definitions, the environmental pollution problems of today are termed “wicked” problems ( NRC 2012 ).
In this article, we characterize today’s most pressing wicked environmental health problems and, drawing from research conducted by the U.S. Environmental Protection Agency (EPA), Office of Research and Development and other environmental organizations, highlight tools and approaches that can be used to evaluate the many complex dimensions of these problems. Finally, we present a new framework for a systems approach for finding sustainable solutions to these complex problems.
Today’s Wicked Problems
A number of complex issues have been identified by the scientific community as wicked problems:
Climate change. In 2015, 195 countries adopted the first universal climate agreement, noting the need for an effective and progressive response to the urgent threat of climate change ( United Nations 2015 ). An increasing range of global adverse effects from climate change are affecting air quality, water resources, agriculture, and wildlife habitats, as well as basic infrastructure systems such as control of contaminated sites, waste management practices, and the functioning of the built environment ( U.S. EPA 2015a ). Climate change is altering the distribution and intensity of public health–related stressors (e.g., temperature, vector-borne diseases) and is eroding gains made in controlling air pollution in many urban areas ( U.S. EPA 2015a ). While some geographic areas may see advantages of a warmer climate (e.g., reductions in death due to extreme cold temperatures), estimates show the net impacts of climate change are likely to be widespread and significant ( McCabe and Burke 2016 ). Without continued emission reductions, the public health and welfare of current and future generations are in jeopardy, and vulnerable citizens, like children, older adults, and people living in poverty, are most at risk ( U.S. EPA 2015b ).
Energy. Choices about future energy sources have far-reaching economic, social, environmental, and public health effects. Energy provides essential support for society. From the household to the industrial setting, it is used to produce and transport goods, move people, and support a productive and growing economy. At the same time, energy production and use affect environmental quality. Oil and gas development, whether conventional or shale oil and gas, pose inherent environmental and public health risks ( GAO 2012 ). Historically, fossil fuel-based energy production and use have affected air quality and the climate, creating emissions of conventional air pollutants and greenhouse gases. As the use of natural gas has expanded, practices such as hydraulic fracturing have raised important questions about potential environmental and public health impacts ( GAO 2012 ). Water quality and quantity are affected because water is needed to produce energy, and the process of producing energy can potentially lead to water contamination. Because energy is central to a strong economy, the quest for cleaner energy sources has driven new technologies to convert sunlight, wind, or geothermal energy into electricity. Likewise, federal regulations related to energy—along with social dimensions such as consumer preference for clean energy—are driving the changing energy landscape. Scientists must be prepared to understand the full scope of these drivers and provide the research and technical knowledge to illuminate the risks and benefits and guide energy policies.
Land use. The health and well-being of a community is closely coupled with land use and development. From inner cities to rural farming communities, quality of life and environment can depend upon land use policies. Land use decisions about roads and transportation systems, industrial siting and development, agricultural land use and the provision of community access to healthy and sustainable food, housing, and open space for parks and recreation can all impact human health. The distribution of green space in populated areas is a factor in physical activity, stress, and related physical and mental health issues ( Lee and Maheswaran 2010 ; Lachowycz and Jones 2013 ). By influencing social interaction and the variety, density, and accessibility of necessities and amenities, decisions regarding land use planning affect well-being through community vibrancy and the autonomy of marginalized populations ( Jackson 2003 ). Land use decisions can drive cascading events that may adversely impact ecological and human health. For example, land use decisions can influence fire risk ( Butsic et al. 2015 ), and wildland fires can alter the landscape, increase erosion, and foster runoff ( Morrison and Kolden 2015 ). Resulting wildland fire smoke, a mixture of gases and fine particles, can cause respiratory illness and aggravate chronic heart and lung diseases ( U.S. EPA 2003 ; Rappold et al. 2011 ).
Water quantity and quality. About 400 billion gallons of water are used each day in the United States, and we face many challenges in maintaining the safety and sustainability of these water resources ( U.S. EPA 2015d ). For example, emerging chemical contaminants, such as perfluorinated compounds, found nationwide in water supplies, may not be removed by conventional water treatment or addressed by policy or regulatory actions ( Sedlak 2016 ). An aging water system infrastructure has led to an estimated 240,000 water main breaks in the United States annually ( ASCE 2013 ), which can only exacerbate water shortages. The recent water crisis in Flint, Michigan, where lead leached from pipes in older drinking water systems and reached levels that exceeded regulatory limits, also highlighted the importance of proper treatment of source water to prevent such occurrences ( Bellinger 2016 ). Harmful algal blooms (HAB), a natural phenomenon, can be influenced by anthropogenic forces and climate change: and expanding human populations could impact HAB occurrence and public health impacts ( Berdalet et al. 2015 ). Drought is a concern for many communities, and the effects of climate change are expected to increase the frequency, intensity, and duration of droughts in many regions ( White House 2016 ). These examples are just a few of the many challenges threatening the safety and sustainability of the water supply in the United States.
Connecting the Dots—A Systems Approach to Environmental Protection
Environmental challenges have historically been managed with compartmentalized and pollutant specific, risk-based approaches. Although such approaches were successful in addressing part of the problem in the past, they are ill-suited to solve today’s wicked environmental challenges. Rather, today’s problems call for a systems approach that looks at a problem holistically, includes all the drivers and stressors that affect it and the dimensions that frame it, and integrates information from human health and ecological sciences and the social sciences to formulate sustainable solutions to environmental issues.
To understand the links between public health, the environment, and society, the interactions of factors within a complex system must be evaluated in a realistic way, regardless of its size, which can range from the scale of the molecule to that of the biosphere (global ecosystem) ( Figure 1 ). Systems thinking considers the cumulative effects of multiple stressors, evaluates a range of alternatives, analyzes upstream and downstream life-cycle implications, involves a broad range of stakeholders, and uses interdisciplinary scientific approaches ( NRC 2012 ). Systems approaches are not new, and the scientific literature provides many examples ( Powers et al. 2012 ; Briggs 2008 ; Fiksel 2006 ). In public health, Guyer (1997) describes a systems process for problem solving that first defines the problem and measures its magnitude, then develops a framework for evaluating the key determinants (biologic, epidemiologic, social, cultural, economic, and political). Contemporary assessments stress the need for systems thinking. For example, a health impact assessment (HIA) uses a systems approach to array data sources and analytic methods and considers input from stakeholders to determine potential effects of a proposed action or decision on the health of a population and the distribution of those effects within the population ( NRC 2011 ). Likewise, a life-cycle assessment uses systems approaches to evaluate a cradle-to-grave process, including all stages of a product’s life from the perspective that they are interdependent ( U.S. EPA 2006 ).

Nested systems from the molecular level to the biosphere.
The Tools of 21st-Century Science and Technology
Concurrent with the changing nature of environmental issues, science and technology are evolving rapidly and offering new tools and methods of analysis needed in taking a systems approach to a problem. For example, modeling real-world scenarios can inform our understanding of interactions within a system, which helps forecast possible intervention outcomes. Computational models, which use and integrate data from many sources to understand and predict system dynamics and impacts of environmental pollutants, have become central to environmental decision-making ( NRC 2007 ). Computational science provides more information than ever before along with the means for analyzing what the information means. The Toxicology Testing in the 21st Century (Tox21), a federal collaborative program that develops high-throughput assays to efficiently test a chemical’s potential to cause adverse health effects ( U.S. EPA 2015c ), is anticipated to deliver a wealth of information about the potential effects of tens of thousands of chemicals ( Attene-Ramos et al. 2013 ). Computational exposure science, which integrates advances in chemistry, computer science, mathematics, statistics, and social and behavioral sciences with new models and data collection methods, will provide tools to better understand population exposures and link exposures to health outcomes ( Egeghy et al. 2016 ).
Changes in technology have spurred the development of low-cost compact sensors for measuring environmental parameters and indicators of health ( Kumar et al. 2015 ; Murphy et al. 2014 ; Chan et al. 2012 ). These sensors can be deployed in multiple locations to monitor pollutant concentrations around a facility or community more accurately than is possible with single stationary monitors ( Snyder et al. 2013 ). Satellite technology can enhance air quality forecasting, emissions estimation, and exposure assessment for human health studies ( Hoff and Christopher 2009 ). The availability of personal computers, mobile phones, and Internet access has revolutionized the communication of information and ideas. Citizen science, which encourages public participation in the scientific process ( Kalil and Wilkinson 2015 ), provides a new way to engage the public in solving problems. Crowdsourcing—an open call for voluntary assistance from a large group of individuals ( Kalil and Wilkinson 2015 )—can help collect information at large geographic scales and over long periods of time.
These technological advances will yield enormous volumes of complex data, both structured and unstructured, originating from different sources. Big data may revolutionize how we monitor environmental quality and understand how humans interact and respond to the environment ( Kays et al. 2015 ) and how the environment responds to human activity ( Dagliati et al. 2015 ). However, the analysis of and need for access and discoverability of big data presents challenges that include protecting individual interests and privacy, managing enormous volumes of data, identifying the most important types of data, understanding data quality, integrating data into a form to analyze and guide decisions, and making the information publically accessible in forms that can be shared and combined for analysis.
Moving to the Future
Moving forward, we need a new comprehensive approach to solve environmental challenges that a ) begins with strong problem formulation, b ) relies on systems approaches and tools to integrate different types of data from multiple disciplines, c ) draws on information generated from new technologies, and d ) considers novel sources of data, such as citizen science. Evolving from case experiences, tools, and approaches developed over the years, we propose adopting a new framework ( Figure 2 ) for environmental science that uses a systems approach to integrate ecological and human health information to solve environmental challenges. This framework includes the following elements and considers vested partners, communities, scientists, decision makers, and the public, and the need for science translation, education, and communication. Table 1 describes each element, summarizes the approaches, and provides examples of tools designed to facilitate its use.

Framework for applying integrated science to protect the environment and public health and well-being.
Considerations, information sources, tools, and approaches for framework elements.
| Considerations and types of information | Example tools and approaches |
|---|---|
| Step 1 – Formulate the problem holistically | |
| Step 2 – Gather and synthesize diverse information | |
| Step 3 – Develop and assess options | |
| Step 4 – Implement sustainable solution(s) | |
| Step 5 – Monitor and evaluate results | |
Formulate the problem holistically. Environmental health problems should be framed within a systems context and should consider ecological, health, social, and economic factors across space and time. Interactions, interdependencies, and cumulative effects are considered, as are the values and goals of vested partners, including the community and the public. By engaging end users early in the process, information and solutions will be more responsive and relevant to their needs. Formulating the problem holistically will improve understanding of potential unanticipated outcomes. Tools and guidance for problem formulation exist. For example, Suter (1993) described the process of creating a conceptual model for ecological risk assessments. This approach can help inform our understanding of system linkages, points of potential intervention, and the information needed to inform policy decisions. Gregory et al. (2012) and Yee et al. (2015) proposed a structured decision-making process, and Bruins et al. (2010) demonstrated the use of problem formulation for addressing complex socio-environmental problems. The U.S. EPA’s “Framework for Human Health Risk Assessment to Inform Decision-Making” ( U.S. EPA 2014b ) describes the importance of problem formulation and provides information to consider during this process.
Gather and synthesize diverse information. Guided by problem formulation, the next step is to identify diverse data and information needed to support the assessment. Economic, social, and environmental information should be considered, including socioeconomic status, health, cultural resources, local knowledge, traditions and practices, and existing conditions of the built and natural environment. For example, a more holistic model based on a systems approach was recently proposed for improving children’s environments and health across developmental life stages ( Tulve et al. 2016 ). Various tools can inform this step. Ideally, they should be discoverable and widely accessible to users in web-based formats. For example, the “Community-Focused Exposure and Risk Screening Tool” (C-FERST; https://www.epa.gov/c-ferst ), a community mapping, information access tool, can inform community assessments and decision-making ( Zartarian et al. 2011 ). “EnviroAtlas,” an interactive mapping tool, can be used to explore the benefits people receive from nature ( Pickard et al. 2015 ). The EnviroAtlas Eco-Health Relationship browser ( https://www.epa.gov/enviroatlas/enviroatlas-eco-health-relationship-browser ) provides information about how health issues are linked to the metrics of ecosystem services—the societal benefits from nature that underpin almost every aspect of human well-being ( Jackson et al. 2013 ; U.S. EPA 2015d ). The “Environmental Quality Index” (EQI) provides a metric for overall environmental quality that incorporates air, water, land, the built environment, and sociodemographics ( U.S. EPA 2014a ).
Develop and assess options. This step helps inform understanding of the consequences of potential decisions under consideration. The benefits and risks of options should be assessed and tradeoffs and costs (monetary and nonmonetary) should be examined under different scenarios. The priorities and concerns of the community and stakeholders should be considered. This step also includes estimating the distribution of impacts or consequences (positive and negative) across the population, including at-risk populations such as children, older adults, pregnant and nursing women, and indigenous people, while considering population vulnerability versus individual risk. At this point, feasible near- and long-term actions that mitigate negative impacts and promote sustainability and resiliency are identified. A variety of traditional and newer tools can be applied. For example, human health and ecological risk assessment will add valuable information about the impacts of various stressors. HIA can provide a structure for assembling information and assessing options, as can structured decision-making ( Gregory et al. 2012 ; Yee et al. 2015 ). A web-based decision analysis framework called “Decision Analysis for a Sustainable Environment, Economy, and Society” (DASEES) can help inform this process ( Yeardley et al. 2011 ). Environmental justice analysis, using mapping tools like C-FERST, EnviroAtlas, and “EJ-SCREEN: Environmental Justice Screening and Mapping Tool” ( http://www.epa.gov/ejscreen ), can provide valuable information about sensitive populations and population risk.
Implement sustainable solutions. Here, the suite of actions to implement solution(s) is selected. Solutions may range from improved infrastructure to interventions to behavioral changes. Implementers may include government agencies, state or local governments, or other stakeholders. These actions might include short- or long-term elements such as installation of a green street to reduce localized flooding combined with development of an area-wide plan for green infrastructure to improve overall water flow in a community. Communicating the scientific basis of solutions to decision makers, communities, and other stakeholders is essential. Ensuring transparency is crucial, as is engaging and empowering communities with knowledge, tools, data, and information.
Monitor and evaluate results. This step evaluates whether the approach provided sufficient information to identify, compare, and implement solutions and whether the chosen solution has the desired short- and long-term positive effects. Certain indicators or data sets could be used to reflect changes in environmental conditions or human health and well-being over time. For example, the “EPA Report on the Environment” provides indicators of national trends in air, water, land, human exposure and health, and ecological condition ( U.S. EPA 2015c ), and the EQI provides a single index of environmental quality that accounts for the multiple domains of the environment that encompass an area where humans interact ( Lobdell et al. 2011 ). The “EnviroAtlas” may be useful for monitoring and evaluating solutions at various spatial scales. Consideration should also be given to whether unconventional data sources—such as citizen science—can inform evaluation.
Environmental protection in today’s world requires recognition of the interconnection of our environmental systems. This framework provides a structure to address today’s complex problems by considering multiple dimensions and a variety of data sources—a systems approach. Similar frameworks exist and have provided the basis for this approach ( Reis et al. 2013 ; Powers et al. 2012 ; Briggs 2008 ). However, this framework represents an evolution of what has been proposed and used to date, and it provides a construct through which environmental and public health scientists can conduct future research, both fundamental and translational, to inform tomorrow’s solutions. We acknowledge the tension between using this framework and traditional approaches, including those driven by regulatory statutes and policies. We are not recommending replacement of those policies that have led to measurable progress. Rather, we recommend systems thinking as a path to enrichment of the scientific basis for decision-making to address wicked problems by creating opportunities for new partnerships and enhancing collaboration across traditional media-specific silos.
Recommendations for Framework Implementation
- Problem formulation as a key step toward integrating science to support systems-based problem solving. The framework presented here is grounded in strong problem formulation. This step is essential for successfully assessing issues and formulating and evaluating options. The environmental science community should be trained in approaches to problem formulation, and environmental and public health organizations should seek opportunities to incorporate problem formulation in their scientific approaches.
- Integrate additional skill sets into environmental problem solving. Informing solutions to complex environmental problems requires insight, expertise, and viewpoints from many scientific disciplines, along with policy makers, public officials, and community stakeholders. Traditionally, the fields of ecology, toxicology, and engineering have been predominant in environmental science. To conduct systems-based science, scientific teams will also need to include public health practitioners, earth scientists, economists, behavioral and other social scientists, database managers, programmers, software engineers, planners, physicians, systems analysts/experts, and science communicators.
- Make systems approaches core in the education of future scientists and decision-makers. Traditional training in environmental science has taken a reductionist approach to focus on specific mechanisms of a stressor and its effect on an ecosystem or human health. However, science students today are increasingly trained to look at the system and embrace cross-disciplinary problem solving. Current and future environmental scientists will need to be trained on systems approaches for conducting science and solving problems. A compilation of systems-based tools and examples of how systems approaches can be applied to inform sustainable solutions will help ensure that environmental scientists are adequately trained.
- Use effective science communication to ensure that decision makers and communities understand and accept the science. This framework requires scientists to work closely with vested partners and decision makers and ensure the science is translated and communicated throughout the process. As with the division of risk assessment and risk management articulated by NRC (1983) , scientists typically do not choose a solution or make a policy or risk management decision. Therefore, it is critical that the science is communicated clearly and that decision-makers and vested partners are educated about the science. Science communication experts will be needed, and scientists will need to be better trained in effective communication.
Conclusions
U.S. EPA authorities have successfully managed gross pollution problems using command and control media-specific approaches. The health of our rivers has improved, the vast majority of Americans have access to safe and clean drinking water, exposure to many toxic pollutants and pesticides has been reduced, and nationwide air quality has improved significantly for many air pollutants ( U.S. EPA 2012 ). However, today’s environmental problems are daunting. Their dimensions go well beyond the traditional risk assessment and risk management paradigm that has been the basis of environmental protection over the past several decades. It is time to embrace a new way of thinking. From safe drinking water to energy choices and pest management, to urban design, systems approaches can help inform sustainable solutions that ensure environmental and public health protection. In times of emergency response, systems approaches will help us understand the multiple dimensions of the situation, how the environment and human health are impacted, and how various solutions may address the issue or potentially cause unanticipated consequences. Wicked problems require thoughtful synthesis of science and decision-making. The framework proposed here provides a much-needed structure, grounded in strong problem formulation, to build upon our progress and strengthen environmental and public health protection for the future.
Acknowledgments
The authors would like to thank the following individuals: K. Brooks, former Acting Assistant Administrator, Office of Administration and Resources Management, U.S. Environmental Protection Agency (EPA) for his insights into and references about the history of the U.S. EPA; S. Edwards and R. Hines of the U.S. EPA for Figure 1, which was used to describe the underpinning of the systems framework research at the National Health and Environmental Effects Research Laboratory, U.S. EPA; and J. Havel at SRA International, Inc. for the design of Figure 1.
The views expressed in this paper are those of the authors and do not necessarily reflect the views or policies of the U.S. EPA.
The authors declare they have no actual or potential competing financial interests.
- ASCE (American Society of Civil Engineers) 2013 Report Card for America’s Infrastructure. 2013 http://www.infrastructurereportcard.org/a/#p/drinking-water/overview [accessed 13 July 2016]
- Attene-Ramos MS, Miller N, Huang R, Michael S, Itkin M, Kavlock RJ, et al. 2013. The Tox21 robotic platform for the assessment of environmental chemicals—from vision to reality. Drug Discov Today 18 15–16 716 723, doi: 10.1016/j.drudis.2013.05.015 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Bellinger DC. 2016. Lead contamination in Flint — an abject failure to protect public health. N Engl J Med 374 12 1101 1103, doi: 10.1056/NEJMp1601013 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Berdalet E, Fleming LE, Gowen R, Davidson K, Hess P, Backer LC, et al. 2015. Marine harmful algal blooms, human health and wellbeing: challenges and opportunities in the 21st century. J Mar Biol Assoc U.K. 96 1 61 91, doi: 10.1017/S0025315415001733 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Briggs DJ. 2008. A framework for integrated environmental health impact assessment of systemic risks. Environ Health 7 61, doi: 10.1186/1476-069X-7-61 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Bruins RJF, Munns WR, Jr, Botti SJ, Brink S, Cleland D, Kapustka L, et al. 2010. A new process for organizing assessments of social, economic, and environmental outcomes: case study of wildland fire management in the USA. Integr Environ Assessment Manag 6 3 469 483, doi: 10.1897/IEAM_2009-075.1 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Butsic V, Kelly M, Moritz MA. 2015. Land use and wildfire: a review of local interactions and teleconnections. Land 4 1 140 156, doi: 10.3390/land4010140 [ CrossRef ] [ Google Scholar ]
- Chan M, Estève D, Fourniols JY, Escriba C, Campo E. 2012. Smart wearable systems: current status and future challenges. Artif Intell Med 56 3 137 156, doi: 10.1016/j.artmed.2012.09.003 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Churchman CW. Wicked problems [Editorial]. Manage Sci. 1967; 14 (4):B141–B142. [ Google Scholar ]
- Dagliati A, Marinoni A, Cerra C, Decata P, Chiovato L, Gamba P, Bellazzi R. 2015. Integration of administrative, clinical, and environmental data to support the management of type 2 diabetes mellitus: from satellites to clinical care. J Diabetes Sci Technol 10 1 19 26, doi: 10.1177/1932296815619180 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Egeghy PP, Sheldon LS, Isaacs KK, Özkaynak H, Goldsmith MR, Wambaugh JF, et al. 2016. Computational exposure science: an emerging discipline to support 21st-century risk assessment. Environ Health Perspect 124 6 697 702, doi: 10.1289/ehp.1509748 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Fiksel J. 2006. Sustainability and resilience: toward a systems approach. Sustainability: Sci, Pract , Policy 2 2 14 21 [ Google Scholar ]
- Fiksel J, Bruins R, Gatchett A, Gilliland A, ten Brink M. 2014. The triple value model: A systems approach to sustainable solutions. Clean Technol Environ Policy 16 4 691 702, doi: 10.1007/s10098-013-0696-1 [ CrossRef ] [ Google Scholar ]
- GAO (U.S. Government Accountability Office) Oil and Gas: Information on Shale Resources, Development, and Environmental and Public Health Risks. GAO-12-732. September 2012. 2012 http://www.gao.gov/products/GAO-12-732 [accessed 20 December 2016]
- Gottlieb L, Egerter S, Braveman P. New York, NY: Robert Wood Johnson Foundation; 2011. Health Impact Assessment: A Tool for Promoting Health in All Policies. [ Google Scholar ]
- Gregory R, Failing L, Harstone M, Long G, McDaniels T, Ohlson D. Oxford, UK: Wiley-Blackwell; 2012. Structured Decision Making: A Practical Guide to Environmental Management Choices . [ Google Scholar ]
- Guyer B. New York: Oxford University Press; 1997. Problem-solving in public health. In: Epidemiology and Health Services . 1st edition. Armenian HK, Shapiro S, eds. [ Google Scholar ]
- Hoff RM, Christopher SA. 2009. Remote sensing of particulate pollution from space: have we reached the promised land? J Air Waste Manag Assoc 59 6 645 675, doi: 10.3155/1047-3289.59.6.645 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Jackson LE. The relationship of urban design to human health and condition. Landscape Urban Plann. 2003; 64 (4):191–200. [ Google Scholar ]
- Jackson LE, Daniel J, McCorkle B, Sears A, Bush KF. 2013. Linking ecosystem services and human health: the Eco-Health Relationship Browser. Int J Public Health 58 747 755, doi: 10.1007/s00038-013-0482-1 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Kalil T, Wilkinson D. 2015. Accelerating Citizen Science and Crowdsourcing to Address Societal and Scientific Challenges. Executive Office of the President, Washington, DC. https://www.whitehouse.gov/blog/2015/09/30/accelerating-use-citizen-science-and-crowdsourcing-address-societal-and-scientific [accessed 13 May 2016] [ Google Scholar ]
- Kays R, Crofoot MC, Jetz W, Wikelski M 2015. Terrestrial animal tracking as an eye on life and planet. Science 348 6240 aaa2478-1 aaa2478-9, doi: 10.1126/science.aaa2478 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Kumar P, Morawska L, Martani C, Biskos G, Neophytou M, Di Sabatino S, et al. 2015. The rise of low-cost sensing for managing air pollution in cities. Environ Int 75 199 205, doi: 10.1016/j.envint.2014.11.019 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lachowycz K, Jones AP. 2013. Towards a better understanding of the relationship between greenspace and health: development of a theoretical framework. Landscape Urban Plann 118 62 69, doi: 10.1016/j.landurbplan.2012.10.012 [ CrossRef ] [ Google Scholar ]
- Lee ACK, Maheswaran R. 2010. The health benefits of urban green spaces: a review of the evidence. J Public Health (Oxf) 33 2 212 222, doi: 10.1093/pubmed/fdq068 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lobdell DT, Jagai JS, Rappazzo K, Messer LC. 2011. Data sources for an environmental quality index: availability, quality, and utility. Am J Public Health 101(suppl 1) S277 S285, doi: 10.2105/AJPH.2011.300184 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- McCabe JG, Burke TA. 2016. Reducing risk by acting on climate. Health Secur 14 2 43 46, doi: 10.1089/hs.2016.0006 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Morrison KD, Kolden CA. 2015. Modeling the impacts of wildfire on runoff and pollutant transport from coastal watersheds to the nearshore environment. J Environ Manage 151 113 123, doi: 10.1016/j.jenvman.2014.12.025 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Murphy K, Heery B, Sullivan T, Zhang D, Paludetti L, Lau KT, et al. 2014. A low-cost autonomous optical sensor for water quality monitoring. Talanta 132 520 527, doi: 10.1016/j.talanta.2014.09.045 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- NRC (National Research Council) Washington, DC: National Academies Press; 1983. Risk Assessment in the Federal Government: Managing the Process . https://www.nap.edu/catalog/366/risk-assessment-in-the-federal-government-managing-the-process [accessed 20 December 2016] [ PubMed ] [ Google Scholar ]
- NRC. Washington, DC: National Academies Press; 2007. Models in Environmental Regulatory Decision Making . https://www.nap.edu/catalog/11972/models-in-environmental-regulatory-decision-making [accessed 20 December 2016] [ Google Scholar ]
- NRC. Washington, DC: National Academies Press; 2011. Improving Health in the United States : The Role of Health Impact Assessment . https://www.nap.edu/catalog/13229/improving-health-in-the-united-states-the-role-of-health [accessed 20 December 2016] [ PubMed ] [ Google Scholar ]
- NRC (National Research Council) Washington, DC: National Academies Press; 2012. Science for Environmental Protection : The Road Ahead . https://www.nap.edu/catalog/13510/science-for-environmental-protection-the-road-ahead [accessed 20 December 2016] [ Google Scholar ]
- Phillips D, Boumans R, Victery W, Fontaine T. Washington DC: A Community on Ecosystem Services, December 8-12, 2014; 2014. Climate change effects on ecosystem services and human health. https://cfpub.epa.gov/si/si_public_record_report.cfm?dirEntryId=299092&fed_org_id=858&SIType=PR&TIMSType=&showCriteria=0&address=nheerl/pubs.html&view=citation&sortBy=pubDateYear&count=100&dateBeginPublishedPresented=01/01/2010 [accessed 19 May 2016] [ Google Scholar ]
- Pickard BR, Daniel J, Mehaffey M, Jackson LE, Neale A. 2015. EnviroAtlas: a new geospatial tool to foster ecosystem services science and resource management. Ecosyst Serv 14 45 55, doi: 10.1016/j.ecoser.2015.04.005 [ CrossRef ] [ Google Scholar ]
- Powers CM, Dana G, Gillespie P, Gwinn MR, Hendren CO, Long TC, et al. 2012. Comprehensive environmental assessment: a meta-assessment approach. Environ Sci Technol 46 17 9202 9208, doi: 10.1021/es3023072 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Ramsey K, Bell A. Cityscape: J Policy Dev Res 16(2):145–162; 2014. The Smart Location Database: a nationwide data resource characterizing the built environment and destination accessibility at the neighborhood scale. https://www.huduser.gov/portal/periodicals/cityscpe/vol16num2/ch11.pdf [accessed 20 December 2016] [ Google Scholar ]
- Rappold AG, Stone SL, Cascio WE, Neas LM, Kilaru VJ, Carraway MS, et al. 2011. Peat bog wildfire smoke exposure in rural North Carolina is associated with cardiopulmonary emergency department visits assessed through syndromic surveillance. Environ Health Perspect 119 10 1415 1420, doi: 10.1289/ehp.1003206 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Rehr AP, Small MJ, Fischbeck PS, Bradley P, Fisher WS. 2014. The role of scientific studies in building consensus in environmental decision making: a coral reef example. Environ Syst Decis 34 1 60 87, doi: 10.1007/s10669-014-9491-8 [ CrossRef ] [ Google Scholar ]
- Reis S, Morris G, Fleming LE, Beck S, Taylor T, White M, et al. 2013. Integrating health and environmental impact analysis. Public Health 129 10 1383 1389, doi: 10.1016/j.puhe.2013.07.006 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Rittel HWJ, Webber MM. 1973. Dilemmas in a general theory of planning. Policy Sci 4 2 155 169, doi: 10.1007/BF01405730 [ CrossRef ] [ Google Scholar ]
- Sedlak D. 2016. Fool me once. Environ Sci Technol 50 15 7937 7938, doi: 10.1021/acs.est.6b03367 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Snyder EG, Watkins TH, Solomon PA, Thoma ED, Williams RW, Hagler GS, et al. 2013. The changing paradigm of air pollution monitoring. Environ Sci Technol 47 20 11369 11377, doi: 10.1021/es4022602 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Stahl CH. 2014. Out of the Land of Oz: the importance of tackling wicked environmental problems without taming them. Environ Syst Decis 34 473 477, doi: 10.1007/s10669-014-9522-5 [ CrossRef ] [ Google Scholar ]
- Suter GW., II Developing conceptual models for complex ecological risk assessments. Human Ecoll Risk Assess. 1999; 5 (2):375–396. [ Google Scholar ]
- Suter GW II. Boca Raton, FL: CRC Press; 1993. Ecological Risk Assessment . [ Google Scholar ]
- Tulve NS, Ruiz JDC, Lichtveld K, Darney SP, Quackenboss JJ. 2016. Development of a conceptual framework depicting a child’s total (built, natural, social) environment in order to optimize health and well-being. J Environ Health Sci 2 2 1 8, doi: 10.15436/2378-6841.16.1121 [ CrossRef ] [ Google Scholar ]
- United Nations. Paris Agreement. 2015 http://unfccc.int/files/essential_background/convention/application/pdf/english_paris_agreement.pdf [accessed 13 July 2016]
- U.S. EPA (U.S. Environmental Protection Agency) AirNow. How Smoke from Fires Can Affect Your Health. EPA-452/F-02-002. Research Triangle Park, NC. 2003 https://www3.epa.gov/airnow/smoke/Smoke2003final.pdf [accessed 6 June 2016]
- U.S. EPA. Washington, DC: U.S. EPA; 2006. EPA Science Inventory. Life Cycle Assessment: Principals and Practice. EPA/600/R-06/060. https://cfpub.epa.gov/si/si_public_record_report.cfm?dirEntryId=155087 [accessed 20 December 2016] [ Google Scholar ]
- U.S. EPA. Our Nation’s Air: Status and Trends Through 2010. Office of Air and Radiation. EPA-454/R-12-001. 2012 https://www3.epa.gov/airtrends/2011/report/fullreport.pdf [accessed 6 June 2016]
- U.S. EPA. Environmental Quality Index: Overview Report. EPA 600/R-14/305. 2014a https://cfpub.epa.gov/si/si_public_record_report.cfm?dirEntryId=316570 [accessed 20 December 2016]
- U.S. EPA. Framework for Human Health Risk Assessment to Inform Decision Making. EPA/100/R-14/001. 2014b https://www.epa.gov/sites/production/files/2014-12/documents/hhra-framework-final-2014.pdf [accessed 6 June 2016]
- U.S. EPA. Air, Climate, and Energy: Strategic Research Action Plan, 2016–2019. EPA 601/K-15/005. 2015a https://www.epa.gov/sites/production/files/2015-10/documents/strap_2016_ace_508.pdf [accessed 14 July 2016]
- U.S. EPA. Climate Change in the United States: Benefits of Global Action. EPA 430-R-15-001. 2015b https://www.epa.gov/sites/production/files/2015-06/documents/cirareport.pdf [accessed 6 June 2016]
- U.S. EPA. EPA’s Report on the Environment. 2015c http://cfpub.epa.gov/roe/ [accessed 13 May 2016]
- U.S. EPA. Health Impact Assessment (HIA) & EnviroAtlas: Integrating Ecosystem Services into the Decision-Making Process. EPA/600/RR-15/128. 2015d https://www.epa.gov/sites/production/files/2015-08/documents/hia_guide_final_pdf.pdf [accessed 6 June 2016]
- White House. Long-term Drought Resilience: Federal Action Plan of the National Drought Resilience Partnership. 2016 https://www.whitehouse.gov/sites/default/files/docs/drought_resilience_action_plan_2016_final.pdf [accessed 13 July 2016]
- Yeardley RB Jr, Dyson B, Tenbrink M. Washington, DC: U.S. EPA. EPA/600/F-11/023, 2011; 2011. EPA Growing DASEES (Decision Analysis for a Sustainable Environment, Economy & Society) – To Aid in Making Decisions on Complex Environmental Issues. https://cfpub.epa.gov/si/si_public_record_report.cfm?dirEntryId=238232 [accessed 20 December 2016] [ Google Scholar ]
- Yee SH, Carriger JF, Bradley P, Fisher WS, Dyson B. 2015. Developing scientific information to support decisions for sustainable coral reef ecosystem services. Ecol Econ 115 39 50, doi: 10.1016/j.ecolecon.2014.02.016 [ CrossRef ] [ Google Scholar ]
- Zartarian VG, Schultz BD, Barzyk TM, Smuts MB, Hammond DM, Medina-Vera M, et al. 2011. The Environmental Protection Agency’s Community-Focused Exposure and Risk Screening Tool (C-FERST) and its potential use for environmental justice efforts. Am J Public Health 101(suppl 1) S286 S294, doi: 10.2105/AJPH.2010.300087 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
ORIGINAL RESEARCH article
Perceptions of local environmental issues and the relevance of climate change in nepal's terai: perspectives from two communities.

- 1 Tyndall Centre for Climate Change Research, School of Psychology, Cardiff University, Cardiff, United Kingdom
- 2 Research Department, Institute for Social and Environmental Research Nepal (ISER-N), Bharatpur, Nepal
The direct and indirect impacts of global climate change entail serious consequences for global biophysical and social systems, including the health, well-being and sustainability of communities. These impacts are especially serious for vulnerable groups in economically developing societies. While climate change is a global phenomenon, it is at the local level that impacts are most felt, and from where responses to climate change are enacted. It is increasingly urgent that communities possess the capacity to respond to climate change, now and in the future. Community representations of climate-relevant issues are critical to underpinning responses. Environmental representations do not directly reflect actual physical conditions but are interpreted through social and cultural layers of understanding that shape environmental issues. This paper investigates environmental and climate-relevant perceptions within two communities in the Terai region of Nepal; the city of Bharatpur and the village of Kumroj in Chitwan Province. Following mixed findings on levels of climate change awareness in Nepal, we set out to explore perspectives on the environment and climate change awareness by conducting 30 qualitative interviews with local people. The study found that issues linked to sanitation and cleanliness were most important in both communities, while reports of temperature and weather changes were less common and typically linked to local causes rather than climate change. Imagined futures were also closely related to current environmental issues affecting communities and did not discuss climate change, though temperature and weather changes were anticipated. However, when talk of climate change was deliberately elicited, participants displayed their awareness, though this was rarely linked to local conditions. We conclude that, in light of other pressing local issues, climate change is yet to penetrate the environmental representations of some communities and there is a need to address the disconnect between local issues and global climate change. Making climate change relevant at the local level by connecting to salient local issues and co-benefits comprises an important step in bridging the gap between more global awareness and its relevance more locally, particularly for communities at risk.
Introduction
Climate change impacts are set to profoundly change global ecological and social systems, bringing about fundamental changes to human behavior ( Evans, 2019 ). The complexity of global climate systems makes it difficult to accurately predict the nature of climate change impacts, though a degree of certainty rests in knowing that fundamental lifestyle shifts commensurate with the scale of climate change will be required if we are to limit the global temperature increase to 1.5°C by 2100 ( Rogelj et al., 2018 ). In addition to average temperature increase, societies also face increases in the frequency of extreme weather events, air pollution and sea level rise, posing an array of physical threats to human health and well-being, both directly and indirectly ( Watts et al., 2018 ).
Consequently, the impacts of sudden natural disasters (such as shock, emotional distress and post-traumatic stress), and cumulative stresses over time (for example, changes to livelihoods, economic opportunities and social support) from climate change carry serious psychological impacts for those affected ( Clayton et al., 2015 ). These impacts are especially pronounced for citizens living in economically developing countries, particularly for those within developing countries who rely on natural resources to sustain their livelihoods ( Aryal et al., 2014 ).
In addition to continued mitigation, societies will be required to adapt to current and future environmental change. Adaptation in this context refers to a community's capacity to deal with changes, reduce vulnerability to risks, and improve the well-being of communities ( Bhatta et al., 2015 ). While action on climate change maintains a crucial global imperative ( Gupta, 2010 ), variability in environmental impacts and sociocultural differences at the local level also highlight the need to better understand the contexts within which responses to climate-relevant issues occur ( Adger, 2003 ). While global environmental issues such climate change are constructed in top–down ways through scientific, political and other cultural narratives ( Adger et al., 2013 ), they are also blended with and filtered through more vernacular, localized forms of understanding ( Byg and Salick, 2009 ).
In this paper we investigate environmental and climate-relevant perceptions in the context of two rural communities in the Terai (lowland) region of Nepal. Nepal is an economically developing country in South Asia that faces serious impacts from climate change including a predicted temperature increase of 2.8°C by 2060 and up to 4°C by 2090, snowpack melt, glacier retreat, shifting climatic zones, increased extreme weather events, increased periods of drought and erratic precipitation ( Becken et al., 2013 ). In a country where agriculture is the principle industry for 80% of citizens ( Paudel et al., 2019 ) and widespread poverty exists, many of Nepal's citizens are precariously positioned by climate change threats ( Leichenko and Silva, 2014 ).
Following Smit and Wandel (2006) , we take a bottom-up approach to environmental and climate-relevant perceptions at the community level. We discuss the findings from 30 qualitative interviews with community members, focusing on the role of subjective environmental perceptions relating to current and future environmental issues, including community perspectives on climate change, with a focus on the impacts for human well-being. While scientific measurement of ecological impacts provides the foundation for mitigation and adaptation, community perceptions are also critical to ensuring that policy interventions fit community understandings and avoid being misinterpreted or rejected by the community ( Leiserowitz, 2007 ). The Inter-Governmental Panel on Climate Change (IPCC) has also stipulated that local knowledge should be used to inform climate adaptation planning ( Carter, 2019 ).
In addition to comprising physical phenomena, environmental issues, including climate change, comprise important social, cultural, and political dimensions that mediate perceptions of the physical ( Hulme, 2009 ; Whitmarsh, 2011 ). These are both facilitated and constrained by cultural knowledge, expressed through social norms, practices, institutional structures and prescribed roles and ways of living. The extent to which climate-relevant communications, interventions and policy are received, understood and enacted by local communities therefore depends on the degree to which top-down standardized scientific narratives converge with, or diverge from the micro-contexts of localized forms of knowledge ( Zinn, 2004 ). Culturally-filtered observations and experiences of environmental conditions are a crucial way in which citizens understand environmental conditions and processes of change ( Bickerstaff, 2004 ; Hulme, 2012 ). Human cognitive biases also influence and distort environmental perceptions. For example, more unusual or memorable weather events tend to exert a stronger influence on perceptions ( Trenberth et al., 2015 ).
Furthermore, perspectives of global climate change may be constrained due to being beyond human perceptual capacity. This means that other locally-salient issues may be perceived as more immediate ( Weber, 2010 ). While people may attribute extreme weather events to global climate change, such interpretations depend on culturally-available narratives that construct such issues, whereas physical climate change is, arguably, only discernible over long time periods. Essentially, a single event cannot unequivocally be attributed directly to climate change, though an individual may or may interpret it as such, depending on their perspective ( Hulme, 2014 ). Similarly, interpretations of local environmental conditions have been found to influence more global climate-relevant understandings. For example, in one study, local perceptions of deforestation, urbanization and air pollution framed explanations of climate change ( Maharjan and Joshi, 2012 ). This suggests that people look for proximate and visible causes in the absence of wider understanding.
Nonetheless, studies have demonstrated evidence that communities who are more in touch with their surroundings are able to accurately detect environmental changes, such as seasonal temperature and weather fluctuations ( Gurung, 1989 ; Tiwari et al., 2010 ; Poudel and Duex, 2017 ; Uprety et al., 2017 ). Other research has found that while community members are accurate in their perceptions of some seasonal and weather-related changes, they are less accurate at perceiving others ( Myers et al., 2013 ). Environmental impacts also affect different groups within a country or region differently, and not always uniformly ( Gentle et al., 2014 ) and may even be experienced differently by different members of the same community ( Maharjan and Joshi, 2012 ).
Climate change awareness has been reported to be higher in economically developed countries than in economically developing nations, a pattern also found for countries within Asia ( Maharjan and Joshi, 2012 ). Other research has found educational attainment to be the strongest predictor of awareness ( Lee et al., 2015 ). Cultural differences are also evident in terms of climate change risk perceptions; in Latin America and Europe, comprehension of the anthropogenic origin of climate change has been found to be the strongest predictor, while in several Asian and African countries, perception of temperature increase locally was most influential ( Lee et al., 2015 ). Perceptions of temperature and weather change are widespread. Savo et al. (2016) conducted a meta-analysis of 10,660 change observations reported across 2,230 localities in 137 countries, which showed increases in temperature, and changes in seasons and rainfall patterns in 70% of localities in 122 countries.
Nepal is particularly susceptible to climate change, with change in the Himalaya accelerating beyond the global average ( Zomer et al., 2014 ). In the Terai agriculture is the principle economic activity, with around 80% of the population dependent on farming for their livelihoods. Therefore, climate change carries significant risks for the economy, which indirectly affect food production and security. The situation is exacerbated by widespread poverty; in 2010 over 25% of the population subsisted below the national poverty line ( Adhikari, 2018 ). Poorer groups within society are more likely to be exposed to climate stresses and possess fewer resources to adapt ( Gentle et al., 2014 ; Leichenko and Silva, 2014 ). Nepal is divided into three ecological regions comprising the Terai (lowland), hill and mountain regions, each of which is characterized by different ecological and climatic conditions. The Terai forms a fertile plain located in the south of the country where the majority of food production takes place, and is also the most densely populated region ( Paudel, 2012 ). Of relevance within Nepal, food shortages due to seasonal changes, infestations of new crop pests and a decline in soil productivity have been recorded ( Paudel, 2012 ).
Public awareness is seen as a major limitation to climate change adaptation within Nepal ( Withana and Auch, 2014 ). While some studies have found high levels of climate change awareness amongst Nepalese citizens ( Becken et al., 2013 ), other research has found awareness to be low ( Gallup, 2009 ). In a cross-national study of 5,060 households, Tanner et al. (2018) report that climate change awareness was low (<50% were aware of the phenomenon even if they had been aware of changes in the weather). Awareness in urban areas was lower than in rural areas (56% v 46%), and very low in mountain areas (63% had not heard of climate change). There were also significant proportions of citizens who did not perceive that the climate was changing. Maharjan and Joshi (2012) report that among the Chepang community only 11.8% of respondents had heard of climate change; of those, only 4.8% were able to relate the phenomenon to changes in weather patterns, temperature, rainfall, wind, floods, landslides, and environmental change.
Research on community perceptions of environmental and climate-relevant change in Nepal has recorded perceptions of warmer summers ( Tiwari et al., 2010 ; Uprety et al., 2017 ); milder winters ( Dahal, 2005 ; Maharjan and Joshi, 2012 ; Becken et al., 2013 ); more erratic rainfall ( Chapagain et al., 2009 ; Paudel, 2012 ; Becken et al., 2013 ; Devkota and Bhattarai, 2018 ); increased periods of drought ( Tanner et al., 2018 ); and more frequent foggy days ( Shrestha et al., 2018 ). However, community perceptions are not consensual. Maharjan and Joshi (2012) report that while 47.5% believed that summers were getting warmer, nearly 10% reported that summers were becoming cooler and 38% perceived no change. In addition, 21% believed that winters were getting colder while 22% believed that winters were becoming milder. Furthermore, 37% believed that there was less rain overall, while 13–17% perceived no change in rainfall. They attribute this to differences in “visual salience”; whereby rainfall is more conspicuous and facilitates perception, whereas temperature change is less directly observable.
With specific reference to the Terai region, Maharjan et al. (2011) interviewed farmers in the Western Terai, with 90% of respondents reporting increases in climate-related risks (erratic rainfall, flooding, droughts, riverbank erosion, windstorms, hailstorms, insect infestations). Tiwari et al. (2010) surveyed Terai communities in which over 75% of participants reported delayed onset of the monsoon and changes in flowering and fruiting time for some plant species. Meanwhile, Manandhar et al. (2011) found that more than two-thirds of farmers in the Terai claimed to have personally experienced evidence of climatic change.
As a result of perceived environmental change in the Terai, and in other regions livelihoods and lifestyles are adapting to changing conditions. Khanal et al. (2018) surveyed farming households in Nepal to gauge adaptation practices across the three ecological regions of Nepal, reporting that 91% of households had adopted at least one practice to minimize impacts of climate change. Adaptation may be more anticipatory or reactive and distinguished by duration, scale of implementation (i.e., more local or more widespread) and focus (e.g., behavioral, institutional, economic, technological, informational) ( Smit et al., 2000 ). In a study of climate change adaptation in the rural hill region of Nepal, Gentle et al. (2018) examined household responses in four villages. Adaptive responses to climate change in rural communities were found to be less coordinated and more reactive and unplanned rather than anticipated and coordinated.
Changes to agricultural practices constitute a primary focal point for adaptation and change. These have included changes in the times crops are sown and harvested ( Maharjan et al., 2011 ), switching to more climate resilient crop varieties and tree and plant species ( Maharjan et al., 2011 ; Paudel, 2016 ; Gahatraj et al., 2018 ), as well as increased use of pesticides, and income diversification ( Gentle et al., 2018 ). Climate change is also perceived as benefiting some crop species ( Rawal and Bharti, 2015 ). For example, mangos are being grown at higher altitudes than was possible in the past ( Chapagain et al., 2009 ).
Within villages, water practices were changing to conserve water resources ( Tiwari et al., 2010 ), and changes to diets have also been identified ( Tanner et al., 2018 ), with less rice being consumed due to the effects of climate on rice productivity ( Maharjan and Joshi, 2013 ). Two-story houses are increasingly being constructed for food storage and as refuge from flooding ( Maharjan and Joshi, 2013 ), while buildings are being oriented to withstand windstorms, incorporating single rather than double doors ( Maharjan and Joshi, 2013 ). Seasonal migration and resettlement becoming more common ( Prasain, 2018 ). People are also reported to be planting more trees and grasses on their own land as well as on communal land to protect communities from flooding, wind and dust ( Tiwari et al., 2010 ; Maharjan et al., 2017 ). Withana and Auch (2014) report that afforestation is viewed as the most effective climate change adaptation strategy by communities.
In summary, perceptions of environmental conditions are key to informing behavior, including the need to adapt to a changing climate. In the context of Nepal, adaptation is particularly salient and it is critical that communities respond to environmental risks in ways that ensure the well-being and futurity of those communities. Given that studies of climate-relevant perceptions have reported mixed findings in terms of awareness, we seek to clarify how Nepalese communities view environmental issues now and in the future. Such perceptions act as important indicators of how local communities make sense of what is happening in their surroundings.
Following our review of the literature, the following questions guide the study approach:
• How do communities in Nepal's Terai perceive their environment?
• How do they see that environment changing in the future?
• To what degree are local communities aware of climate change?
• What is the relative importance of climate change compared to other issues environmental affecting the community?
Materials and Methods
The following subsections describe the study design and procedure. Broadly, this comprised a qualitative approach using semi-structured interviews with residents in two communities in the Terai region of Nepal. Thirty interviews were conducted in total. 15 interviews were conducted with residents of the village of Kumroj, a small rural community bordering Chitwan National Park. Another 15 interviews were conducted with residents of Bharatpur, an urban community approximately 12 miles (20 km) away. For each group, we were interested in gauging perceptions of salient environmental issues, including climate change. We selected two different communities to explore the degree to which locally salient issues varied and informed discussions. Before commencing fieldwork, the study design was scrutinized and approved by the Research Ethics Committee in the School of Psychology at Cardiff University.
Participants
Fieldwork was conducted in January and February 2016. A purposive sampling strategy ( Silverman, 2015 ) was used to try to generate a range of different sociodemographic profiles within each community in terms of age, gender and ethnicity. All participants were aged 18+ and resided in either Bharatpur or Kumroj, both in the Chitwan district. Bharatpur has a population of 280,000 and is one of the largest and fastest growing cities in Nepal. While it is home to a number of small-scale processing industries, agriculture remains the biggest industry. Kumroj is a small town with a population of 8,000. Kumroj borders Chitwan National Park, the first National Park created in Nepal (in 1973). In recent years in-migration has increased pressure on land for settlement and agriculture. Increasing tourism has put additional pressure on the landscape. A number of community development initiatives have attempted to confer Kumroj as an ecological exemplar, with the creation of a community forest initiative and grant funding to encourage domestic biogas installation to reduce deforestation, launched on World Environment Day, 2013. Around 80% of households within Kumroj have installed bio-gas converters to reduce reliance on the forest for fuel.
To arrange fieldwork with local people in Kumroj, we contacted the offices of the World Wildlife Fund for Nature (WWF) in Kathmandu, who had been involved in community development projects in Kumroj. Through WWF, we were able to negotiate access through local community leaders who helped us to recruit participants. Prior to our arrival, the study was advertised by word-of-mouth by community leaders, who identified potential members of the community willing to be interviewed. Extra care had to be taken in gaining access to participants, establishing contact and opening communicative spaces with the community, which could be damaged if pushed too quickly ( Wicks and Reason, 2009 ). The study was promoted as a “ lifestyle and behavior ” project and avoided making reference to the environment, as we wished to avoid recruiting only those members of the community whose motivations and values were strongly pro-environmental. At recruitment, a brief screening procedure was applied; individuals were screened to ensure that they were 18+ and aware of the broad purpose of the study and what would be required in terms of participation. We also purposefully recruited individuals to ensure that we had a roughly equal split in terms of gender, as well as diversity in terms of age, ethnicity, occupation, and income. See Table 1 for subsample demographics.
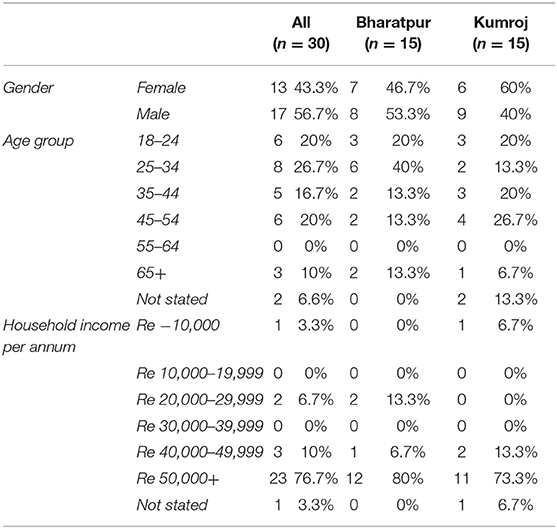
Table 1 . Subsample demographics.
To recruit our Bharatpur subsample, we collaborated with the Institute for Social and Environmental Research Nepal (ISER-N). ISER-N is a research and development institute that conducts applied research to inform policy-making and effective sustainable development initiatives across local communities. Using a similar method to the above, ISER-N acted as our guide and point of access to the local community and advertised and recruited a subsample of local people who had expressed an interest in discussing their lifestyles and behaviors.
Once participants had been identified, screened, and given further information about the study, they were invited to take part in an interview to discuss aspects of their day-to-day lifestyles and behaviors with the research team. Interviews were scheduled to take approximately one-and-a-half hours, but varied from 45 min to 2 h. A semi-structured interview method ( Galletta, 2013 ) was chosen in which a standard set of questions was covered while also allowing flexibility for follow-up questions and exploration of other issues of relevance to participants. Such flexibility is an advantage in cross-cultural settings as this allows for greater exploration of cultural factors underpinning issues of interest ( McIntosh and Morse, 2015 ; Hagaman and Wutich, 2017 ). All participants were required to give written informed consent prior to participation.
Questions in the interview protocol sought to contextualize environmental perspectives within people's wider everyday lives as far as possible. Questions broadly covered perceptions of the environment and the importance of environmental issues environmental problems (including climate change), engagement in environmentally-friendly behavior, the character, motivations for and consequences of behaviors, and comparisons with others in terms of acting in environmentally-friendly ways (see Supplementary Information ).
The majority of interviews took place at participants' homes. Discussions took place on seats or woven mats in the front yards of houses rather than inside the building itself. A small number of interviews were conducted in other locations, such as a local café, or community building in the case where the home could not be used. We relied heavily on our collaborators and local community leaders to manage interview arrangements in line with our concerns about accessing members of an unfamiliar culture and wishing not to transgress social boundaries. Because people's yards are the area of the home where a lot of day-to-day interaction takes place, providing socially appropriate spaces for interaction.
One of the disadvantages of holding interviews outside was that on some occasions the research team's presence would attract the curiosity of other family members, neighbors and other locals. The sudden presence of others could occasionally alter the dynamic of the interview interaction, particularly if the others who were present began talking or offering their own perspectives. On one or two occasions the research team had to ask bystanders to limit their contribution so as to allow the participant to speak. To a cultural outsider this would appear potentially problematic and non-conducive to an appropriate interview context, which led us to consider this and other ethical considerations in conducting interview research in different cultures.
Ethical Considerations in Conducting Interviews in Different Cultures
Researchers typically assume that the communities in which they work will be aware of the concept of research and its value, though for many communities research is something abstract, distanced and difficult to make sense of in relation to their ordinary lived experience. This came across clearly in working with each subsample. In Bharatpur, participants were familiar with ISER-N and, owing to participating in other cross-cultural research, were more comfortable with the researcher's presence than participants in Kumroj, who had not been so exposed to researchers and the research process. Further to this, bridging communicative spaces is not confined merely to issues of translation and word equivalence, but of more conceptual differences in terms of the ways that different cultures define reality and categorize their experience ( Fong, 2012 ). Language and culture are woven together in ways that require not only the translation of speech, but the translation of cultural meanings that are often concealed from those outside of that culture. In designing the interview protocol, we worked closely with our collaborators not only to ensure that questions were understandable, but that any cultural assumptions (for example, about the lifestyles, values, and practices of the community) were identified and addressed appropriately. All interview materials were double-translated.
Qualitative methods including interviews, also carry particular ethical implications in terms of power imbalance, where the discussion is primarily directed by the researcher ( King et al., 2018 ). Assumptions about the identity of the western researcher (typically white, middle-class, and educated) on the part of the research participant construct interactional dynamics before a word has been spoken. Similarly, the reflexive researcher will not only consider how their own identity might influence communication, but how their assumptions about the community they are researching enter into framing interactions. While researchers may seek to embark on research practices that are non-exploitative and non-oppressive, researchers are nonetheless complicit in systems of oppression and should be aware of their own privileges.
The interview team comprised a male researcher (lead author) and a female translator to minimize any gender imbalance that might affect trust and participant disclosure, especially for female participants ( Campbell and Wasco, 2000 ; Sikes, 2018 ). The translator also played an active role in facilitating each interview, asking additional questions and clarifying understanding, as opposed to simply translating questions and responses. It was felt that a combination of cultural insider and cultural outsider benefited the discussion; while the former helped to increase trust and disclosure, the latter encouraged more detailed exploration of issues that might otherwise be taken for granted by those familiar with those issues ( Dwyer and Buckle, 2009 ).
Conducting qualitative fieldwork in collaboration with translators can also compromise the quality and accuracy of the material generated. In an interview context, the translator adds an additional layer to the interaction. For example, the translator is likely to be more acquainted with the cultural nuances of the interaction than the researcher. Therefore, both the researcher and translator can affect the fieldwork process, as well as disrupting the flow of talk to allow for translation ( Van Teijlingen et al., 2011 ). When fully transcribed, interviews can also show disparity between participant responses and translated responses. van Teijlingen et al. suggest that a way round this is to allow the translator to conduct the interview and only relay main points to the researcher, though this can be impractical, as well as excluding the researcher.
Prior to the interviews, considerable time was spent in developing and pre-testing interview questions. After constructing an initial set of interview questions in English, these were double-translated and then reviewed by our collaborators in Nepal. This was invaluable in not only identifying significant weaknesses in conceptual equivalence between Nepali and English versions of the questions ( Larkin et al., 2007 ), but also in highlighting researchers' cultural assumptions inherent in questions relating to everyday life in “other” places. That is, while a translated question may be conceptually equivalent to the original, it still may not be understandable in another culture (e.g., where researchers from one culture assume that all participants in another culture will have the same access to resources, such as running water). Even when all care is taken with translation, translators may be unfamiliar with a particular geographical region or cultural group. Therefore, it is recommended that questions are pre-tested in the specific cultural contexts in which they will be used.
With reference to interview locations, our decision to hold interviews outside and not in a more private location was primarily guided by social conventions as well as pragmatism, though we acknowledge the active influence of the nature of the space within which such interactions take place ( Gagnon et al., 2015 ). As mentioned at the end of the previous section, on occasion others were present at interviews in ways that influenced participant responses and could have constrained disclosure or breached informal assumptions about confidentiality (though interview questions were not considered to cover personally sensitive topics). Conversely, in discussing lifestyle and behavior issues, the home sometimes served as an exemplar in which participants described their activities in the context of the physical surroundings, which enhanced disclosure. In addition, conducting interviews in familiar environments can reduce the power imbalance between researcher and research participant ( Gagnon et al., 2015 ).
Ethical considerations do not end at the point at which the interview concludes but influence ongoing reflections following the interview (such as translation, analysis, writing-up and dissemination) ( Hoover et al., 2018 ). Acknowledging that translation imposes an additional level of interpretation on the spoken word ( Caretta, 2015 ), we have tried insofar as possible to contextualize accounts based on participants' direct speech rather than translators' interpretations of what was said. At the end of each interview, participants were provided with a verbal and written debrief in Nepali, in which they were given the opportunity to get in touch with the research team through appointed members of the local community and in-country collaborators should they have any further questions or concerns once participation had ended.
Analytic Approach
All interviews were digitally audio-recorded and translated and transcribed at ISER-N. Written field notes were also taken throughout each interview relating to points of interest and things that might not be captured by the recorder. An “ in-interview ” system of translation was used whereby questions and responses were translated between English and Nepali by the translator. This method of translation was primarily used to aid communication within the interview itself. When the interview recordings were translated, the translators re-translated participants' responses, which appear alongside the in-interview translations in the transcripts. This was done as the task of translating what at times were lengthy utterances in the moment, could have led to omissions and gaps, whereas in translating participant responses from the recordings utterances could be replayed and listened to repeatedly for clarity, thus better capturing what was said.
An episodic narrative approach was used as an analytic framework by which to explore participants' accounts of environmentally-friendly perceptions and behaviors. This approach treats perceptions and experiences as lived narratives situated within the wider society and culture ( Flick, 2000 ; Jovchelovitch and Bauer, 2000 ). Narrative interviewing is interested in eliciting particular episodes or features of participants' lives and how they make sense of the world as embodied, culturally and spatially situated individuals ( Raulet-Croset and Borzeix, 2014 ). Interview audio files and transcripts were analyzed using NVivo 11, supplemented by written field notes.
Our analysis combined several methods, which we outline here. In line with the early stages of a grounded theory approach ( Timmermans and Tavory, 2012 ) we began by reading through transcripts to identify examples of talk that involved themes relating to health and well-being in the context of environmental issues. As much as possible, given inevitable researcher preconceptions and positions ( Caelli et al., 2003 ) we sought to identify general themes and provisional topics of interest, without imposing a predetermined framework. This manner of bottom-up or inductive analytic reading of the data allows for the broadest possible range of salient themes to be identified. Once we familiarized ourselves with the material through repeated readings, we then developed a system of codes to more precisely categorize these themes. In order to do so, we used a version of template analysis, which is suitable for identifying themes in research data that is commensurate with both essentialist and constructionist perspectives, and which enables a hybrid approach that utilizes both inductive and deductive techniques ( Brooks et al., 2015 ). Template analysis is a form of thematic analysis applied to qualitative data, that is sensitive both to emergent themes that are grounded in the data (i.e., not anticipated or predetermined by the researcher) as well as permitting predetermined codes or categories to be applied (i.e., in line with the researcher's interests and the existing literature). The coding framework was developed through an iterative process: through multiple readings of the research data and refinement of initial codes until further changes to the framework did not enhance it further. A further feature of template analysis is the development and application of a hierarchical coding approach, designed to shed light on the structure across the set of codes. In the case of the present study, this for example has led to higher-level codes such as “behavioral responses” beneath which we identify sub-codes such as “cleanliness” and “waste disposal.”
In the analysis that follows, we present extracts from interviews in both communities comprising perceptions of environmental issues. Where considering the themes identified within the data, we have illustrated this using a single typical extract and alluded to its occurrence in other participants' accounts within the text.
Community Perceptions of Current Environmental Conditions
We began by asking participants about the importance of environmental issues in their day-to-day lives and what the surrounding environment was like. Responses comprised both positive and negative evaluations of environmental conditions, though there was a greater range of issues forming the latter. To get some sense of the kinds of terms used to describe the local environment in each community, we created two word clouds using NVivo, which display the most frequently used words in discussing issues. The results of these are displayed in Figures 1 , 2 .

Figure 1 . Word cloud of the 75 most common words associated with present environmental conditions (Bharatpur participants).

Figure 2 . Word cloud of the 75 most common words associated with present environmental conditions (Kumroj participants).
Both communities used the same terms in discussing the environment, such as “ people ” and “ good .” In Bharatpur, “ better ” was also commonly used in talking about the environment, which may reflect the dominance of the issue of sanitation (see section Sanitation and Hygiene below). Negative words such as “ pollution,” “ smoke,” “ problem,” and “ dust” also came up relatively regularly, as did the word “ plastic .” Terms relating to hygiene and sanitation were also notable. These included “ cleanliness,” “ toilet ,” “ healthy,” and “ clean .” Meanwhile, in Kumroj, commonly used terms appeared congruent with the community's rural position. These included “ animals ,” “ jungle ,” “ wild ,” and “ forest .” Words such as “ polluted ,” “ concerned,” and “ worried” were also used. We now move on to discuss responses in more detail.
Sanitation and Hygiene
The primary way issue through which the environment was assessed in both communities, though particularly in Bharatpur, related to sanitation and the need to maintain a clean environment to reduce the risks of disease:
“ Previously, like ten to fifteen years ago people used to smoke, and there was open defecation everywhere, there weren't any toilets, so people used to get sick and the death rate also used to be very high, people used to be suffering by many kinds of disease, skin problems, allergies. Now currently almost every household has a toilet, and many organizations have been working on cleanliness. They have been providing various training and awareness programs regarding the clean environment. So now I would say, the environment is not so bad around here .” (Bharatpur, Interview A3).
In the above account, a positive assessment of environmental conditions is formulated by drawing a comparison between past and present sanitation and sanitary practices. Whereas, in the past, communities were affected by diseases resulting from unsanitary conditions, this had now changed, providing a positive indicator of the local environment as a whole.
In addition to health risks from open defecation, providing proper toilets in rural communities such as Kumroj also minimized other risks from wildlife, and the discomfort of adverse weather conditions:
“ If we don't have a toilet, then we may have to face many difficulties such as while going outside for toilet then we might get attacked from snake or when raining it would be hard to go the toilet. And if we openly defecate then it will pollute the environment and as result we may have to suffer from different diseases, so environment is the most important thing to survive for everyone and we can't imagine life without environment .” Kumroj, Interview B11).
For rural communities, development of sanitation was considered not only key to well-being, but also, implicitly, key to a good environment. Talk of sanitation in the context of evaluating the local environment also rested heavily on community awareness. What contributed to a lack of environmental quality in the past was not only that proper sanitation was unavailable, but that in the past, communities were less aware of the risks to health and well-being from poor sanitation. Risky sanitary practices were thus maintained as people did not know any better. In contrast, nowadays, communities were more aware of risks from inadequate sanitation and knew how to overcome issues such as contaminated drinking water. In this way, community awareness also contributed to positive judgements of environmental quality:
“ The e nvironment here is better in comparison to the past…These facilities didn't exist. There had been problems of drinking water taps. The same tap was used. It wasn't enough. In society, people had to drink water from wells. They had germs, smoke and dust .” (Bharatpur, Interview A10).
Similar to the accounts of the shift to a better environment through the development of toilet facilities and reduction in the practice of open defecation, an overall positive evaluation of the environment is constructed through comparisons of past and present. For many participants, issues of health, sanitation and hygiene formed the yardstick by which the overall environment was evaluated positively.
Waste and Pollution
While improvements in sanitation and hygiene across both communities provided a positive indicator of environmental quality, there was more ambivalence where participants discussed other issues indicative of environmental quality in their respective communities. For participants in both Bharatpur and Kumroj, distance from industrial development and proximity to green spaces were important factors associated with positive environmental assessments:
“ The environment around here is ok, there is no industry and factory so it is not that much polluted here and we are nearby jungle so we have greenery, yeah, it's good, it's fine .” (Kumroj, Interview B5).
As illustrated in the above account, environmental quality was implicitly understood as relating to human well-being, in terms of risks from pollution. Such a location for the community, close to the jungle and away from factories, led to evaluations that the environment was good. Conversely, accounts of pollution from other sources within the community itself, suggested a rather different environmental evaluation. At the same time as some participants positively evaluated the environment being relatively pollution-free, others constructed it as a polluted space due to the way that plastic waste was managed. The problem of plastic waste disposal came up most frequently in Bharatpur:
“… looking at increasing population, there can be very dangerous pollution. I feel that it will increase, yes, increasing. The use of plastics is increasing and there is no awareness regarding how to maintain cleanliness, how to save us from the problem. They have no such idea. Due to increasing population density, such symptoms are evident .” (Bharatpur, Interview A14).
Concerns about plastic waste were tied to other concerns about local population increase and the perception that there was a lack of awareness amongst the community in addressing the issue. Such accounts implied that there were no alternatives to using plastic, therefore the problem was in disposing of plastic waste that littered the environment and did not decompose. The main problem causing the pollution was not the presence of plastic waste, but the method used to manage and deal with waste plastic. This chiefly involved collecting the plastic and burning it in open fires. While this resolved the problem of plastic waste littering the community, participants were concerned that the smoke polluted the air and posed risks to health:
“ There is plastic around here and there. To dispose plastic, we need to burn it, and if we burn plastic it makes huge air pollution and affects people's health. The other day I argued with one person not to throw plastic. We must use firewood for cooking and because of that there is again smoke in the air, because of a lack of cooking gas. That's why it has been a very bad environment .” (Bharatpur; Interview A2).
In contrast to the previous extract constructing the local environment in positive ways as being relatively pollution-free, alternative perspectives such as the above led to very different evaluations of the local environment, with concomitant consequences for the health of the community. While the local community was aware of the contribution of existing informal plastic waste management practices to air pollution, it was nonetheless positioned as being powerless to change in ways that address air pollution as people are locked in to environmentally-damaging practices in order to manage waste and address basic needs. Similar to the need to use firewood for cooking due to shortages of cleaner alternatives, there were no alternatives and burning plastic waste was viewed as unavoidable. Essentially, such accounts lead to a very different evaluation of local environmental conditions.
Conversely, in Kumroj, a municipal system for collecting plastic waste had been in place for some time, therefore the community's method of dealing with plastic waste was not considered to threaten local environmental quality as much as problems such as poor sanitation:
“ People defecate wherever they want around the city area, there are toilets in here no toilets, so people openly defecated. So, I'm concerned about it…Otherwise, there is a facility to collect the waste from municipalities, the van comes and takes away waste. People collect the wastage plastic in sacks, then when the municipality van comes, then they take it away .” (Kumroj, Interview B6).
The account begins by constructing open defecation as the main issue threatening the environment in nearby Bharatpur, implying a negative assessment of the surroundings. This is contrasted with a more positive assessment where the speaker switches to talk about plastic waste management in Kumroj. Therefore, while plastic waste was a problem in both communities, in evaluating the local environment, the different ways in which plastic waste was managed were used to formulate contrasting assessments of environmental quality overall. These contrasting assessments may also connect to the wider importance of health and well-being, in which potential risks are offset by waste management practices in one community, but raised by plastic waste management practices in another.
Deforestation
While plastic waste did not negatively influence environmental assessments in Kumroj as it did in Bharatpur, there were, nonetheless, other issues affecting the community leading to negative environmental evaluations that were not reported in Bharatpur. For people in rural Kumroj, there was a closer felt connection to the neighboring forest as a source of environmental concerns. That is, forest conditions were more commonly invoked in environmental assessments by participants in Kumroj than in Bharatpur. The forest was seen as a valuable community resource, primarily as a source of firewood. Such talk occurred against a context of strikes and fuel shortages, further highlighting the importance of the forest as a source of firewood for local communities, which was being rapidly diminished due to increased demand:
“ We restored the forest with a lot of hard work. The strikes have already led to twenty-five percent of the forest to deforest and if this goes on, the forest will be completely deforested in a year or two. There is a new facility called biogas, we have that facility but, we have seventy-five percent biogas but people are poor and some bring the firewood from the forest, steal it and sell it… People have to survive. Having to die today and struggling for it tomorrow isn't going to work. If you have to survive today, you'll have to work for it today. And if they don't have any other way they'll go to the forest and steal the firewood .” (Kumroj, Interview B10).
Despite attempts to increase forest cover and reduce reliance on firewood by providing biogas converters within local communities, this did not address the wider problem of sustaining local people's livelihoods, which caused further deforestation and the potential loss of the forest altogether. From this perspective, the amount of forest cover formed an indicator of environmental quality. Furthermore, for participants in Kumroj, the environment was also judged based upon perceived changes in the amount of wildlife that could be observed locally:
“ I think the current environment is worse than the previous environment. I have noticed that the current environment is going down every day instead of going up. Because, previously when I used to go to the jungle I could see the wild animals very near, even sometimes outside of the jungle, but these days we have to go very deep into the jungle to search for the animals .” (Kumroj, Interview B14).
While the need for wood to sustain people's lives were commonly acknowledged within accounts of the pressures on forest resources in Kumroj, deforestation remained a significant concern.
Climate and Weather
While it was not foremost in terms of locally significant issues, participants in Bharatpur and Kumroj also referred to changes in climate and weather conditions in formulating their assessments of the local environment. These changes did not form the basis for positive evaluations of the local environment but appeared in negative or neutral assessments. Talk referred to a narrow range of changes. These mainly involved observations of temperature extremes in which summers were perceived to be increasingly hot, and winters increasingly cold. However, while these observations of climatic change were described causal factors were hardly mentioned. Furthermore, the phenomenon of global climate change was not spontaneously invoked in accounts:
“ I would say it's okay, so far Chitwan's environment is fine, although here is not much forest and plants. In winter it's very cold and summer is getting hotter .” (Bharatpur, Interview A6).
What appears initially as a positive assessment of the local environment is tempered by a perceived lack of forest cover and greenery in Bharatpur. In addition, the speaker adds the casual observation that winter and summer are increasingly subject to extreme temperatures, though no reason is offered as to why.
In addition to temperature changes, the other way in which the environment was judged was based on fluctuations in precipitation. In such accounts, there was consensus that rainfall was becoming more erratic and less predictable, and that rainfall overall was decreasing, including at the wettest times of the year. Again, no specific reasons were ventured as to why this was happening:
“ Yeah, I think sometimes, I think there's not enough or little rainfall during the rainy season .” (Bharatpur, Interview A1)
While changes in climate in terms of global averages cannot readily be detected by individuals ( Hulme, 2009 ), participants' observations appeared to reflect general climate trends. However, there was little concern expressed about temperature and precipitation changes, in comparison to other issues linked to health, cleanliness and well-being. Very occasionally, this type of issue was also linked to other perceived environmental problems. For example, one participant associated reductions in the amount of rain that fell to changes in forest cover:
“… we shouldn't be cutting down trees like we have been doing. We wouldn't get any rain if there weren't any trees .” (Kumroj, Interview B6).
The above account provides an isolated example of causation in relation to weather related changes. Even so, the role of climate change is not mentioned and rainfall change is attributed solely to the local problem of deforestation. While discussions of weather and climate were almost exclusively focused on the local area, an isolated reference was made to climate change in discussing the environment on a larger scale. One speaker spontaneously referred to broader patterns of global warming observed in changes beyond the local environment:
“… as you know because of the international global warming, now these days we have maximum cold, maximum hot, and impacts on ice and the change of snow fall trends…now there is very little snow fall in the mountains. If there is snow it melts so fast. These days we can see there are big storms, rainfall, everything has changed now. I think all the weather patterns have changed because of global warming. So, all those things make me concerned about the environment .” (Kumroj, Interview B13).
While an isolated example, the extract illustrates that climate change did arise in discussions of more local environmental conditions. Broader weather and temperature changes in Nepal corroborated observations at the local level, including temperature extremes and changes in rainfall.
In summary, assessments of the local environment were framed in different ways, leading to differences in the way that environment environmental conditions were evaluated. Assessments were framed based upon locally significant issues, which were both shared by, and individual to each community. Moreover, the most significant concerns were related to health and wellbeing. Next, we consider responses to the question of future environmental change.
Community Perceptions of Future Environmental Change
Following discussions over present environmental conditions, we then asked participants how the local environment might change in the future. Responses again comprised both positive and negative impressions, with a higher proportion of responses focused on the latter.
As previously, we created word clouds to get a sense of the sorts of terms that were used in imagining the future, and how these terms varied across communities. The results are shown in Figures 3 , 4 .
Figure 3 . Word cloud of the 75 most common words associated with future environmental conditions (Bharatpur participants).

Figure 4 . Word cloud of the 75 most common words associated with future environmental conditions (Kumroj participants).
Among participants in Bharatpur, the words “ waste ,” “ population,” and “ increasing ” came up most frequently in responses about future change. References to negative terms, such as “ pollution ” appeared less than in talk about existing conditions, though it appeared to be used relatively more frequently by participants in Kumroj. With reference to the latter community, the two most prominent words used in talking about the future were “ forest ” and “ people .” Other terms referred to environmental concerns looking to the future, including “ live ,”, “ less ,” “ important,” “ survive,” and “ disappear.” We now move on to discuss responses in more detail.
Future Deforestation
Across both communities, the most commonly reported issue in the future was that of population increase and its consequences, especially for those in Kumroj. As can be read from the analysis so far, population increase influenced environmental perceptions; and was something that was set to continue into the future. Population increase was not viewed in positive ways in either community. Instead, environmental impacts were predicted to increase as more people came to live in the Terai. Of these impacts, the pressure on local forests was most often mentioned. This tapped into the idea that the forest existed as a resource for local communities and that, as a resource, the forest was already being overused:
“ Well, um…I think, the population will increase, they may need more homes, more food, etcetera. For that, the increased population might destroy the green forest for their homes and for cultivating land. There might not be good management of the increased population. There may come disorder in the environment. There might be less wild animals, less trees and plants .” (Bharatpur, Interview A7).
In addition to providing raw materials in terms of firewood, as mentioned above, the need for land clearance to build settlements and provide food for newcomers compounded deforestation. If not well-managed, there were fears that this would eventually lead to the complete loss of the forest, both as a resource, and as a habitat for local flora and fauna. Such accounts appeared to be grounded in existing concerns about the exploitation of forest resources and served as a warning against continuing unchecked exploitation. In addition to its construction as a community resource and as a habitat for wildlife, in one or two discussions of future population increase, the forest was constructed as a safeguard against preventing other environmental impacts. For example, the forest protected the landscape from flooding and erosion:
“ Since the population and settlements are increasing, the forest is being cut down and people are settling in areas that were forest. More trees are being cut down to meet demand and brick factories are setting up and their chimneys pollute the air with lots of smoke. Because of less forest there could be floods and landslides, so this is the way the environment will be affected in future .” (Kumroj, Interview B11).
Further to the above, while participants were asked about environmental change in the future, discussions were typically grounded in perceptions of the present. Within the above extract, indications of future conditions linked to increased population and natural disasters are connected with conditions in the here and now, which are projected into an imagined future. It is assumed that present conditions will remain stable and consistent, with little expectation of change. As such, these accounts of the future highlight anxieties linked to present conditions, along with a sense of futility and helplessness that little will change. Conversely, issues such as sanitation did not really come up as future concerns, which likely reflects perceptions of sanitation improvements in the present, compared to the past.
Future Temperature Increases and Reduced Precipitation
Of relevance to climate change, rising temperatures, reduced rainfall and the loss of water resources also came up as potential future conditions locally. As found previously in accounts of present conditions, such talk tended to report conditions without elaborating on reasons as to what might contribute to causing them, or by offering opaque references to some unspoken (or non-understood) conditions or circumstances as “ having changed ”:
“ Yes, I think the environment might change. We even hear in the news that the heat or temperature has risen…we also have heard that because of some things the amount of rainfall has also decreased.” (Bharatpur, Interview A1).
The above narrative hints at climate change, though without any formal acknowledgment of the phenomenon. First of all, the speaker does not refer to direct experience of rising temperatures but formulates this information as something gathered from the media. Likewise, due to a set of unnamed causal factors labeled as “ some things ,” rainfall has also decreased, hinting at complexity. Furthermore, while the speaker begins by stating the belief that the environment could possibly change, the following discussion of climate-relevant change is grounded in changes that have already occurred, rather than changes that could happen in the future. As above, perceptions of future change are intimately connected to changes in the present. This is also confirmed in the next extract, in which a response to the question over future change is also constructed as an account of a present in which the environment locally had shifted from a state of stability to one of flux:
“ When it used to rain in Chure…that is in the mid hills, if we put some grains in the sun to dry then we wouldn't have time to collect them and bring them inside so quickly. The rain would have come, it used to rain quickly. But five to seven years after that there were floods and then other floods, and after that the climate started getting worse and worse. Nowadays what happens is we can see it raining in Chure but here is doesn't rain. So that is a very definite thing that I have noticed .” (Kumroj, Interview B13).
In this extract, rather than merely hearing about weather and temperature-related changes from secondary sources, evidence of environmental change could be found in the course of changes to practices that were arranged in line with previously stable and consistent weather patterns. As weather patterns had become less predictable, community practices had undergone changes, highlighting the impact of weather-related changes on the local community.
Local Community Perceptions of Climate Change
The previous sections have shown that while participants in both communities spoke about issues related to changes to temperature and weather, both now in the future, these issues were typically unelaborated beyond the reporting of changes when unelicited, and only rarely connected to wider global climate change. Yet these perceptions often paralleled broader climate change trends. In order to gauge the extent to which participants were aware of climate change, we then asked directly whether participants had heard of climate change or global warming.
Using NVivo, we began by mapping climate change themes from participants' accounts in both communities., which then formed basic nodes through which to understand the various ways in which participants in both communities talked about climate change. The conceptual map is shown in Figure 5 . We then looked at responses in more detail.
Figure 5 . Conceptual map of themes arising in participants' talk about climate change across both communities.
Changes in Temperature
Of the participants who were directly asked whether they had heard of climate change, only one or two had not, though nobody claimed to know more than a little. Responses were very similar across both communities. Nearly all participants in both communities referred to changes in temperature and/or weather locally. Extreme temperatures were the most commonly cited indicator, most often connected to hotter summers, but also less frequently linked to colder winters, as detailed above in the section on Climate and Weather. Generally, little was said beyond simply noticing change, though one important impact of temperature change in the Terai concerned the direct consequences for plant life:
“ Well…hmm…actually I don't know the reason of global warming. I have heard that the snow of the mountains is melting these days. If it melts it will be hotter. The vegetation will be dry and can't survive, I heard this. It means the temperature increase may affect every living thing on the earth .” (Bharatpur; Interview A7).
Such talk reflects the importance of agriculture for many communities in what is Nepal's primary agricultural region; while the direct impact on plants was highlighted, other impacts of temperature change were not. The speaker also claims to be unaware of the causes of global warming. However, they construct a link between snowmelt on the distant mountains and temperature rise more locally, with potential impacts for the planet.
Links between climate change and health were rare, however, one speaker explained that hotter temperatures brought new disease risks to humans:
“ What is there is that the rays of the sun, the layer between sun and the earth is what people call depleting nowadays, isn't it? This leads to an increase in heat. This heat has brought about different diseases. Like, mosquito bites cause various diseases. I have heard from the radio that climate change has adversely affected human beings .” (Bharatpur; Interview A14).
In explaining the causes of temperature rise that bring about health risks from flying insects, the speaker combines elements of ozone layer depletion and global warming. This reflects the way that lay understandings of climate change do not map neatly onto expert definitions, but often overlap with other environmental problems ( Rudiak-Gould, 2012 ).
Changes in Precipitation
Following changes in temperature, particularly in the summer months, changes in precipitation were the other main symptom linked to climate change in both communities. An example of this type of perception is provided in Section 3.1.3, though talk of erratic or reduced rainfall was framed locally and very nearly always unconnected with global climate change. However, when the issue of climate change was deliberately elicited by the interviewer, a greater degree of acknowledgment was given to the influence of the phenomenon on local changes particularly in relation to agriculture:
“ Because of global warming, there is not timely rainfall, nothing happens according to the growing seasons. For example, no rain in the rainy reason but it is (rainy) in winter time. Nothing occurring at the right time, I guess this is all the impact of climate change .” (Kumroj, Interview B13).
Because of global warming, regular patterns of precipitation and the seasons had been thrown into disarray. This was of particular importance in the Terai in terms of agriculture, and was the primary way in which such changes to established patterns were recognized. For others, while erratic weather had recently been observed, it was of little concern as the weather tended not to be consistent but changeable day-to-day:
“ Few years back there was heavy rain, but now there is very little rain, and the summer heat has increased since last year…I think it's not really concerning me because every day is different and going on in its own way, so I don't feel really concerned about it .” (Kumroj, Interview B12).
In general, accounts of changing temperature and weather were constructed in ways that assumed a transition from the stable and consistent natural patterns of the past, to a present in which established patterns had been disrupted. However, for those less concerned, changes were viewed as part of natural variability. Ultimately, when thinking about local conditions, climate change typically did not form a part of community perspectives unless introduced by the interviewer. The final section summarizes individual climate-relevant behavioral responses to the issues raised in talking about the environment.
Health and Well-Being Motivates Engagement in Climate-Relevant Behaviors
Because participants in Bharatpur and Kumroj often did not associate local issues with climate change, there was little talk of the need to adopt specific mitigation or adaptation behaviors. However, within each community one or two climate-relevant behaviors were raised in the course of discussing engagement in more general environmentally-relevant actions. For example, planting trees was widely practiced in both communities. Primarily, this was done to provide wood, create shade around homes and provide fruit. Trees were also considered important in preventing drought (see section on Climate and Weather) and other natural disasters such as flooding and erosion (see section Future Deforestation). In addition, a few participants framed climate-relevant behaviors as motivated by the need to safeguard health and well-being:
“ Trees I plant in the rainy season, so I plant yearly. Once I cut the old, then I plant new…Trees keep the environment clean and healthier. Trees inhale carbon dioxide and exhale oxygen” (Bharatpur, Interview A6).
While there was no clear link made to climate change, participants acknowledged the value of reducing atmospheric carbon, which was understood as maintaining a “ clean and healthier ” environment. Essentially, such climate-relevant practices were understood not in accordance with received scientific conceptualisations of climate change, but through more pragmatic perspectives linked to health and well-being.
In Kumroj, the Nepalese government had tried to maintain forest stocks by encouraging villagers to purchase biogas converters through grant schemes. Several participants, mainly from Kumroj, had biogas converters. These were seen as advantageous as organic waste could be utilized for producing fuel and then used as a fertilizer. Food could also be cooked quicker without the need to light a fire, and it reduced the need to collect wood. While participants did not mention the link between biogas practices and climate change, one of the most important benefits of biogas was that it did not pollute the air and so reduced health risks linked to inhaling wood smoke:
“ It (biogas) is clean and the air is also clean. The utensils are also not black. Biogas is more hygienic. People can be safe from colds and coughs and smoke-related diseases .” (Kumroj; Interview B13).
Cleanliness is paramount to the importance of biogas in the above extract. The pollution emitted by burnt wood is illustrated with reference to the condition of cooking utensils, with the implication that the wider environment is being affected in a similar way. In contrast, biogas does not discolor cooking utensils, which illustrates the fuel's superiority in terms of minimizing health risks caused by woodsmoke.
This study set out to investigate community perceptions of environmental and climate-relevant issues within two communities in the Terai region of Nepal. Specifically, we sought to address 4 related research questions; (1) How do community members perceive their environment? (2) How do they see that environment changing in future? (3) To what degree are communities aware of climate change? (4) How important is climate change in comparison to other issues? A range of environmental and climate-relevant issues emerged within current and future perspectives. Perspectives were focused primarily on local issues rather than wider environmental conditions. Issues linked to health and well-being were of paramount importance, while climate change was hardly mentioned in either community, either as a current or future problem. However, there was common awareness of temperature and weather changes in the local climate, though the vast majority did not link these changes to climate change. We now move on to discuss the results of our analyses in more detail.
For participants in both communities, assessments of the local environment were commonly based on evaluations of a single locally-salient issue. Positive issues, such as improvements in sanitation over time, invariably resulted in positive overall evaluations of the environment overall. Conversely, pollution resulted in more negative overall assessments. This highlights the highly subjective nature of environmental perceptions and the way in which specific issues can achieve heightened significance in judgements of environmental quality.
Many of the environmental issues raised in both communities were related to health and well-being, including cleanliness, pollution, and deforestation. It may be the relative proximity of each community contributed to this overlapping of issues. It may also be because they represent basic environmental concerns common to many communities—keeping the environment clean, healthy, and pollution free. Similarities between communities may also be partly attributable to our sampling method (see section Study Limitations and Future Research) There were also some differences in issues between communities. While plastic waste was more of an issue in Bharatpur, deforestation came up more often in Kumroj—though neither issue was exclusive to each community.
Climate change as an issue came up only once spontaneously, implying that other local issues were more salient. However, temperature and weather changes analogous to climate change did come up in several interviews across both communities, though without attribution to climate change. There was also little consideration of causal factors beyond immediate local causes such as deforestation affecting precipitation, flooding, and land erosion. In line with Leichenko and Silva (2014) , it appeared that temperature and weather changes allied to global climate change were already being experienced, though such issues were more atomized and vernacular and sometimes merged with other environmental problems ( Rudiak-Gould, 2012 ). In line with previous work, community perspectives often drew on different issues without attempting to clearly categorize or explain them ( Lorenzoni et al., 2007 ). Xiao and Dunlap (2007) note how particular environmental cognitions can constrain others; it is therefore possible that, when issues are framed locally, wider frameworks of understanding are overlooked.
Perceptions of Future Environmental Change
Perceptions of future environmental change were closely linked to mental representations of current conditions and issues of anxiety and concern. This could be seen in the way that participants rarely spoke about sanitation with reference to environmental change in the future, as sanitation had improved within communities. However, concerns about issues linked to current population increase were projected into the future and anticipated to continue unabated. Previous work has found that existing perceptions of self and other can be elicited through projections of “possible selves” in the future ( Harrison, 2018 ). In the same way, communities' imagined environmental futures highlight salient issues within existing relationships between communities and their physical surroundings.
The Terai region has witnessed large increases in population over recent decades ( Population Reference Bureau, 2002 ), and this was linked to pollution, deforestation and pressure on natural resources. While predictions of temperature and weather emerged from the interviews, such impacts were less frequently mentioned than concerns over population growth, as found in other research (e.g., Butler et al., 2014 ). Before communities can interpret and respond to climate-relevant issues, it may therefore be necessary to address existing concerns characterized by visions of the present and the future. In addition, the analysis highlights the relevance of sociocultural arrangements and cultural practices that contribute to community perspectives. For example, tree-felling was understood sympathetically within wider contexts of survival and economic struggle, as well as fuel shortages that left no alternative but to take wood from the forest. Such perspectives serve to highlight the complex nature and wider structural relations sustaining environmentally damaging practices.
Awareness of Climate Change
Climate awareness was relatively unmentioned in discussing the local environment, echoing previous studies ( Gallup, 2009 ; Withana and Auch, 2014 ). We found little difference between awareness in Bharatpur and Kumroj. A potential reason for this is that the changes observed suggest broader shifts in temperature and weather affecting the wider region, rather than localized effects or micro-climates that might affect one community and not another. Other studies have also reported lower awareness in rural communities ( Tanner et al., 2018 ), though a lack of difference may be due to the higher levels of environmental awareness from NGO engagement in Kumroj. However, while most participants did not spontaneously discuss the issue of climate change, when directly questioned, all had at least heard of climate change and many were able to eloquently demonstrate a good degree of knowledge. Therefore, it may not have been that participants were unaware of climate change, but simply did not consider it a locally salient issue. Tanner et al. (2018) also found that climate change awareness was low, despite respondents observing changes to local weather and climate. It may be that communities look to more local explanations for climate-relevant issues, as was found in some discussions. Therefore, if received knowledge teaches that the lack of rain is due to local forests being depleted, why would communities look to wider, more nebulous phenomena as explanations? The kinds of issues that came up in talk of climate change broadly reflects other research on community perceptions of climate change in the Terai (e.g., Tiwari et al., 2010 ; Maharjan et al., 2011 ). The apparent disjuncture between local experience and climate change suggests that the latter may lack relevance for local communities as long as environmental changes can be attributed to more local causal factors. It also suggests two kinds of climate change; a distanced, abstract climate change, and a more experiential, locally-grounded one. Within communities facing such impacts there is a need for a nuanced understanding that blends both. Howe et al. (2013) remark that local perceptions, such as temperature change, can positively bias perceptions of more abstract global climate change, which in turn can generate greater awareness and the capacity to respond to reduce risks to communities. As communities appear to be aware that the local climate is changing in a variety of ways, it is necessary to translate this awareness beyond the local. Reciprocally, more global perspectives need to connect with the concerns and interests of communities at the local level to make climate change more relevant to people's everyday lives. Bain et al. (2016) discuss evidence for initiatives promoting public engagement designed to generate support on the basis of considerations that are independent of climate change, including health and the creation of benevolent communities.
Study Limitations and Future Research
The use of a single qualitative methodological approach utilizing a small sample can only provide a partial insight into climate-relevant and environmental issues confronting the communities studied. Qualitative interview methods rely heavily on participants being able to recall and clearly convey their thoughts in the limited context of the interview interaction. Managing interview interactions in a cross-cultural setting remains a significant challenge and it is possible that the framing of questions could have influenced responses, such as precluding the discussion of global climate change by not deliberately eliciting the topic early in the interviews. Triangulation using other methods and larger samples might help to clarify these qualitative findings. Convergence in perspectives between communities may be attributable to our sampling method. While we categorized Bharatpur as the urban counterpart to rural Kumroj, most participants lived on the edges of the city close to the countryside, which may have generated perceptions that were more aligned with a rural, rather than an urban perspective. Future research might further investigate the apparent disparity between awareness of climate change more generally, and a lack of acknowledgment of climate change in discussions of environmental conditions at the local level. Drawing attention to this gap might also serve to elicit more comprehensive community perspectives and rule out potential shortcomings of a single methodological approach.
Data Availability
The raw data supporting the conclusions of this manuscript will be made available by the authors, without undue reservation, to any qualified researcher.
Ethics Statement
This study was carried out in accordance with the recommendations of the Ethics Policy, Cardiff University School of Psychology. The protocol was approved by the Cardiff University School of Psychology Ethics Committee. All subjects gave written informed consent in accordance with the Declaration of Helsinki.
Author Contributions
NN, IC, and RM conducted fieldwork with the assistance and guidance of LW and SC. NN was primarily responsible for analysis and authorship of the paper, with significant contributions in both areas from the other authors. All authors agree to be accountable for the content of the work.
This project was funded by the European Research Council (ERC) as part of the CASPI Project (no. 336665).
Conflict of Interest Statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Acknowledgments
Many thanks to Ugan Manandhar of WWF Nepal and the staff of ISER-Nepal for their valued collaboration on this project. Thanks also to Jyotsna Shrestha (independent translator) for help in designing the study and assisting with the translation of interviews in Kumroj, and Bishnu Adhikari, who assisted with fieldwork translation in Bharatpur. This paper is dedicated to the memory of Krishnan Ghimire of ISER-Nepal, who was instrumental in supporting the research.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fsoc.2019.00060/full#supplementary-material
Adger, W. N. (2003). Social capital, collective action, and adaptation to climate change. Econ. Geogr. 79, 387–404. doi: 10.1111/j.1944-8287.2003.tb00220.x
CrossRef Full Text
Adger, W. N., Barnett, J., Brown, K., Marshall, N., and O'Brien, K. (2013). Cultural dimensions of climate change impacts and adaptation. Nat. Clim. Change 3, 112–117. doi: 10.1038/nclimate1666
CrossRef Full Text | Google Scholar
Adhikari, B. (2018). The State of economic development in Nepal. Int. J. Soc. Sci. Manage. 5, 43–45. doi: 10.3126/ijssm.v5i1.19029
Aryal, S., Cockfield, G., and Maraseni, T. N. (2014). Vulnerability of Himalayan transhumant communities to climate change. Clim. Change 125, 193–208. doi: 10.1007/s10584-014-1157-5
Bain, P. G., Milfont, T. L., Kashima, Y., Bilewicz, M., Doron, G., Garð*arsdóttir, R. B., et al. (2016). Co-benefits of addressing climate change can motivate action around the world. Nat. Clim. Change 6, 154–157. doi: 10.1038/nclimate2814
Becken, S., Lama, A. K., and Espiner, S. (2013). The cultural context of climate change impacts: perceptions among community members in the Annapurna Conservation Area, Nepal. Environ. Dev. 8, 22–37. doi: 10.1016/j.envdev.2013.05.007
Bhatta, L. D., van Oort, B. E. H., Stork, N. E., and Baral, H. (2015). Ecosystem services and livelihoods in a changing climate: understanding local adaptations in the Upper Koshi, Nepal. Int. J. Biodivers. Sci. Ecosyst. Serv. Manage. 11, 145–155. doi: 10.1080/21513732.2015.1027793
Bickerstaff, K. (2004). Risk perception research: socio-cultural perspectives on the public experience of air pollution. Environ. Int. 30, 827–840. doi: 10.1016/j.envint.2003.12.001
PubMed Abstract | CrossRef Full Text | Google Scholar
Brooks, J., McCluskey, S., Turley, E., and King, N. (2015). The utility of template analysis in qualitative psychology research. Qual. Res. Psychol. 12, 202–222. doi: 10.1080/14780887.2014.955224
Butler, J. R. A., Skewes, T., Mitchell, D., Pontio, M., and Hills, T. (2014). Stakeholder perceptions of ecosystem service declines in Milne Bay, Papua New Guinea: is human population a more critical driver than climate change? Mar. Policy 46, 1–13. doi: 10.1016/j.marpol.2013.12.011
Byg, A., and Salick, J. (2009). Local perspectives on a global phenomenon - climate change in Eastern Tibetan villages. Glob. Environ. Change 19,156–166. doi: 10.1016/j.gloenvcha.2009.01.010
Caelli, K., Ray, L., and Mill, J. (2003). ‘Clear as mud’: toward greater clarity in generic qualitative research. Int. J. Qual. Methods 2, 1–13. doi: 10.1177/160940690300200201
Campbell, R., and Wasco, S. M. (2000). Feminist approaches to social science: epistemological and methodological tenets. Am. J. Commun. Psychol. 28, 773–791. doi: 10.1023/A:1005159716099
Caretta, M. A. (2015). Situated knowledge in cross-cultural, cross-language research: a collaborative reflexive analysis of researcher, assistant and participant subjectivities. Qual. Res. 15, 489–505. doi: 10.1177/1468794114543404
Carter, L. (2019). Indigenous Pacific Approaches to Climate Change. Palgrave Studies in Disaster Anthropology. Champaign. IL: Palgrave Pivot.
Chapagain, B. K., Subedi, R., and Paudel, N. S. (2009). Exploring local knowledge of climate change: some reflections. J. For. Livelihood 8, 108–112.
Google Scholar
Clayton, S., Devine-Wright, P., Stern, P. C., Whitmarsh, L., Carrico, A., Steg, L., et al. (2015). Psychological research and global climate change. Nat. Clim. Change 5, 640–646. doi: 10.1038/nclimate2622
Dahal, N. (2005). Perceptions in the Himalayas. Tiempo 56, 19–24.
Devkota, R. P., and Bhattarai, U. (2018). Assessment of climate change impact on floods from a techno-social perspective. J. Flood Risk Manage. 11, S186–S196. doi: 10.1111/jfr3.12192
Dwyer, S. C., and Buckle, J. L. (2009). The space between: on being an insider-outsider in qualitative research. Int. J. Qual. Methods 8, 54–63. doi: 10.1177/160940690900800105
Evans, G. W. (2019). Projected behavioral impacts of global climate change. Annu. Rev. Psychol. 70, 449–474. doi: 10.1146/annurev-psych-010418-103023
Flick, U. (2000). “Episodic interviewing,” in Qualitative Researching With Text, Image and Sound , eds M. W. Bauer and G. Gaskell (London: Sage), 75–92.
Fong, M. (2012). “The nexus of language, communication, and culture,” in Intercultural Communication: A Reader , 13th Edn, eds L. A. Samovar, R. E. Porter, and E. R. McDaniel (Belmont CA: Wadsworth), 83–94.
Gagnon, M., Jacob, J. D., and McCabe, J. (2015). Locating the qualitative interview: reflecting on space and place in nursing research. J. Res. Nurs. 20, 203–215. doi: 10.1177/1744987114536571
Gahatraj, S., Jha, R. K., and Singh, O. P. (2018). Impacts of climate change on rice production and strategies for adaptation in Chitwan, Nepal. J. Agric. Nat. Resour. 1, 114–121. doi: 10.3126/janr.v1i1.22226
Galletta, A. (2013). Mastering the Semi-structured Interview and Beyond: From Research Design to Analysis and Publication . New York, NY: New York University Press.
Gallup (2009). High Risk, Low Awareness of Climate Change in Nepal . Available online at: https://news.gallup.com/poll/124658/high-risk-low-awareness-climate-change-nepal.aspx (accessed November20, 2018).
Gentle, P., Thwaites, R., Race, D., and Alexander, K. (2014). Differential impacts of climate change on communities in the middle hills region of Nepal. Nat. Hazards 74, 815–836. doi: 10.1007/s11069-014-1218-0
Gentle, P., Thwaites, R., Race, D., Alexander, K., and Maraseni, T. (2018). Household and community responses to impacts of climate change in the rural hills of Nepal. Clim. Change . 147, 267–282. doi: 10.1007/s10584-017-2124-8
Gupta, J. (2010). A history of international climate change policy. Wiley Interdiscip. Rev. Clim. Change 1, 636–653. doi: 10.1002/wcc.67
Gurung, S. M. (1989). Human perception of mountain hazards in the Kakani-Kathmandu area: experiences from the middle mountains of Nepal. Mt. Res. Dev. 9, 353–364. doi: 10.2307/3673584
Hagaman, A. K., and Wutich, A. (2017). How many interviews are enough to identify metathemes in multisited and cross-cultural research? Another perspective on Guest, Bunce, and Johnson's (2006) landmark study. Field Methods 29, 23–41. doi: 10.1177/1525822X16640447
Harrison, N. (2018). Using the lens of ‘possible selves’ to explore access to higher education: a new conceptual model for practice, policy, and research. Soc. Sci. 7:209. doi: 10.3390/socsci7100209
Hoover, S. M., Strapp, C. M., Ito, A., Foster, K., and Roth, K. (2018). Teaching qualitative research interviewer skills: a developmental framework for social justice psychological research teams. Qual. Psychol. 5:300. doi: 10.1037/qup0000101
Howe, P. D., Markowitz, E. M., Lee, T. M., Ko, C. Y., and Leiserowitz, A. (2013). Global perceptions of local temperature change. Nat. Clim. Change 3:352. doi: 10.1038/nclimate1768
Hulme, M. (2009). Why We Disagree About Climate Change: Understanding Controversy, Inaction and Opportunity . Cambridge: Cambridge University Press.
Hulme, M. (2012). Telling a different tale: literary, historical and meteorological readings of a Norfolk heatwave. Clim. Change 113, 5–21. doi: 10.1007/s10584-012-0400-1
Hulme, M. (2014). Attributing weather extremes to ‘climate change’: a review. Prog. Phys. Geogr. 38, 499–511. doi: 10.1177/0309133314538644
Jovchelovitch, S., and Bauer, M. W. (2000). “Narrative interviewing,” in Qualitative Researching With Text, Image and Sound , eds M. Bauer and G. Gaskell (London: Sage), 57–74.
Khanal, U., Wilson, C., Lee, B. L., and Hoang, V. N. (2018). Climate change adaptation strategies and food productivity in Nepal: a counterfactual analysis. Clim. Change 148, 575–590. doi: 10.1007/s10584-018-2214-2
King, N., Horrocks, C., and Brooks, J. (2018). Interviews in Qualitative Research . London: Sage.
Larkin, P. J., Dierckx de Casterlé, B., and Schotsmans, P. (2007). Multilingual translation issues in qualitative research: reflections on a metaphorical process. Qual. Health Res. 17, 468–476. doi: 10.1177/1049732307299258
Lee, T. M., Markowitz, E. M., Howe, P. D., Ko, C. Y., and Leiserowitz, A. A. (2015). Predictors of public climate change awareness and risk perception around the world. Nat. Clim. Change 5, 1014–1020. doi: 10.1038/nclimate2728
Leichenko, R., and Silva, J. A. (2014). Climate change and poverty: vulnerability, impacts, and alleviation strategies. Wiley Interdiscip. Rev. Climate Change 5, 539–556. doi: 10.1002/wcc.287
Leiserowitz, A. (2007). Public Perception, Opinion and Understanding of Climate Change - Current Patterns, Trends and Limitations . New York, NY: United Nations Development Programme.
Lorenzoni, I., Nicholson-Cole, I., and Whitmarsh, L. (2007). Barriers perceived to engaging with climate change among the UK public and their policy implications. Glob. Environ. Change 17, 445–459. doi: 10.1016/j.gloenvcha.2007.01.004
Maharjan, K. L., and Joshi, N. P. (2012). Climate Change, Agriculture and Rural Livelihoods in Developing Countries With Reference to Nepal . Hiroshima International Center for Environment Cooperation (HICEC), IDEC, Hiroshima University.
Maharjan, K. L., and Joshi, N. P. (2013). Effect of Climate Variables on Yield of Major Food-Crops in Nepal: A Time-Series Analysis . Available online at: https://mpra.ub.uni-muenchen.de/35379/1/MPRA_paper_35379.pdf 12/11/18 (accessed November 30, 2018).
Maharjan, S. K., Maharjan, K. L., Tiwari, U., and Sen, N. P. (2017). Participatory vulnerability assessment of climate vulnerabilities and impacts in Madi Valley of Chitwan district, Nepal. Cogent Food Agric. 3:1310078. doi: 10.1080/23311932.2017.1310078
Maharjan, S. K., Sigdel, E. R., Sthapit, B. R., and Regmi, B. R. (2011). Tharu community's perception on climate changes and their adaptive initiations to withstand its impacts in Western Terai of Nepal. Int. NGO J. 6, 35–42. doi: 10.5897/NGO10.003
Manandhar, S., Vogt, D. S., Perret, S. R., and Kazama, F. (2011). Adapting cropping systems to climate change in Nepal: a cross-regional study of farmers' perception and practices. Reg. Environ. Change 11, 335–348. doi: 10.1007/s10113-010-0137-1
McIntosh, M. J., and Morse, J. M. (2015). Situating and constructing diversity in semi-structured interviews. Glob. Qual. Nurs. Res. 2, 1–12. doi: 10.1177/2333393615597674
Myers, T. A., Maibach, E. W., Roser-Renouf, C., Akerlof, K., and Leiserowitz, A. A. (2013). The relationship between personal experience and belief in the reality of global warming. Nat. Clim. Chang. 3, 343–348. doi: 10.1038/nclimate1754
Paudel, B., Zhang, Y., Yan, J., Rai, R., and Li, L. (2019). Farmers' perceptions of agricultural land use changes in Nepal and their major drivers. J. Environ. Manage. 235, 432–441. doi: 10.1016/j.jenvman.2019.01.091
Paudel, M. N. (2012). Adaptation mechanisms in agriculture for climate change in Nepal. Hydro Nepal J. Water Energy Environ. 11, 81–85. doi: 10.3126/hn.v11i1.7219
Paudel, M. N. (2016). Consequences of climate change in agriculture and ways to cope up its effect in Nepal. Agron. J. Nepal 4, 25–37. doi: 10.3126/ajn.v4i0.15514
Population Reference Bureau (2002). Population Growth Continues to Hinder Nepal's Economic Progress . Available online at: https://www.prb.org/populationgrowthcontinuestohindernepalseconomicprogress/ (accessed February 11, 2019).
Poudel, D. D., and Duex, T. W. (2017). Vanishing springs in Nepalese mountains: assessment of water sources, farmers' perceptions, and climate change adaptation. Mt. Res. Dev. 37, 35–47. doi: 10.1659/MRD-JOURNAL-D-16-00039.1
Prasain, S. (2018). Climate change adaptation measure on agricultural communities of Dhye in Upper Mustang, Nepal. Clim. Change 148, 279–291. doi: 10.1007/s10584-018-2187-1
Raulet-Croset, N., and Borzeix, A. (2014). Researching spatial practices through commentated walks: “On the move” and “walking with”. J. Org. Ethnogr. 3, 27–42. doi: 10.1108/JOE-11-2012-0046
Rawal, D. S., and Bharti, L. (2015). Identification of crop species vulnerable to projected climate change in three agro-ecological zones of the Koshi river basin, Nepal. J. Hill Agric. 6, 233–243. doi: 10.5958/2230-7338.2015.00050.6
Rogelj, J., Popp, A., Calvin, K. V., Luderer, G., Emmerling, J., Gernaat, D., et al. (2018). Scenarios towards limiting global mean temperature increase below 1.5 C. Nat. Clim. Change 8, 325–334. doi: 10.1038/s41558-018-0091-3
Rudiak-Gould, P. (2012). Promiscuous corroboration and climate change translation: a case study from the Marshall Islands. Glob. Environ. Change 22, 46–54. doi: 10.1016/j.gloenvcha.2011.09.011
Savo, V., Lepofsky, D., Benner, J. P., Kohfeld, K. E., Bailey, J., and Lertzman, K. (2016). Observations of climate change among subsistence-oriented communities around the world. Nat. Clim. Change 6, 462–473. doi: 10.1038/nclimate2958
Shrestha, S., Moore, G. A., and Peel, M. C. (2018). Trends in winter fog events in the Terai region of Nepal. Agric. For. Meteorol. 259, 118–130. doi: 10.1016/j.agrformet.2018.04.018
Sikes, P. (2018). “Working together for critical research ethics,” in Researching Ethically Across Cultures: Issues of Knowledge, Power and Voice , eds A. Robinson-Pant and N. Singal (Abingdon: Routledge), 92–112.
Silverman, D. (2015). Interpreting Qualitative Data . London: Sage.
Smit, B., Burton, I., Klein, R. J., and Wandel, J. (2000). “An anatomy of adaptation to climate change and variability,” in Societal Adaptation to Climate Variability and Change , eds S. M. Kane and G. W. Yohe (Dordrecht: Springer Science + Media), 223–251.
Smit, B., and Wandel, J. (2006). Adaptation, adaptive capacity and vulnerability. Glob. Environ. Change 16, 282–292. doi: 10.1016/j.gloenvcha.2006.03.008
Tanner, T., Acharya, S., and Bahadur, A. (2018). Perceptions of climate change: applying assessments to policy and practice . Available online at: https://www.researchgate.net/profile/Thomas_Tanner2/publication/324246811_Perceptions_of_climate_change_Applying_assessments_to_policy_and_practice/links/5ac71156a6fdcc8bfc7f9038/Perceptions-of-climate-change-Applying-assessments-to-policy-and-practice.pdf (accessed November 16, 2018).
Timmermans, S., and Tavory, I. (2012). Theory construction in qualitative research: from grounded theory to abductive analysis. Sociol. Theory 30, 167–186. doi: 10.1177/0735275112457914
Tiwari, K. R., Awasthi, K. D., Balla, M. K., and Sitaula, B. K. (2010). Local people's perception on climate change, its impact and adaptation practices in Himalaya to Terai regions of Nepal . Available online at: https://digitalrepository.unm.edu/nsc_research/48/ (accessed November 20, 2018).
Trenberth, K. E., Fasullo, J. T., and Shepherd, T. G. (2015). Attribution of climate extreme events. Nat. Clim. Change 5, 725–730. doi: 10.1038/nclimate2657
Uprety, Y., Shrestha, U. B., Rokaya, M. B., Shrestha, S., Chaudhary, R. P., Thakali, A., et al. (2017). Perceptions of climate change by highland communities in the Nepal Himalaya. Clim. Dev. 9, 649–661. doi: 10.1080/17565529.2017.1304886
Van Teijlingen, E., Simkhada, B., Porter, M., Simkhada, P., Pitchforth, E., and Bhatta, P. (2011). Qualitative research and its place in health research in Nepal. Kathmandu Univ. Med. J. 9, 301–305. doi: 10.3126/kumj.v9i4.6350
Watts, N., Amann, M., Ayeb-Karlsson, S., Belesova, K., Bouley, T., Boykoff, M., et al. (2018). The Lancet Countdown on health and climate change: from 25 years of inaction to a global transformation for public health. Lancet 391, 581–630. doi: 10.1016/S0140-6736(17)32464-9
Weber, E. U. (2010). What shapes perceptions of climate change?. Wiley Interdisc. Rev. Clim. Change 1, 332–342. doi: 10.1002/wcc.41
Whitmarsh, L. (2011). Scepticism and uncertainty about climate change: dimensions, determinants and change over time. Glob. Environ. Change 21, 690–700. doi: 10.1016/j.gloenvcha.2011.01.016
Wicks, P. G., and Reason, P. (2009). Initiating action research: challenges and paradoxes of opening communicative space. Action Res. 7, 243–263. doi: 10.1177/1476750309336715
Withana, N. R. P., and Auch, E. (2014). Perceptions of climate change risk to forest ecosystems: a case study of Patale community forestry user group, Nepal. Int. J. Environ. Ecol. Geol. Geophys. Eng. 8, 565–572.
Xiao, C., and Dunlap, R. E. (2007). Validating a comprehensive model of environmental concern cross nationally: a U.S.-Canadian comparison. Soc. Sci. Q. 88, 471–493. doi: 10.1111/j.1540-6237.2007.00467.x
Zinn, A. (2004). Social Contexts and Responses to Risk Network (SCARR). Literature Review: Sociology and Risk. Working Paper . Available online at: http://www.kent.ac.uk/scarr/papers/Sociology%20Literature%20Review%20WP1.04%20Zinn.pdf (accessed November 20, 2018).
Zomer, R. J., Trabucco, A., Metzger, M. J., Wang, M., Oli, K. P., and Xu, J. (2014). Projected climate change impacts on spatial distribution of bioclimatic zones and ecoregions within the Kailash sacred landscape of China, India, Nepal. Clim. Change 125, 445–460. doi: 10.1007/s10584-014-1176-2
Keywords: climate change, environment, perception, community, local, Nepal, culture
Citation: Nash N, Capstick S, Whitmarsh L, Chaudhary I and Manandhar R (2019) Perceptions of Local Environmental Issues and the Relevance of Climate Change in Nepal's Terai: Perspectives From Two Communities. Front. Sociol. 4:60. doi: 10.3389/fsoc.2019.00060
Received: 11 March 2019; Accepted: 22 July 2019; Published: 20 August 2019.
Reviewed by:
Copyright © 2019 Nash, Capstick, Whitmarsh, Chaudhary and Manandhar. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Nick Nash, nashn1@cardiff.ac.uk
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.

Humans can work with nature to solve big environmental problems – but there’s no quick fix
Associate Professor, School of Environmental and Conservation Sciences, Murdoch University
Research Fellow, School of Agriculture, Food and Ecosystem Sciences, The University of Melbourne
Disclosure statement
Rachel Standish receives funding from the Australian Research Council and the Cooperative Research Centre for Transformations in Mining Economies.
Tina Parkhurst has received funding from the Cooperative Research Centre for Transformations in Mining Economies.
University of Melbourne provides funding as a founding partner of The Conversation AU.
Murdoch University provides funding as a member of The Conversation AU.
View all partners
“Nature-based solutions” are gaining momentum in environmental policy, including in Australia. They involve working with nature to protect, restore or manage ecosystems in a way that benefits both people and the environment.
This might include restoring coastal mangroves to protect a community from coastal erosion, or replanting forests to store carbon, provide cleaner air, and create habitat for wildlife.
But such solutions must go the distance, if their full potential is to be realised. In particular, they must be able to withstand short-term disturbances such as fire or drought, as well as longer-term change such as global warming.
How do we ensure their resilience? Our review of nature-based solutions around the world set out to answer this question.
We found biological diversity – at the level of genes, species, communities and whole ecosystems – is key to creating nature-based solutions that last. In contrast, quick-fix solutions, such as planting a single species of tree, are less likely to work in the long run.
These findings are crucial for Australia, as the federal government establishes markets for nature repair and informing biodiversity policies.

Biodiversity is vital
Biological diversity refers to richness at every level – from the genetic diversity of individual plants, animals and fungi, to the range of species, and diversity within communities, ecosystems and landscapes.
Diverse ecosystems are more resilient. That’s because different species in an ecosystem vary in their responses to change.
For example , some plant species complete their life cycle before the drought season. Other plants tolerate drought by adjusting their metabolism. A third group avoid drought by shutting down, including shedding old leaves and closing their stomata.
This means even when some species are stressed or missing altogether, an ecosystem can keep ticking along.
The same is true for planted forests . Diverse planted forests are more resilient to fires, pests and diseases compared with low diversity projects. So they’re more likely to capture and store carbon, helping tackle climate change.
So if we want nature-based solutions to last, biodiversity must be at the core.
What we did
Our review involved analysing 78 research papers published internationally and in Australia over the past 20 years. We wanted to assess how ecological resilience was addressed in nature-based solutions.
A subset of papers described nature-based solutions in urban, agricultural and forested landscapes. Many focused on reducing impacts of climate change in cities. Then we considered key papers on ecological resilience and how to apply this knowledge to nature-based solutions.
So what did we find?
Most projects did not consider how resilience came about. This was true for resilience within species and populations, such as ensuring genetic diversity. It also applied at the landscape scale, such as providing connectivity between animal populations to prevent inbreeding.
The exception was afforestation projects – planting forests in degraded landscapes. In this domain, there is increasing recognition that species diversity is needed to create resilient ecosystems.
Researchers have, however, identified ways to make ecosystems more resilient – for example by restoring degraded land adjacent to remnant vegetation or controlling invasive predators that eat native wildlife.
The knowledge exists. The key now is to put these resilience ideas into practice.

Which interventions can help?
Our review confirms the best nature-based solutions mimic nature. So, interventions to conserve existing ecosystems are ideal. Once an ecosystem is destroyed, restoring diversity is difficult.
Controlling invasive species such as cane toads can also help by protecting pockets of native species from these threats.
Measures can also be carried out across entire landscapes. For example, the Gondwana Link project in southwestern Australia set out to revegetate abandoned farmland and reconnect patches of bushland for native wildlife.
Climate change is prompting land managers to rethink their “local is best” approach to sourcing seed and seedlings. Plants that are better adapted to heat and drought may be preferable. However, this approach requires further testing.
And returning plants with different drought strategies could help restore landscapes scorched by wildfire .
Looking ahead
Quick-fix, low-diversity solutions are not likely to recover after disturbances such as fire and drought. So while these projects are nature-based, the solution could be fleeting.
In Australia, the Nature Repair Market will incentivise nature-based solutions. First Nations people, conservation groups and other landholders will be rewarded for actions that deliver improved biodiversity outcomes. This includes returning vegetation along rivers and controlling invasive weeds and pests.
Our findings suggest nature repair and biodiversity markets should support actions that provide long-term benefits rather than quick wins. This could involve providing clear guidelines to landholders and ensuring their activities are accredited. It may also involve monitoring the outcomes of projects and rewarding success.
And these solutions take time to create. Governments should invest in research to develop projects that deliver long-lasting benefits. This includes understanding how to motivate people to drive successful outcomes.
Restoring biologically diverse landscapes may take time and effort. But for the sake of both people and the natural world, we must get it right.
- Climate change
- Biodiversity
- Environment
- Carbon sequestration
- Tree planting
- Climate crisis
- Forest restoration
- nature-based solutions
- Nature restoration
- nature repair
- Nature-based solutions to climate change

Project Manager SSTP

Head of Evidence to Action

Supply Chain - Assistant/Associate Professor (Tenure-Track)

OzGrav Postdoctoral Research Fellow

Casual Facilitator: GERRIC Student Programs - Arts, Design and Architecture
Writing a Paper about an Environmental Issue
- Homework Tips
- Learning Styles & Skills
- Study Methods
- Time Management
- Private School
- College Admissions
- College Life
- Graduate School
- Business School
- Distance Learning
:max_bytes(150000):strip_icc():format(webp)/Fred_mugshot-570525b95f9b581408c0928f.jpg)
- Ph.D., Wildlife Ecology, University of Maine
- M.A., Natural Resources, Humboldt State University
- B.S., Biology, Université du Québec à Rimouski
Are you a student tasked with writing a research paper on an environmental issue? These few tips, along with some hard and focused work, should get you most of the way there.
Find a Topic
Look for a topic that speaks to you, that grabs your attention. Alternatively, choose a topic about which you are genuinely interested in learning more. It will be a lot easier to spend time working on something of interest to you.
Here are some places you can find ideas for a paper:
- Global warming
- Biodiversity
- Deforestation
- Fossil fuels
- Water Pollution
- The science or environment sections of major newspapers and news organizations will feature articles about current environmental news and events.
- Environmental news websites like Grist or Environmental News Network .
Conduct Research
Are you using internet resources? Make sure you can assess the quality of the information you find. This article from Purdue University’s Online Writing Lab is useful to help with assessing the quality of your sources.
Print resources are not to be neglected. Visit your school or city library, learn how to use their search engine, and talk to your librarian about accessing the resources available.
Are you expected to constrain your sources to primary literature? That body of knowledge consists of peer-reviewed articles published in scientific journals. Consult your librarian for help with accessing the proper databases to reach those articles.
Follow Instructions
Carefully read the handout or prompt given to you and which contains instructions about the assignment. Early in the process, make sure you choose a topic that will satisfy the assigned requirements. Once half-way through the paper, and once when it’s done, check it against the instructions to make sure you didn’t drift away from what was required.
Start With a Solid Structure
First craft a paper outline with your main ideas organized, and a thesis statement . A logical outline will make it easy to gradually flesh out ideas and eventually produce complete paragraphs with good transitions between them. Make sure all the sections serve the purpose of the paper outlined in the thesis statement.
After you have a good draft produced, put the paper down, and don’t pick it up until the next day. It’s due tomorrow? Next time, start working on it earlier. This break will help you with the editing stage: you need fresh eyes to read, and re-read your draft for flow, typos, and a myriad other little problems.
Pay Attention to Formatting
Along the way, check that you are following your teacher’s formatting instructions: font size, line spacing, margins, length, page numbers, title page, etc. A poorly formatted paper will suggest to your teacher that not only the form, but the content is of low quality as well.
Avoid Plagiarism
First, make sure you know what plagiarism is , you can then more easily avoid it. Pay especially close attention to properly attributing the work you cite.
- 10 Tips for the SAT Essay
- How to Double Space Your Paper
- How to Organize Research Notes
- Lining Up Dots in a Table of Contents
- Newspaper Sections and Terms
- Turabian Style Guide With Examples
- The Difference Between Revising and Editing
- How to Use a Thesaurus
- How to Help Your 4th Grader Write a Biography
- Formatting Papers in Chicago Style
- College School Supplies List
- Writing the Parts of a Stage Play Script
- What Is a Blue Book?
- How to Solve Common Keyboard and Typing Problems
- Fourth Grade School Supplies List
- 18 Ways to Practice Spelling Words
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- CORRESPONDENCE
- 20 August 2024
More studies are needed on the long-term environmental consequences of war
- Patrick B. Newcombe 0
Princeton University, Princeton, New Jersey, USA.
You can also search for this author in PubMed Google Scholar
Research by historians, political scientists and environmental scientists is increasingly showing that the environmental effects of war have long-term humanitarian consequences. Conflicts worldwide, including in Burkina Faso, Gaza, Haiti, Mali, Sudan and Ukraine, demand multidisciplinary research to understand and address this global challenge.
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
24,99 € / 30 days
cancel any time
Subscribe to this journal
Receive 51 print issues and online access
185,98 € per year
only 3,65 € per issue
Rent or buy this article
Prices vary by article type
Prices may be subject to local taxes which are calculated during checkout
Nature 632 , 739 (2024)
doi: https://doi.org/10.1038/d41586-024-02711-z
Competing Interests
The author declares no competing interests.
Related Articles

See more letters to the editor
- Human behaviour
- Environmental sciences
Urgently clarify how AI can be used in medicine under new EU law
Correspondence 27 AUG 24
Local politicians have opened up Europe’s largest marine reserve for commercial fishing

AI firms must play fair when they use academic data in training
Editorial 27 AUG 24

Loss of plasticity in deep continual learning
Article 21 AUG 24
Are brains rewired for caring during pregnancy? Why the jury’s out
Correspondence 20 AUG 24

How pregnancy transforms the brain to prepare it for parenthood
News Feature 31 JUL 24

The meaning of the Anthropocene: why it matters even without a formal geological definition
Comment 26 AUG 24

Effective realization of abatement measures can reduce HFC-23 emissions
Tenure Track Faculty Position - Division of Hematology
The Division of Hematology at Washington University in St. Louis invites applications from outstanding candidates with a Ph.D. and/or M.D. degree f...
Saint Louis, Missouri
Washingon University School of Medicine - Division of Hematology
Lecturer/Senior Lecturer at the Dyson School of Design Engineering
About the role: Do you want to change the world for the better, and do you believe this can be done through research and education? If so, grab you...
South Kensington, London (Greater) (GB)
Imperial College London (ICL)
Faculty Positions in Westlake University
Founded in 2018, Westlake University is a new type of non-profit research-oriented university in Hangzhou, China, supported by public a...
Hangzhou, Zhejiang, China
Westlake University

Call for Global Talents, Recruitment Information of Nankai University
Nankai University welcomes global outstanding talents to join for common development.
Tianjin, China
Nankai University
Director for Signature Research Programme in Cancer and Stem Cell Biology, DukeNUS Medical School &
The successful candidate will demonstrate their ability of growing, leading and mentoring faculty as well as developing and operationalising strategy.
Singapore (SG)
DukeNUS Medical School
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Environmental Issues Research Paper

This sample environmental issues research paper features: 6700 words (approx. 22 pages), an outline, and a bibliography with 39 sources. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced writers for help. This is how your paper can get an A! Feel free to contact our writing service for professional assistance. We offer high-quality assignments for reasonable rates.
Introduction
Cultural beliefs and the environment, social construction and the environment, social construction and social movements, political economy and the environment, environmental issues: method and application, risk perception and environmental health, mobilization around toxic waste sites: love canal.
- Bibliography
More Environment Research Papers:
- Environmental Bioethics Research Paper
- Environmental Crime Research Paper
- Environmental Economics Research Paper
- Environmental Psychology Research Paper
- Environmental Regulation Research Paper
- Environmental Regulations Compliance Research Paper
- Environmental Rights Research Paper
- International Environmental Politics Research Paper
- Population and the Environment Research Paper
- Technology and the Environment Research Paper
Environmental issues can be discussed within a number of different contexts. For anthropology and sociology, culture and society become important factors in understanding environmental issues. By incorporating a perspective that includes environmental history, aspects of environmental change, dialogue and culture, and future concerns, a more complete understanding of the relationship between sociocultural actions and the natural environment can be developed. In an effort to understand the nature of environmental problems, one must develop an understanding of the cultural paradigms that guide human behavior and interaction with the natural environment. Many perspectives seek to explain this relationship. Social scientists look toward dialogue and cultural perspectives to trace the history of environmental concern.
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
Historically, humans have understood their role to be one of dominion over nature. This is explained in numerous classic works and referenced in many religious and spiritual texts as well (Bell, 2008; Dunlap & Mertig, 1992). Cultural paradigms exist that serve to guide our interactions with the environment. Most stem from the anthropocentric belief that the world is centered around people and that human society has the right to maintain dominion over nature. Structural beliefs provide the foundation of these understandings.
The belief that a free market system provides the greatest good for the greatest number of people leads us to place economic decision-making processes in private hands. Frequently, private decisions have public consequences, but these public consequences are not accounted for in production costs or covered by market costs. Instead, the costs are passed on to consumers in the form of taxes and higher base prices for goods and services. Esteemed environmentalists Al Gore Jr. and Robert Kennedy Jr. have argued that if the external costs of production were assumed by manufacturers, then the ultimate benefit would be a system that accounted for waste created in the production process. This is evident in their research on global warming. Coal-fired power plants are promoted as one of the cheapest forms of creating energy. This is misleading, because the health effects of pollution caused by coal are not included in the costs of production. Others argue that those costs would have to be passed on to the consumer. However, they are passed on now in the way of pollution and medical expenses for illnesses associated with environmental contaminants. Coal is one of the biggest contributors to greenhouse gases, thus leading to the overall societal costs of global warming.
Another cultural belief is that the natural world is inexhaustible. Extraction of natural resources happens at an incredible rate without a consideration to limits. Society’s constant dependence on nonrenewable energy forces mining and the refining of coal and oil to keep up with these demands. Consumer goods are deliberately planned to become obsolete within a relatively short time, and consumers are pressured to buy replacements. This process has been conceptualized in research focused on the treadmill of production. Production and utility processes, using natural resources, dominate the modes of production. The reliance on the treadmill model provides perpetual extraction and production, increasing the fragility of the natural environment.
Another cultural value resides in a lasting faith in technology. Culturally, we believe that technology can meet any challenge. Humans are seen as ingenious creatures able to devise solutions for any problem. However, technology itself is not sufficiently controlled and can create more problems that contribute to environmental degradation. This can lead to a situation known as culture lag, used here to describe a situation in which technology has outpaced the cultural ability to respond to the consequences of using a given technology.
The philosophy of the growth ethic argues that growth equals progress. Successful cultures are often defined by their levels of progress. Urban sprawl exemplifies the connection between progress and environmental destruction. Urban ecologists argue urban sprawl follows the concentric circle urban planning mode of the early 20th century. Residents were encouraged to develop space for residential purposes further away from city centers. This was culturally promoted as prime real estate, and individuals continued to purchase land as a showing of class standing. Urban sprawl results in the loss of green and open space, increased use of natural resources, and more vehicle miles traveled as commuting distance continues to increase.
Materialism is a cultural value that also contributes to how environmental problems emerge. Americans tend to measure success in terms of the consumption of material things. Globally, the most valued nation is one that can command and use the largest fraction of the world’s resources. Currently, the United States supports 5% of the world’s population and uses 25% of the world’s natural resources. This is evidence that the cultural emphasis on the consumption of material goods is in direct correlation with natural resource use.
Two final cultural values that impact environmental practices are individualism and an anthropocentric worldview. Cultures that emphasize individual rights and personal achievements tend to have a greater environmental impact. We place benefits to the self over what is best for the collective. Subsequently, the anthropocentric worldview is centered around human beings, thus inferring that human begins are superior to other beings and have natural rights to use the environment to ensure the progress of human beings as a species.
Subsequently, these cultural beliefs form the principles that overwhelmingly guide cultural interactions with nature. Theoretically, they serve as paradigms that explain the emergence of environmental issues. The following section provides specific theoretical underpinnings of environmental issues.
Theory and the Environment
Theory addressing environmental issues has been situated in the social constructionist and political economy approaches. Within these approaches, attention has been paid to developments of subfields in social science research, such as social movements and the environment, environmental health, and environmental justice.
Social constructionists focus on the construction of social problems and how this allows individuals to assign meaning and give importance to the social world. Sarbin and Kitsuse argued that “things are not given in the world, but constructed and negotiated by humans to make sense of the world” (1994, p. 3). When interests are at stake, claims are made around an activity in order to define the interests as problems. The process of claims making is more important than the task of assessing whether the claims are true (Hannigan, 1995).
Hannigan provides a three-step process for the construction of environmental problems: assembling, presenting, and contesting. He argues that each step develops the claimsmaking activities of environmental activists and antagonists. Environmental problems are different from other social problems, because claims are often based on physical, chemical, or biological scientific evidence (Hannigan, 1995). In nearly all cases of environmental problems, even though such problems are based on scientific evidence, the burden of proof falls on the claims-makers, the environmental actors.
When a claim about an environmental problem is presented, state and corporate actors emerge most often to challenge the validity of these problems. Although these actors are willing to construct the issue as a “problem,” support to alleviate the problem is often lacking. If it supports the alleviation of the problem, most probably through funding remedial efforts or research, the state or corporation is seen as taking responsibility for the problem. If the state is seen as responsible, its perceived legitimacy decreases, which may lead to decreased trust. On the other hand, if a problem is not acknowledged, then trust in government may also decrease, because the perception arises that the interests of the state are not the best for the people.
The power of individuals in roles and positions to define these claims is ultimately what allows problems to be defined as problems. Claims may be made by others not in a position of power, but they are often not seen as valid because of the lack of power associated with the role. Different claims of environmental problems then lead to different definitions of the problems.
Definitions of problems are framed to illustrate specific viewpoints of what the problem is. Goffman used the term frame in order to explain interpretations of occurrences. Frames can serve as explanations or guideposts to individual or collective action (Snow & Benford, 1988). Snow and Benford describe framing as an activity performed by social movements to express their viewpoints and “to assign meaning to and interpret relevant events and conditions in ways that are intended to mobilize potential adherents and constituents—to garner bystander support and demobilize antagonists” (p. 198).
By framing events in certain ways that assign meaning to them, actors can attempt to mobilize support and delegitimize opposing viewpoints. Because different frames may emerge surrounding the same problem, individuals may choose to adopt one or the other on the basis of the reliability of the frames. One factor in determining reliability is trust in the actors who present the frame. Constituents may mobilize around one frame because trust in that explanation and the organization that presents it is high (Robinson, 2009). This impacts how individuals interpret the seriousness of environmental problems and subsequently whether issues will be acted on and in what manner.
The framing process can serve to mobilize constituents for or against a particular cause. Mobilization against frames that are presented by actors emerges when the audience of the frame has low trust in the source of the frame. Social movement literature has acknowledged the emergence of mobilization over environmental issues where lack of trust is present. Examples include institutional recreancy, lack of trust in government agencies and officials, and the combination of the two (Brown & Mikkelsen, 1990; Cable & Cable, 1997; Freudenburg, 1993; Gaventa, 1980; Gibbs, 1982).
Charles Tilly provides a model for mobilization that bridges some of the ideological views of frame analysis with collective action and resource mobilization theory. Tilly’s (1978) definition of mobilization is “a process by which a group goes from a passive collection of individuals to an active participant in public life” (p. 69). A further extreme of this model is resource mobilization theory, which gives even less importance to ideological factors and, instead, emphasizes the need for available resources. The combination of ideologies, resources, and the power of frame presentation contribute to mobilization. Using this analytical framework, the emergence of environmental problems and mobilization around these problems can be better understood.
Environmental problems in communities provide a setting to further explore this connection. Community organizing around local problems has a long history in the United States. Many forms of community organizing exist. These have included writing and literacy circle newsletters in the late 19th and early 20th centuries, Saul Alinsky’s model of radical politics to create mass organizations to seize power and give it to the people (1971), and neighborhood block clubs. The goals to spread awareness, ensure social justice, and understand that city hall can be fought vary in scope and magnitude but have often proved to be effective models for organizing.
Citizen action in response to toxic waste at Love Canal has emerged as the premier example of community organizing over environmental issues. The story of neighborhood organizing and the quest for a clean, healthy environment is acknowledged in most major studies on environmental issues. The specifics of this case follow in a later section where the application of environmental issues is discussed.
Theories of political economy of environmental issues focus on the development of political and economic practices and policies that contribute to environmental problems. Primarily, the focus has been on the creation of the capitalist mode of production that leads to overwhelming environmental destruction. Furthermore, the development of capitalism promotes a political environment that is friendly to more profitable, but less environmentally friendly, practices.
In addition to physical environmental realities that production processes cause, issues of health and economic injustice exist. Bryant and Mohai (1992) asked whether a safe environment is a civil right. They argue that people of color see environmental degradation interrelated with economic and political justice. This is the fundamental idea behind environmental justice in both action and theory. Another issue in environmental justice arises because people of color and lower income are less likely to have access to health insurance; thus, they become more ill if exposed to environmental hazards without means of treatment. Therefore, these populations share more of the negative environmental burden and have fewer resources to resolve the given problems.
The connection between health and economic justice is not a new relationship. Since World War II, there has been an increase in the development of the petrochemical industry. Coinciding with an increased demand for synthetic chemicals was an increased demand for disposal sites for waste byproducts of these chemicals. Many disposal sites were created in vacant plots of land, without the regulated disposal standards in place today. Expensive land used for the disposal sites of the 1940s and 1950s became the residential suburban developments of the 1960s, 1970s, and 1980s. With the post–World War II increase in population, many families were moving into suburban neighborhoods. Families felt safe from the problems of the cities, but they were not aware that many residential properties were built near the abandoned chemical waste sites of prior decades.
The problems of environmental contamination were first addressed publicly in Rachel Carson’s Silent Spring (1962). Her warning of chemical contaminants silencing biological life was not heeded at the time her book was published. These issues were not addressed until the 1970s with the first Earth Day in 1970, followed by the passing of numerous pieces of environmental protection legislation and the creation of the Environmental Protection Agency (EPA). Through this period of uncertainty, unclear scientific findings overwhelmed policymakers and the public, leading to confusion about how to develop environmental policies and actions.
Environmental problems have manifested most directly in the form of pollution. Evidence of environmental destruction is seen in the form of air, water, and land pollution that has a direct impact on the health of the human population. One of the most direct links between pollution and negative health effects has been identified since the creation of the petrochemical industry in the 1940s. Since this time, we have seen more cases of cancer and respiratory illness in the human population. The rate remains high even when controlling for mitigating factors, such as the effects of advanced medical technology in treating these illnesses, and lifestyle factors, such as diet and smoking. This case was made with the infamous discovery of toxic waste at Love Canal, New York, in 1978.
Literature in this area addresses the possible effects of exposure to toxins on one’s health. However, few studies have provided irrefutable evidence supporting the research hypothesis (association exists) or the null hypothesis (no association exists). Scientists know that chemicals can have adverse effects on the human condition when ingested, but they argue that some indirect exposures through air, soil, water, or residential habitation in proximity to such toxins have not provided similar consequences. The basic disagreement emerges in how one views risk, either through the precautionary principle or through risk assessment and evaluation. Proponents of the precautionary principle argue that if the chance of danger is present, then precaution should be used to avoid exposure. Risk assessment would argue the opposite—that the risk must be known before action is taken to avoid exposure. The difficulty is that science has not provided irrefutable evidence on the dangers of many chemical substances; therefore action for their removal from products and the environment has been slow. Recently, Devra Davis took on this phenomenon in The Secret History of the War on Cancer (2008). She outlined the lack of scientific responsibility in reporting findings connecting cancer and chemical exposure.
Most reports have not described exposures accurately, or they have failed to completely identify a causal factor (National Research Council, 1991). The Committee on Environmental Epidemiology was formed to assess the progress on hazardous waste assessment since the creation of Superfund and the Agency for Toxic Substance and Disease Registry. The committee concluded that no conclusive reports could be used to base policy on, because there are no measures in place to accurately depict exposure assessments. Their conclusions continue: There exists no comprehensive inventory of waste sites, no site discovery program, no minimum data set on human exposures, and no policy for immediate action if exposure exists (National Research Council, 1991). The report indicates that “the nation is not adequately identifying, assessing, or ranking hazardous-waste site exposures and their potential effects on human health” (p. 21).
Environmental toxins have long been thought to be causally related to the incidence of disease. Air pollution, specifically with carbon dioxide and sulfur dioxide, has been studied in association with asthma and pulmonary disorders (Carnow, Lepper, Shekelle, & Stamler, 1969). Water pollution, particularly with trichloroethylene and tetrachloroethylene, sparked a concern about childhood and adult leukemia in Woburn, Massachusetts (Brown & Mikkelsen, 1990). Similarly, numerous studies have been conducted that investigate the exposure-ailment connection (Landrigan, 1990; Neutra, Lipscomb, Satin, & Shusterman, 1991; Paigen, Goldman, Mougnant, Highland, & Steegman, 1987). These studies use descriptive and case-control methods and field investigations consisting of surveys and physical examinations, resulting in quantitative analyses in order to test hypotheses.
Descriptive studies portray disease patterns in populations according to person, place, and time, and they include time-series analyses (National Research Council, 1991). For example, a study performed by the National Cancer Institute used maps of cancer incidences and toxic waste sites, concluding that the high incidence of bladder cancer in northwestern Illinois counties was significant and leading to the implementation of an incidence study using survey methods (National Research Council, 1991).
A cohort study was employed with North Carolina residents who consumed raw polluted river water contaminated by an industrial site from 1947 to 1976. Residents’ rates of all forms of cancer were more than twice those expected in the general population (National Research Council, 1991). Once exposure ceased, rates returned to the expected level, adjusting for latency.
The epidemiologic case-control study carried out in Woburn, Massachusetts, yielded an association between leukemia and drinking from contaminated wells. The EPA could not pinpoint the source of contamination; therefore, it could not infer conclusively that the cases of leukemia were due to the proximity of a hazardous waste site (Lagakos, Wessen, & Lelen, 1986).
Griffith, Duncan, Riggan, and Pellom (1989) analyzed EPA and cancer mortality data from 13 U.S. sites where there were major incidences of cancer between 1970 and 1979. They found evidence that contaminated ground water was used for human consumption at 593 waste sites in 339 U.S. counties in 49 states. Significant associations were found between several cancers and exposure to contaminated water in white males; these included cancers of the lung, bladder, esophagus, stomach, large intestine, and rectum (Griffith et al., 1989). Higher incidences of cancers of the lung, bladder, breast, stomach, large intestine, and rectum were found in white females in these counties (Griffith et al., 1989), when compared with females in counties that did not have hazardous waste sites. However, this study has been criticized based on its use of populationbased incidences of cancer rather than individual-level estimates. Researchers inferred that proximity to hazardous waste sites caused cancer.
Wong, Morgan, Whorton, Gordon, and Kheifets (1989) performed an ecologic and case-control analysis to evaluate whether there was an association between groundwater contamination with dibromochloropropane (DBCP) and mortality from gastric cancer and leukemia. The only positive association that was found was in farm workers. No relationship was found for gastric cancer or leukemia with DBCP contamination of drinking water.
Neutra et al. (1991) found that individuals living near toxic waste sites had one or more bothersome symptoms that those living in control areas did not have. However, rates of cancer and birth defects were not found to be statistically significantly different for these individuals than for those in the control neighborhoods. Symptoms such as worrying, depression, and nervousness were more likely to be the result of knowledge of the site and its contaminants than the result of chemical exposure. Although some practitioners argue that residents near these sites do show higher incidences of asthma and psychological disturbances than individuals in control groups, the findings remain highly controversial (Neutra et al., 1991).
For the most part, these studies consist of survey and field investigation methodologies, relying on self-report methods. One problem with explaining associations that rely on self-report methods is that if residents want to be relocated or have other agendas, then the degree to which symptoms are reported may increase. Many residents felt that this was what some homeowners were hoping for at Love Canal. This remains one of the most critical problems with state and federal agency studies that seek to provide evidence of community risk.
With the increase in studies in this area, the public has been partially reassured by having the knowledge that at least concerns are being recognized. Specifically, cancer rates are still high, but the fear of human-made chemicals has largely been dispelled. Most recently, the organic food movement has been gaining legitimacy. Yet, many still doubt the health benefits behind this movement. Studies concerning environmental racism have been more prevalent, focusing on the incidence of lower-income, nonwhite families living near toxic waste sites. This focus has taken attention away from specific health problems. Instead, the focus has been on issues of political economy and equity. This is not a criticism of environmental justice but rather a call for the convergence of natural science and sociology in order to address both issues. Other variables to be considered in these studies may include racial composition of counties, social class of counties, concentration of low-income occupations in counties, new housing starts in counties, and the percentage of welfare recipients per county.
The uncertainty of science had created cross-discipline dialogue. Social scientists have addressed environmental issues in studies of risk assessment, disaster relief (both natural and technological), toxic exposure, and other datadriven areas. Because of the risk of chemical exposure due to toxic waste, landfills emerged as one of the most imminent public health threats with the discovery of Love Canal. However, even in cases where studies to show an association between illness and exposure to toxic chemicals have been inconclusive, the message has been that these chemicals cause cancer and needed to be eradicated.
An important role of science is to inform the public of findings, usually through the media. Epidemiologic studies deal with human populations and are often questioned based on the legitimacy of the data and the willingness of the agency or corporation funding the research to share findings with the public. These studies are also usually based on relatively small populations and a small number of events; this results in a lack of significant findings, because sample sizes are too small to generate statistically reliable conclusions. Researchers are asked to report conclusions to various interest groups that may have a stake in the research problem. The pressure of the public arena and media, with emerging concerns and consequences for public health and the environment, has led to a decrease in the willingness to share data and be criticized if the data do not fit the public agenda. Politics and public perception surpass what science is able to provide. Science’s inability to prove negatives has led to public policy that tries to control what cannot be established. This uncertainty shapes policy to err on the side of protection; yet in many communities the risks are endured regardless.
Findings often snowball into hard line conclusions and the perception of a problem when one may not exist, or vice versa. Risk perception and the realization of risks are two different things. Risk perception may encompass what one believes might occur or an understanding based on secondary information. Risk realization occurs when one is physically affected by the agent or situation and a decision to act is based on that encounter. The problem arises in this discrepancy. Perception is what people perceive to be happening. With different information from different scientific experts, the public is left to decide on their own who or what is right, based on the health and well-being of themselves and their families.
Freudenburg (1993) discussed the concept of risk and recreancy in public decision making. He argues that an increase in institutional responsibility for risk management has created a system where responsibilities are often overlooked. This concept proposes increased frequency in institutional decision making in risk analysis. Freudenburg (1993) coined the term recreancy to identify the institutional failure to follow through on a duty or responsibility or broadly expected obligations to the collective. Questions are now raised by individuals deciphering scientific studies for themselves, but they now question the role of institutional actors. Without correlational data from an alternative institutional source that they trust, citizens do not know where to turn for clear answers about data regarding environmental toxins.
Community-based studies by community organizers have emerged in an attempt to address the failure of institutions to provide real, understandable answers regarding human health and exposure rates. Specifically, recent literature calls for more involvement of the scientific community in the decision-making process. A resurgence of popular epidemiology, since Lois Gibbs’s attempt in 1978– 1979, has found individuals using lay methods to determine association. Even if they don’t result in strong, scientific evidence, community-based studies at least provide the groundwork and show a need for more in-depth studies. Brown and Mikkelsen’s 1990 study is a strong example of this method. The question of whether there was a connection between childhood leukemia and known contaminated well water divided the community, but it forced epidemiologic studies.
Coinciding with these revelations, other studies were being conducted that attempted to link other contaminated sites with adverse health effects. As Gots (1993) stated, most were laboratory studies in simulated environments. Examples of human studies existed only in the sociological and epidemiological literature (Brown & Mikkelsen, 1990; Gibbs, 1982; Landrigan, 1990; Neutra et al., 1991). Incidences of chemical scares were also prevalent. Headlines concerning the dioxin scare at Times Beach, Missouri; contamination of apple crops with the synthetic growth regulator Alar; and use of Agent Orange created the fear that human-made chemicals cause disease. Evidence existed that these specific chemicals may cause health problems in humans, but data on the incidence of illness relative to exposure and on synergistic effects of these chemicals were missing. Furthermore, there was even less information available about other potential threats to health, such as airborne and waterborne contaminants, environmental sensitivity disorders, and living in proximity to hazardous waste sites. To establish a causal relationship between exposure and chemicals, obtaining valid measures and estimates for exposure is essential.
Environmental Movements
Contaminated Communities; The Challenge of Social Control; Environmental Problems as Conflicts of Interests; Disasters, Collective Behavior, and Social Organization; Love Canal: Science, Politics, People, and Power; and Powerlessness are just a few of the book titles that describe the scope and emergence of the mobilization surrounding environmental problems. Since the publication of Silent Spring, the struggle to define, understand, and resolve environmental problems has inundated environmental literature as well as the agendas of environmental organizations at both the national and local levels.
The environmental movement in the United States can be traced back to the early conservationists at the turn of the 20th century, whose focus was on control of natural resources for technological and societal use. Accompanying this was a movement toward the preservation of the natural environment simply for nature’s sake and separate from any use and/or value that human society had placed upon it.
The contemporary environmental movement embraced both of these traditions while focusing on building a political alliance to ensure the passage of legislation that would protect both nature and human health. As evidenced by the multitude of legislative victories the environmental movement claimed during the 1970s, the environmental movement was gaining prominence as one of the most successful efforts of social movement organizers.
Politically, momentum began to shift back toward the wise-use movement throughout the 1980s. Environmental problems were framed in opposition to capitalist goals. Politicians took an either/or stance: jobs or the environment. With one’s economic livelihood seemingly at stake, it is no wonder that concern for the environment was diminished in the public agenda. The environmental health movement is arguably one area that continued to keep environmental issues in the public’s consciousness. One of the classic and influential cases in environmental organizing, Love Canal, illustrates the interconnectedness of politics, science, and the environment.
To understand the factors contributing to the emergence, awareness, and mobilization around environmental problems, the scope and focus of the problem must be considered. This analysis focuses on the emergence of and mobilization around toxic waste sites found in residential communities. Literature addressing toxic waste sites in communities place Love Canal, New York, as the first community to encounter such a problem that received national media attention. Although community protests were occurring around the toxics issue as early as 1970, no other site received the same degree of national media attention (Szasz, 1994).
In 1978, Love Canal was declared a federal disaster area, but the final homeowner evacuation was voluntary, not mandatory, even though the state had said a health emergency may exist. Given the possibility of ill-health effects, residents were given the choice about whether to stay or move. Because of the lack of strong correlational evidence, public health officials were not able to substantiate a link between exposure to chemicals and disease (Robinson, 2002).
The questionable contaminated area was evacuated and became known as the Emergency Declaration Area (EDA). It was divided into seven sampling areas. Two studies were performed to assess the habitability and safety of the area. The first study was completed in 1982 by the New York State Department of Health (DOH), the EPA, and the U.S. Department of Health and Human Services. Problems arose about the study’s conclusion, which was that the EDA was as habitable as comparable control areas. The Congressional Office of Technology Assessment found that the study lacked information to determine whether unsafe levels of contamination existed and that it did not make clear what next steps should be taken. Thereafter, DOH and EPA conducted a second study on habitability; it was released in 1988. Habitability and safety have been studied in regard to numerous hazardous waste sites, but actual rates of illness have not been linked to exposure to toxic substances from nearby chemical waste sites.
The Superfund Act, passed in 1980, was written specifically in response to the known hazardous waste site at Love Canal. Policymakers recognized that industry used land-based disposal methods, that industrial sites were contaminated, and that an increase in clean air and water standards led to a decrease in land-based regulated disposal (Barnett, 1994). The problem was that there was neither an informed way of counting or tracking these sites, nor evidence of an adverse ecosystem and human effects (Barnett, 1994).
Since Love Canal, no other neighborhood has received the same degree of attention, although many have encountered toxic waste contaminants in their communities (Brown & Mikkelsen, 1990; Bryant & Mohai, 1992; Cable, Walsh, & Warland, 1988). No conclusive, significant correlation between chemicals and cancer has been found at Love Canal or at the other identified exposure sites. Nor has any truly verifiable evidence been found that exposure to, and living near, any other toxic waste site causes disease, though disorders have been loosely associated with chemical exposure, such as asthma, respiratory disease, nerve damage, miscarriages, and cancer.
People living near these sites must often decide on how much they want to expose themselves to risk. Once the presence of a waste site is known, they must decide, without data to guide their decisions, whether to stay in their homes or leave. This has historically interfered with the availability and collection of valid data. When a study is conducted, residents request to be informed of the results and progress of the study. Because most epidemiological studies require longitudinal or cohort analysis in order to be reliable and valid, it is advantageous to have a stable, nonmobile population. This begs ethical questions, on behalf of the researchers, to disclose data relating to exposure before the study is completed. Researchers cannot both verify exposure findings and expect residents to remain so that they can carry out the remainder of the study. Thus, individuals, families, and communities are asked to base their decisions on claims that cannot be substantiated one way or the other.
Toxic waste sites continue to be discovered in communities. In many cases, the resulting community struggles are extended battles. The operative phrase in many cases is “once a site is discovered.” The chemicals in Love Canal were buried 30 years before it was known to the community that their houses, school, and playground were built on top of and surrounding a chemical site containing 22,000 tons of waste. This is not to say that the problem didn’t exist before its discovery by residents; it just wasn’t defined as a problem. From the time the chemicals were buried to the discovery of the site by residents 30 years later, residents noticed dogs with burned noses, children with skin rashes, and increased rates of miscarriages, leukemia, and nerve and respiratory disorders. But they were not aware that these rates were out of the ordinary. The effects of the problem did not change, but the way the problem was represented did. The shift was in an awareness of the existence of the problem.
In addition to the chemical disaster at Love Canal, other environmental issues have been the subject of various social movement activities, as well as political legislation. In each instance, public perception influences how and whether the problem is acted on by those with the power to make a difference.
Culturally and socially, environmental problems represent problems of social organization, communication, and socialization. Social scientists can look toward the phenomenon, visible in the reaction to environmental problems, to begin making sense of culture and society at large. Our understanding of environmental issues as primarily social constructions offers insight into how these issues are created, maintained, and resolved.
For example, in many cases where chemical contamination is the focal issue of community groups, the level of risk is perceived by affected individuals rather than established by science. It is the social processes in a community that lead to risk determination, not the natural science interpretations of an issue. Individuals have been socialized to trust science for valid information. When the determination of risk is uncertain, individuals are left to determine the level of risk for themselves by other means. In most cases, this determination is made through contact with state or federal government officials, through collaboration with other community members, or through other sources of information, such as the media. This framework helps to explain disagreements over the seriousness of most environmental issues, from global climate change to mountain-top coal removal.
The subjective reality of environmental problems becomes visible in terms of how the issue is circulated in cultural discourse. Each stakeholder constructs different means of projecting information for public consumption. When presented in the media, the perception is that information is true and accurate. Most often the determination of risk takes place in the form of a public meeting. In this situation, public officials are in control of the meeting, drawing on public anticipation surrounding the specific issue and information to be released. At Love Canal, for example, officials kept the information to be discussed at the meeting private until the meeting in order to build anticipation and increase their power over the dissemination of information.
At both the cultural and social level, power is maintained through these exercises. Often, the state controls the dissemination of information that individuals perceive to be true and accurate. However, different modes of collaboration among community members can create a different means of risk determination. The sharing of common experiences among community residents can lead to a broader sense of mobilization. Once commonalties are recognized, residents begin to determine their own level of risk. Risk perception is based on the potential danger of a problem. The sources that individuals base their information and understanding on are numerous. Each source has developed a frame of events and information on which they base their version of reality. Whether from the media, science, the state, or local knowledge, such frames serve as a means to display a problem in terms of a specific group. Social movement development, in relation to the environment, offers a powerful tool for individuals looking to construct the frame of a given environmental reality.
The ways in which environmental realities have been constructed influences how they will be acted on socially, culturally, and politically. Cultural discourse then circulates in the public sphere and becomes normative. Environmental issues become part of the public dialogue. This dialogue serves to help develop an understanding about the factors that coalesce to create, maintain, and resolve social processes that influence environmental problems.
Community-level interaction is an interesting social space from which to witness environmental understanding. Community-based, environmental problems affect individuals in many ways. Some communities mobilize and form environmental organizations to address a specific problem. Others, with existing community organizations, add environmental problems to their agenda. Environmental problems can vary in scope, size, and duration.
Mobilization in these communities may occur due to individuals’ fear that nothing is being done to ensure the safety of their children and families. It may also occur on the basis of frustration and an inability to understand what and why this is happening in their community. In addition, community groups often mobilize as a result of a lack of trust in government. The mobilization of individuals to resist the state’s discourse challenges the power of the state. The level of trust in government is a key factor in determining the level of power the state can maintain during the presentation of its frame. For example, if trust in government is low, then a stronger frame needs to be developed to legitimize the government’s position. Government often emerges as the key stakeholder, as the actor that will have the power to create change.
Previous research addresses the state’s desire to maintain legitimacy at the same time that community groups seek to resist state discourse. Admitting that there is a problem shows that the state is capable of mistakes, and thus, the state’s legitimacy can be questioned and it is vulnerable. The goal in the rhetoric of the state is not to raise questions, thereby maintaining legitimacy.
Most environmental problems are categorized by place: global, local, or national. These categories are not mutually exclusive. For example, ozone depletion is a global problem because of the total atmospheric effects the ozone layer has on the biosphere from ultraviolet rays. Yet the problem can be seen as being local in an area where heavy smog is causing ozone depletion and high surface area ozone levels, such as in a highly urban area like Los Angeles.
Similarly, the discovery of toxic waste sites across the United States can be seen as a national problem. But in the specific communities where these sites are discovered, it is a local problem affecting individuals directly. The problem is no longer seen as away from them; it is now part of their community. This developing framework of environmental issues has helped individuals become aware of the multitude of impacts that these problems have. Social scientists have been able to develop an understanding of the environment that moves away from the depiction of the earth as something separate from human society, but, instead, the earth is a system with interrelated consequences and realities. One of the most vivid paradigm shifts has been the movement away from an anthropocentric worldview and toward an environmental worldview. This shift can be represented in the movement from the human environmental paradigm (HEP) to the new environmental paradigm (NEP).
Social scientists focus on this shift as a way to explain a cultural movement that has embraced a way of understanding the impact that society has on the environment. Arguably, once the NEP is part of the natural discourse of environmental issues, they become more easily recognized as problems that have risen from a system out of balance. This approach focuses on sustainable development and other modes of development that provide environmentally sensitive growth models. These efforts move toward a culture that is sensitive to a responsibility that ensures less devastating environmental impact in the future. As environmental sociologists and other environmental researchers seek answers for a sustainable society, we must consider the devastating impacts of our current modes of production. New modes of production that take into consideration innovative, green energy solutions will provide a stronger sustainable economy and environment for culture and society.
Bibliography:
- Alinsky, S. (1971). Rules for radicals. New York: Random House.
- Barnett, H. G. (1994). Toxic debts and the superfund dilemma. Chapel Hill: University of North Carolina Press.
- Bell, M. (2008). Invitation to environmental sociology (3rd ed.). Thousand Oaks, CA: Pine Forge Press.
- Brown, P., & Mikkelsen, E. (1990). No safe place: Toxic waste, leukemia and community action. Berkeley: University of California Press.
- Bryant, B., & Mohai, P. (Eds.). (1992). Race and the incidence of environmental hazards: A time for discourse. Boulder, CO: Westview Press.
- Cable, S., & Cable, C. (1997). Environmental problems, grassroots solutions: The politics of grassroots environmental conflict. New York: St. Martin’s Press.
- Cable, S., Walsh, E., & Warland, R. (1988). Differential paths to political activism: Comparison of four mobilization processes after the Three Mile Island accident. Social Forces, 66, 951–969.
- Carnow, B. W., Lepper, M. H., Shekelle, R. B., & Stamler, J. (1969). Chicago air pollution study: SO 2 levels and acute illness in patients with chronic bronchiopulmonary disease. Archives of Environmental Health, 18, 768–776.
- Carson, R. (1962). Silent spring. Boston: Houghton Mifflin.
- Cylke, F. K. (1993). The environment. New York: HarperCollins.
- Davis, D. (2008). The secret history of the war on cancer. New York: Basic Books.
- Dunlap, R., & Mertig, A. (1992). The evolution of the U.S. environmental movement from 1970 to 1990: An overview. London: Taylor & Francis.
- Freudenburg, W. (1993). Risk and recreancy: Weber, the division of labor, and the rationality of risk perceptions. Social Forces, 71 (4), 909–932.
- Gaventa, J. (1980). Power and powerlessness: Quiescence and rebellion in an Appalachian Valley. Urbana: University of Illinois Press.
- Gibbs, L. (1982). Love Canal: My story. Albany, NY: SUNY Press.
- Gore, A., Jr. (2006). An inconvenient truth: The planetary emergency of global warming and what we can do about it. Emmaus, NY: Rodale Press.
- Gots, R. E. (1993). Toxic risks: Science regulation and perception. Boca Raton, FL: Lewis.
- Gould, K. A., Pellow, D., & Schnaiberg, A. (2008). The treadmill of production: Injustice and unsustainability in the global economy. Boulder, CO: Paradigm.
- Griffith, J. R. C., Duncan, R. C., Riggan, W. B., & Pellom, A. C. (1989). Cancer mortality in U.S. counties with hazardous waste sites and ground water pollution. Archives of Environmental Health, 44, 69–74.
- Hannigan, J. (1995). Environmental sociology: A social constructionist perspective. London: Routledge.
- Kennedy, R. F., Jr. (2004). Crimes against nature: How George Bush and his corporate pals are plundering the country and hijacking our democracy. New York: HarperCollins.
- Kettel, B. (1996). Women, health and the environment. Social Science & Medicine, 42, 1367–1379.
- Lagakos, S. W., Wessen, B., & Lelen, M. (1986). Contaminated well water and health effects in Woburn, Massachusetts . Journal of the American Statistical Association, 81, 583–614.
- Landrigan, P. J. (1990). Prevention of toxic environmental illness in the twenty-first century. Environmental Health Perspectives, 86, 197–199.
- Landrigan, P. J. (1992). Commentary: Environmental disease— A preventable epidemic. American Journal of Public Health, 82, 941–943.
- Levine, A. (1982). Love Canal: Science, politics, people. Lexington, MA: D. C. Heath.
- Lipscomb, J. A., Goldman, L. R., Satin, K. P., Smith, D. F., Vance, W., & Neutra, R. (1991). A follow-up study of the community near the McColl Waste Disposal Site. Environmental Health Perspectives, 94, 15–24.
- National Research Council. (1991). Environmental epidemiology: Public health and hazardous wastes. Washington, DC: National Academy Press.
- Neutra, R., Lipscomb, J., Satin, K., & Shusterman, D. (1991). Hypotheses to explain the higher symptom rates observed around hazardous waste sites. Environmental Health Perspectives, 94, 31–38.
- Paigen, B., Goldman, L., Mougnant, M., Highland, J., & Steegman, A. T. (1987). Growth of children living near the hazardous waste site, Love Canal. Human Biology, 59, 489–508.
- Robinson, E. (2002). Community frame analysis in Love Canal: Understanding messages in a contaminated community. Sociological Spectrum, 22, 139–169.
- Robinson, E. (2009). Competing frames of environmental contamination: Influences on grassroots mobilization. Sociological Spectrum, 29, 3–27.
- Sarbin, T., & Kitsuse, J. (1994). Constructing the social. London: Sage.
- Snow, D., & Benford, R. D. (1988). Ideology, frame resonance and participant mobilization. International Social Movement Research, 1, 197–217.
- Steingraber, S. (2001). Having faith: An ecologist’s journey to motherhood. Cambridge, MA: Perseus.
- Szasz, A. (1994). Ecopopulism: Toxic waste and the movement for environmental justice. Minneapolis: University of Minnesota Press.
- Tilly, C. (1978). From mobilization to revolution. New York: McGraw-Hill.
- Townsend, P. (2009). Environmental anthropology: From pigs to policies (2nd ed.). Long Grove, IL: Waveland Press.
- Wong, O., Morgan, R. W., Whorton, M. D., Gordon, N., & Kheifets, L. (1989). Ecological analysis and case-control studies of gastric cancer and leukemia in relation to DBCP in drinking water in Fresno County, California. British Journal of Independent Medicine, 46, 521–528.
Browse more research papers on environmental issues:
Order high quality custom paper.

Journal of Environmental Issues and Climate Change

About the Journal
Journal of Environmental Issues and Climate Change (JEICC) is an open-access, peer-reviewed journal that publishes original research articles in English are focused on natural and climatic elements of environmental studies. The journal emphasizes interdisciplinary approaches that combine techniques from environmental and social analysis, climatology, biology, environmental issues, biodiversity, and ecology. The mission of JEICC is to offer a forum for global scientists to promote, exchange, and discuss numerous new concerns and advancements in various fields of natural and environmental science. Researchers and scientists are welcome to submit work to us if they want to advance science or society by introducing novel methods or insights. Readers have free access to all the resources. The aim of the Journal of Environmental Issues and Climate Change (JEICC) is to share knowledge and spread awareness about our environmental issues and climate change.
Publication fee
Publication in JEICC is FREE . Thus, it does not require any payment of page or publication charges by authors. JEICC is an open-access journal, which means all its contents are freely available over the internet to any reader.
Current Issue

In Progress Issue: February 2023
Journal of Environmental Issues and Climate Change (JEICC) is an open-access, peer-reviewed journal that publishes original research articles in English, triannually in February, June and October, that are focused on natural and climatic elements of environmental studies. The journal emphasizes interdisciplinary approaches that combine techniques from environmental and social analysis, climatology, biology, environmental issues, biodiversity, and ecology.
Rural Households’ Livelihood Diversification Activities: A Case Study from Borena District, North Central Ethiopia
An analysis of the quality of dhaka's potable water and sanitation services, flood vulnerability assessment of a semi-arid region: a case study of dutse in jigawa state, nigeria, the the inhibitory efficacy of plants extracts in the management of root knot nematode (m. incognita) infected crops, impact of slaughterhouse effluents on groundwater quality: evidence-based assessment in tudun-wada and kawo residential suburbs, kaduna, nigeria, gis-based spatial assessment of post covid water quality status of turag river for water resource conservation in bangladesh, assessment of heavy metal residues in soil and vegetables along urban-peri-urban gradient of lagos state nigeria, impact of productive safety net program on rural household food security in somali regional state: a case of kebri dehar district, ethiopia.
- Editorial Team
- Open Access Policy
- Focus and Scope
- Author Guidelines
- Journal License
- Peer Review Process
- Peer Reviewers
- Copyright Notice
- Crossmark Policy
- Publication fees
- Visitor Counter
Make a Submission
Download template.
e-ISSN: 2964-4887
p-ISSN: 2963-4105
Information
- For Readers
- For Authors
- For Librarians
- Livelihood Diversification as a Strategy to Overcome Food Insecurity Challenges in North Central Ethiopia: The Case of Borena District 489
- The Perception of Urban Dwellers on the Impact of Brickfields' Smoke Emissions on Socioeconomic Conditions and Human Health: A Case Study of Pabna, Bangladesh 445
- Rural Households’ Livelihood Diversification Activities: A Case Study from Borena District, North Central Ethiopia 407
- Isolation of Antibiotic Resistant Bacteria from Abattoir Waste Water: A Case Study of Makurdi Metropolis 399
- Smart Technologies for a Sustainable Service Supply Chain: A Prospective Perspective 391
Collaborators
Social media links, recommended tools.
- Publisher: Universitas Muhammadiyah Buton in Collaboration with Lembaga Riset dan Inovasi Masyarakat Madani
- Address : Jl. Betoambari, Kota Bau-Bau, Sulawesi Tenggara 93717.
- Email : [email protected]

Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu
- Subscribe SciFeed
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Exclusive papers of the editorial board members and topical advisory panel members of catalysts in section “catalytic materials”.

Author Contributions
Acknowledgments, conflicts of interest, list of contributions.
- Liu, P.; Qiao, H.; Su, X.; Peirong; Yang, F. Visible Light-Photocatalyzed C5-H Nitration of 8 Aminoquinoline Amides. Catalysts 2024 , 14 , 263. https://doi.org/10.3390/Catal14040263 .
- Neves, P.; Simoes, G.; Naprus, B.D.; Pamin, K. Versatile Polyoxo Metalates of Different Structural Dimensionalities for Liquid Phase Catalytic Oxidations. Catalysts 2024 , 14 , 251. https://doi.org/10.3390/Catal4040251 .
- Sidorenko, N.D.; Topchiyan, P.A.; Saraev, A.A.; Yu, E.; Gerasimov; Zhurenok, A.V.; Vasilchenko, D.B.; Kozlova, E.A. Bimettalic Pt-IrOx/g-C 3 N 4 Photocatalysts for the Highly Efficient Overall Water Splitting Under Visible Light. Catalysts 2024 , 14 , 225. https://doi.org/10.3390/Catal14040225 .
- Marks, K.; Erbing, A.; Hohmann, L.; Chien, T.-E.; Yazdi, M.G.; Muntwiler, M.; Hansson, T.; Engvall, K.; Harding, D.J.; Öström, H.; Odellus, M.; Göthelid, M. Naphthalene Dehydrogenation on Ni(111) in the Presence of Chemisorbed Oxygen and Nickel Oxide. Catalysts 2024 , 14 , 124. https://doi.org/10.3390/Catal14020124 .
- Cepollaro, E.M.; Cimino, S.; Marco D‘Agostini; Gargiulo, N. Giorgia Franchin, and Luciana Lisi, 3D-Printed Monoliths Based on Cu-Exchanged SSZ-13 as Catalystsfor SCR of NOx. Catalysts 2024 , 14 , 85. https://doi.org/10.3390/Catal14010085 .
- Chakarova, K.; Drenchev, N.; Mihaylov, M.; Hadjiivanov, K. Interaction of O 2 with Reduced Ceria nanoparticles at 100–400K: Fast Oxidation of Ce 3+ ions and dissolved H 2 . Catalysts 2024 , 14 , 45. https://doi.org/10.3390/Catal14010045 .
- Mohammadpour, N.; Uznanski, H.K.-P.; Tyczkowski, J. Plasma Deposited CoO-(Carbon Matrix) Thin-Film Nanocatalysts: The Impact of Nanoscale p-n Heterogunctions on Activity in CO 2 Methanations. Catalysts 2024 , 14 , 38. https://doi.org/10.3390/Catal14010038 .
- Zhu, Q.; Luo, Y.; Yang, K.; Che, G.; Wang, H.; Qi, J. Construction of Spinel/Perovskite Heterojunction for Boosting Photocatalytic Performance for Polyacrylamide. Catalysts 2023 , 13 , 1424. https://10.33901/Catal13111424 .
- Chernov, A.N.; Cherepanova, S.V.; Gerasimov, E.Y.; Prosvitin, I.P.; Zenkovets, G.A.; Shutilov, A.A.; Gorbunova, A.S.; Koltunov, K.Y.; Sobolev, V.L. Propane Dehydrogenation over Cobalt Aluminates: Evaluation of Potential Catalytic Active Sites. Catalysts 2023 , 13 , 1419. https://doi.org/10.3390/Catal13111419 .
- Rizzato, L.; Cavazzani, J.; Osti, A.; Scavini, M.; Glsenti, A. Cu-Doped SrTiO 3 Nanostructured Catalysts for CO 2 Conversion into Solar Fuels Using Localiged Surface Plasmon Resonance. Catalysts 2023 , 13 , 1377. https://doi.org/10.3390/Catal13101377 .
- Panek, B.; Kierzkowska-Pawlak, H.; Uznanski, P.; Nagy, S.; Nagy-Trembosova, V.; Tyczkowski, J. The role of Carbon Nanotube Deposit in Catalytic Activity of FeOx-Based PECVD Thin Films Tested in RWGS Reaction. Catalysts 2023 , 13 , 1302. https://doi.org/10.3390/Catal13091302 .
- Osti, A.; Rizzato, L.; Canazzani, J.; Gilsenti, A. Optimizing Citrate Combustion Synthesi of A-Site Defficient La, Mn-Based Perovskite: Application of Catalytic CH 4 Combustion in Stoichiometric Conditions. Catalysts 2023 , 13 , 1177. https://doi.org/10.3390/Catal13081177 .
- Afshari, M.; Carabineiro, S.A.C.; Gorjizadeh, M. Sulfonated Silica Coated CoFe 2 O 4 Magnetic Nanoparticles for the Synthesis of 3, 4-Dihydropyrimidin-2(1H)-one and octahydroquinazoline Derivatives. Catalysts 2023 , 13 , 989. https://doi.org/10.3390/Catal13060989 .
- Lee, J.W.; Jeong, R.H.; Shin, I.; Boo, J.-H. Fabrication of New TiO 2 Photo Catalyst for removing organic dyes and Harzadous VOCs in Air Purifier System. Catalysts 2023 , 13 , 935. https://doi.org/10.3390/Catal13060935 .
- Peng, A.; Huang, Z.; Li, G. Ethylene Oligomerization Catalyzed by Different Homogeneous or Heterogeneous Catalysts. Catalysts 2024 , 14 , 268. https://doi.org/10.3390/Catal14040268 .
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Liotta, L.F.; Kumar, N.; Hadjiivanov, K.I. Exclusive Papers of the Editorial Board Members and Topical Advisory Panel Members of Catalysts in Section “Catalytic Materials”. Catalysts 2024 , 14 , 564. https://doi.org/10.3390/catal14090564
Liotta LF, Kumar N, Hadjiivanov KI. Exclusive Papers of the Editorial Board Members and Topical Advisory Panel Members of Catalysts in Section “Catalytic Materials”. Catalysts . 2024; 14(9):564. https://doi.org/10.3390/catal14090564
Liotta, Leonarda Francesca, Narendra Kumar, and Konstantin Ivanov Hadjiivanov. 2024. "Exclusive Papers of the Editorial Board Members and Topical Advisory Panel Members of Catalysts in Section “Catalytic Materials”" Catalysts 14, no. 9: 564. https://doi.org/10.3390/catal14090564
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals

- E-mail the Help Desk
- User's Guide for H-Announce
Call for Papers: Crimson Historical Review
The Crimson Historical Review at the University of Alabama is a nationally acclaimed, highly selective, peer-reviewed, undergraduate, historical research journal that is now accepting submissions for its thirteenth issue. Publishing with the CHR offers bright researchers an opportunity to experience the rigors of the publication process in a supportive environment. If you have students who are doing original historical research that should be considered for publication, please consider sending them to the CHR at http://crimsonhistorical.ua.edu . The deadline for submissions for the Fall 2024 issue is September 20, 2024.
Thank you and Best Regards,
Dr. Margaret Peacock, Faculty Advisor for the Crimson Historical Review
Dr. Margaret Peacock
Securing data and preserving privacy in cloud IoT-based technologies an analysis of assessing threats and developing effective safeguard
- Open access
- Published: 27 August 2024
- Volume 57 , article number 269 , ( 2024 )
Cite this article
You have full access to this open access article

- Mayank Pathak 1 ,
- Kamta Nath Mishra 1 &
- Satya Prakash Singh 1
The Internet of Things (IoT) is a powerful technology adopted in various industries. Applications of the IoT aim to enhance automation, productivity, and user comfort in a cloud and distributive computing environment. Cloud computing automatically stores and analyzes the large amounts of data generated by IoT-based applications. Cloud computing has become a crucial component of the information age through easier data administration and storage. Currently, government agencies, commercial enterprises, and end users are rapidly migrating their data to cloud environments. This may require end-user authentication, greater safety, and data recovery in the event of an attack. A few issues were discovered by authors after analysis and assessments of various aspects of the published research papers. The research analysis reveals that the existing methods need to be further improved to address the contemporary dangers related to data security and privacy. Based on the research reports, it can be stated that safe end-to-end data transmission in a cloud-IoT environment requires modifications and advancements in the design of reliable protocols. Upcoming technologies like blockchain, machine learning, fog, and edge computing mitigate data over the cloud to some level. The study provides a thorough analysis of security threats including their categorization, and potential countermeasures to safeguard our cloud-IoT data. Additionally, the authors have summarized cutting-edge approaches like machine learning and blockchain technologies being used in the data security privacy areas. Further, this paper discusses the existing problems related to data privacy and security in the cloud-IoT environment in today’s world and their possible future directions.
Explore related subjects
- Artificial Intelligence
Avoid common mistakes on your manuscript.
1 Introduction
The speedy development of technology and Internet of Things (IoT)-based devices in organizations and enterprises give rise to progressive increases in various types of data. IoT has become a vital part of human life and it can be sensed in our day-to-day activities. It was said by Kumar et al. ( 2019 ) that IoT is a revolutionary approach that has changed numerous aspects of human life. It makes our lives easy and secure by handling various applications of smart city societies including pollution control , smart transportation , smart industries , smart home security systems , smart water supply , and many more systems. The small amount of data accumulates and gives rise to Big Data which is stored, processed, and analyzed by a set of technologies. Big Data is a large volume of data generated by IoT sensors , servers , social media , and medical equipment, etc . Cloud computing is internet-based computing that enables inexpensive, reliable, easy, simple, and convenient accessibility to the resource (Albugmi et al. 2016 ). Cloud computing provides service, and reduces infrastructure maintenance overheads. Apart from this it also provides better performance to the end users and flexibility for storing data over the cloud. However, storing highly confidential Big Data obtained from IoT devices , medical data , and server data over the cloud may pose threats to attackers. Therefore, data security is a most important concern when a large or bulk of confidential data is to be stored in the cloud (Sumithra and Parameswari 2022 ).
Cyber attacks target IoT devices that impact stakeholders, and they may damage physical systems, m-health, and economic systems severely. Earlier events show that IoT devices hold numerous vulnerabilities. Many manufacturers struggle to protect IoT devices from vulnerabilities (Schiller et al. 2022a ). Cloud computing integrates distributed computing, grid computing, and utility computing to establish a shared virtual resource pool (Sun 2019 ). There are privacy and security issues in these cases because the owners have no control over the information and tasks carried out on the platform. Various privacy protection methods have been introduced such as encryption , access control , cryptography , and digital signature but they are not strong enough, as a result, attackers easily break through the security wall and harm the data over the cloud.
The authors of the research papers reviewed various methods and suggested some measures and directions to protect the data in cloud computing and edge computing environments (Ravi Kumar et al. 2018 ; Zhang et al. 2018 ). Through this study, the author found that data privacy , data remoteness , data leakage , and data segregation are crucial problems that may exist. The survey paper (Hong-Yen and Jiankun 2019 ) addressed modern privacy and preserving models to focus on numerous privacy-interrelated frameworks to be implemented in practice.
As a contribution, the current paper aims to accomplish the following objectives:
To examine existing security frameworks , standards , and techniques that incorporate different standards across multiple areas of cloud-IoT technologies.
To explore and discuss open-ended challenges in a Cloud-IoT-based environment concerning securities and privacy.
To present and discuss the classification of challenges in Cloud-IoT environments after evaluating the performance of existing literature. It also provides solutions for the identified open-ended challenges and addresses future security concerns related to Cloud-IoT technologies.
The following are the Research Questions ( RQs ) that the researchers tried to investigate through the current research paper:
RQ 1 : To Investigate how IoT , Big Data , and Cloud computing technologies are interconnected, and how security can be a major concern when data is stored in a cloud environment.
RQ 2 : What are the security objectives for the data security and privacy domain?
RQ 3 : What are the privacy concerns for end-users in cloud-IoT-based environments?
RQ 4 : What is the role of edge computing in enhancing privacy in a cloud-IoT environment?
RQ 5 : What are vulnerabilities that exist in the cloud-IoT infrastructure?
RQ 6 : What are the current research trends and areas of focus?
RQ 7 : What are Advancements in security threat detection and avoidance ?
RQ 8 : How machine learning can be a useful tool in detecting vulnerabilities within a cloud-IoT environment?
RQ 9 : How can blockchain technology be an effective measure of data security and privacies?
RQ 10 : What are Current Issues in Data Security and Privacy?
Regarding the remaining portion of the document, Sect. 2 describes the methodology of this research work. Section 3 discusses the characteristics of a research paper and explains how the current paper differs from others. Section 4 talks about security goals in the Cloud-IoT environment. Section 5 discusses the taxonomy related to Cloud-IoT environment which includes Big Data and IoT along with its applications in various domains. Section 6 is a comprehensive study of various attacks in the Cloud-IoT environment. Section 7 (A) explores the study of various research trends through Table 1 . Section 7 (B) describes attack vectors and mitigation strategies through Table 2 . Section 8 presents an in-depth analysis of digital forensics. Section 9 talks about the machine learning and Blockchain technologies-based approaches used for threat detection and recovery. Section 10 covers the current challenges in data security and privacy, and it provides a brief description of possible solutions listed in Table 3 . Further, this section highlights the research gaps identified by the author in Table 4 . Conclusions and future research work are discussed in Sect. 11 .
2 Methodology: a systematic approach
The methodology is the systematic approach that is used by the author to conduct research, analyze the data, and frame conclusions. The methodology section covers the boundary area of methods and approaches that are followed by the author to write the current research paper. The methodology of this research paper is as follows: To examine IoT security challenges and threats author searched numerous kinds of literature on IoT security. For this keyword IoT, Cloud-IoT security was used for standard survey papers that were published in reputed journals like IEEE, Elsevier, Springer, and many more. After completing this task, the author examined numerous techniques and methodologies presented in those survey papers critically analyzed the facts, and algorithms, and selected a set of relevant topics that is important from a security perspective, provided with the help of the author’s individual experience in the sphere of security. In addition to this, the author introduced various standard approaches that are recognized in the sphere of security for protection against threats. At last, the author utilized Internet-based search techniques to find the most appropriate security products. The Methodology of the current paper is divided into three standard stages as follows.
Phase 1 Identification of the study area, formulation of the research questions, sampling, and establishing the primary search approach or standards.
Phase 2 Using the search strategy or criterion about existing literature, carrying out keyword searches, Boolean searches involving the combination of keywords and phrases with the operators “AND”, and “OR”, and database searches, assessing the results, and formulating selection criteria.
Phase 3 Finding and evaluating approved literature, articles, papers, websites, and web documents by the chosen primary research topic.
Figure 1 shows the distribution of references over the year. The figure portrays which year the researcher’s paper was selected to prepare the current paper. The author selected the previous research paper from year 2016 to 2024, a recently published paper. The author reviewed the paper which includes published journal and conference papers. The author searched, examined, and analyzed the paper was included in the references section of the manuscript.
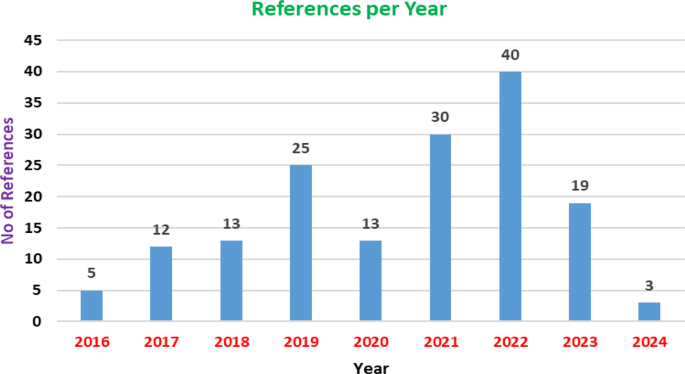
Reference timeline
2.1 Inclusion/exclusion criteria
The inclusion and exclusion criteria aim to identify the research studies that correspond with the questions under investigation. The primary studies were identified using the inclusion criteria that we are presenting. The exclusion criteria were left out since they represent the negative version of the inclusion criteria that were specified.
Inclusion Criteria
IC 1 : Publications released on and after the year 2016.
IC 2 : Publications that have been published in peer-reviewed journals, conferences, workshops, etc.
IC 3 : English-language articles published.
IC 4 : Articles that are required to contain an abstract and title.
IC 5 : Publication that specifically addresses the subject topic such as data security, privacies encryption decryption, machine learning, blockchain, or research problems.
IC 6 : Research with subject-specific keywords included.
IC 7 : Systematic reviews, theoretical analysis, and empirical study.
Exclusion Criteria
EX 1 : Articles that are loosely connected to the research question or do not answer it.
EX 2 : Articles whose complete text cannot be accessed.
EX 3 : Articles not available in English.
EX 4 : Articles that were released almost ten years ago.
EX 5 : Studies with poor ratings or serious methodological errors.
EX 6 : Articles that don’t explicitly address privacy and data security concerns is excluded.
EX 7 : To prevent prejudice from incorporating the same study more than once, remove duplicate publications.
2.2 Algorithms, tools, and techniques Implemented
Alogrithm 1 : RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), and AES (Advanced Encryption Standard) are a few examples of the particular encryption techniques used in the studies.
Alogrithm 2 : Determine which machine learning techniques—such as anomaly detection methods (e.g., k-means clustering, isolation forests)—are utilized to detect data breaches or to ensure data security.
Tool 1 : To manage and organize references, use programs like Scispace, Citation Gecko, and Open Knowledge Map.
Tool 2 : To create visual representations of the data in MS Excel (graph).
Tool 3 : To check Grammar and Spelling Grammarly software tools are used.
Tool 4 : To draw the picture tools such as Paint, Smart Draw, and Origin-Lab are used.
Tool 5 : iThenticate is used for Plagiarism detection.
Techniques for Search
Technique 1 : Use Boolean operators and specified keywords to search IEEE Xplore, Scopus, and Google Scholar. The following query is an example: “data security” AND “privacies” AND (encryption OR data protection) AND “2016–2024”.
3 Advancing IoT, Big Data, and cloud integration: novelty in current research
In the rapidly evolving landscape of technology, the convergence of the IoT, Big Data, and Cloud computing stands at the forefront of innovation. Each domain, when studied individually, offers significant advancements and benefits. However, the integration of these technologies opens up unprecedented possibilities, presenting both opportunities and challenges. This research work provides the novel aspects of combining IoT , Big Data , and Cloud computing . Further, the paper highlights the transformative impact on various industries and emerging security concerns. This study aims to uncover new insights and propose solutions to ensure the safe and efficient deployment of integrated systems by exploring how these technologies interact. The major contributions of the current research paper are as follows:
Integration of IoT, Big Data, and Cloud Computing : The paper examines the combined effects and security threats of integrating IoT, Big Data, and Cloud computing.
Role Analysis : It offers an in-depth analysis of how IoT, Big Data, and Cloud storage work together.
Data Flow : The paper explores the process where data generated from IoT devices becomes Big Data and is subsequently stored in the Cloud.
Security Threats : It highlights the potential security threats during the transmission and storage of data.
Proposed Protections : The authors propose standard approaches to protect against potential attacks that could compromise the data.
Digital Forensics : The paper discusses digital forensics as a method to preserve and analyze digital data post-attack, aiding in tracing the attacker’s footprint and identifying patterns and trends.
Recent Data Security Technologies : In this research work, the authors addressed new technologies that have the potential to significantly reduce threats in cloud-IoT environments.
Research Focus : Authors determine the researcher’s field of expertise methodically.
4 Security goals in Cloud-IoT environments: a comprehensive overview
Security in Cloud-IoT environments is paramount due to the interconnected nature of devices and the vast amount of sensitive data they generate and process. Ensuring the confidentiality, integrity, and availability of data and services has become a major challenge as cloud computing and IoT devices become more integrated into everyday life and vital infrastructure. In an ever-changing digital ecosystem, this comprehensive overview seeks to explore the major security objectives, difficulties, and tactics that are crucial for protecting Cloud-IoT environments.
Figure 2 shows security objectives in a cloud environment. To guarantee the confidentiality, integrity, availability, and general security of data, applications, and resources hosted in the cloud, security objectives for a cloud environment are essential. These goals assist businesses in defining their security objectives and directing the application of suitable security solutions. For the confidentiality, integrity, and availability of data and services hosted in the cloud, security objectives for the environment are crucial. These goals aid organizations in developing a framework for putting security measures in place and in defining their security objectives. To respond to changing threats and keep a solid security posture in the cloud, it is essential to regularly assess and update security goals and procedures.
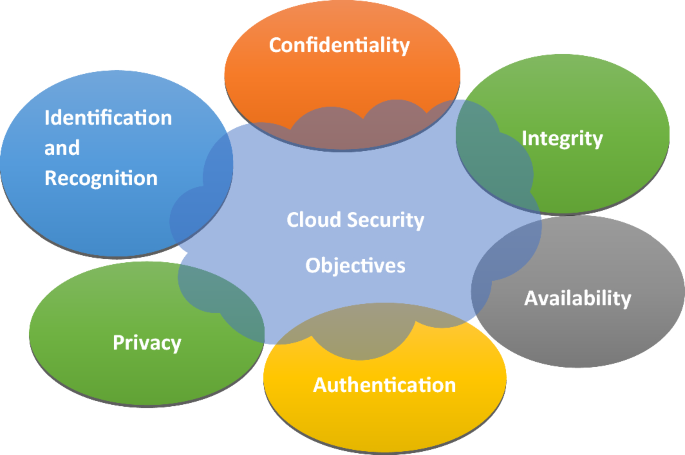
Security objective in cloud environment
Confidentiality Confidentiality refers to safeguarding or protecting critical data from unauthorized access. The information will only be revealed or accessible to those persons who are authorized (Schiller et al. 2022a ).
Identification and Recognition Identification is a unique way to provide attributes to users or devices to differentiate from other users. Recognition is related to the validation of the claimed identity. When a user gives a password, it matches with the saved password and identifies an individual (Schiller et al. 2022a ).
Privac: To safeguard the privacy of individual data, security measures are implemented. It also ensures that data must be responsibly handled. It involves protecting personnel information (Schiller et al. 2022a ).
Authentication: The authentication measures procedure involves confirming the identities of individuals and protecting against unauthorized access. It involves the user providing a username and password (Schiller et al. 2022a ).
Availability Availability refers to the accessibility and usage of data when required by an authenticated person. It involves maintaining availability includes protecting against denial of service, downtime, and disruptions that can hamper the availability of data (Schiller et al. 2022a ).
Integrity Integrity ensures that data should be consistent, accurate, and unchangeable throughout its lifecycle. It also ensures the trustworthiness of the data (Schiller et al. 2022a ).
Case studies that demonstrate how these security goals are implemented in practice are described below:
Estonia’s e-Residency Program: e-Residents receive a government-issued digital ID that is stored on a blockchain. This ID allows them to securely sign documents, access Estonian e-services, and run a business remotely.
MediLedger in Pharmaceutical Supply Chain: MediLedger uses blockchain, a decentralized ledger, to ensure data integrity and transparency.
Civic’s blockchain-based identity verification: It allows users to create and verify digital identities. Further, Enigma uses secure multi-party computation ( sMPC ) on the blockchain to ensure that data can be shared and analyzed without being exposed.
5 Taxonomy of Cloud-IoT environment
In the rapidly growing landscape of the Cloud-IoT environment, understanding the taxonomy is significant for navigating the complexities of connected devices and realizing their full potential in the swift diversification of the Cloud-IoT ecosystem.
5.1 The relationship between IoT, Big Data, and cloud computing
There is a strong synergistic relationship between Cloud Computing, Big Data, and the IoT, with each technology augmenting the other’s capabilities. IoT enables data collection which is uploaded to the cloud for storage and processing. These bulk data are accumulated in the cloud and form a large volume of data known as Big Data. Big Data tools and techniques are applied to these bulk data for processing and scrutiny of data on the cloud. Real-time monitoring and analysis are made possible by the convergence of cloud computing, Big Data, and IoT. This makes it possible to respond and act quickly, which optimizes processes, boosts productivity, and enhances user experiences.
Figure 3 illustrates the relationship between the IoT devices that are placed at remote locations. Data is generated from IoT devices which are stored and analysed on the cloud using Big Data tools. Finally, after processing data on the cloud decision is made. IoT, Big Data, and cloud computing work together to create a potent trio that propels efficiency and innovation in a wide range of sectors, including manufacturing, agriculture, smart cities, and healthcare.
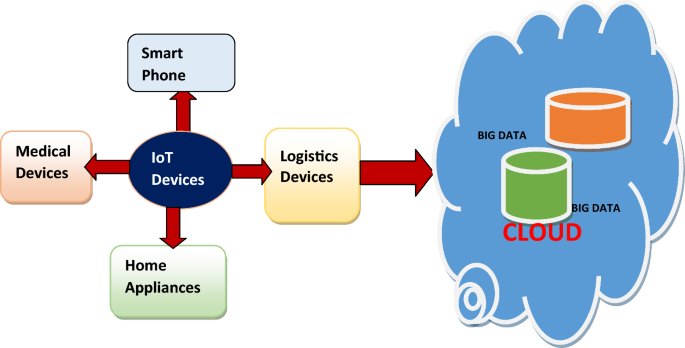
Relationship between IoT, Big Data, and cloud computing
5.1.1 Understanding the dynamics of Big Data
Big Data in a few years come out as an ideal that has provided an enormous amount of data and provided a chance to enhance and refine decision-making applications. Big Data offers great value and has been considered as being a driving force behind economic growth and technological innovation (Dutkiewicz et al. 2022 ). Machines and humans both contribute to data through online records, closed-circuit television streaming, and other means. Social media and smartphones create enormous amounts of data every minute (Ram Mohan et al. 2018 ). Big Data is a large amount of data that is fast and complex. These data are not easy to process using conventional methods. Today Giant Companies substantial portion of the value advanced from data generated by the company which is continually examined to produce better and advanced products. A prime example of Big Data is the New York Stock Exchange, which creates one terabyte of fresh trade data daily. Big Data characteristics are defined by the 4 V’s i.e. Volume, Variety, Velocity, and Veracity which is shown in the figure below. Big Data involves three main actions integration, managing, and analysis.
Figure 4 A and B illustrate the essential 4 V’s i.e. Variety, Volume Velocity, and Veracity of Big Data through 4 blocks. Volume block represents the size of data that grows exponentially such as Peta byte, Exa byte, etc. It represents how much information is present. The volume of data is increasing exponentially. Velocity block shows that data is streaming into the server for analysis and the outcome is only useful if the delay is short. It is used to portray how fast information can be available. Data must be generated quickly and should also be processed rapidly. For example, a healthcare monitoring system in which sensors record the activities that occur in our body and if an abnormal situation occurs needs a quick reaction. Variety blocks represent, a variety of data and various formats, types, and structures of data that exist such as sensor data, PDF, photo, video, social media data, time series, etc. The veracity block ensures that data should be consistent, relevant, and complete in itself. Hence, the error can be minimized accurate results can be produced and decisions can be taken through analysis of the result.
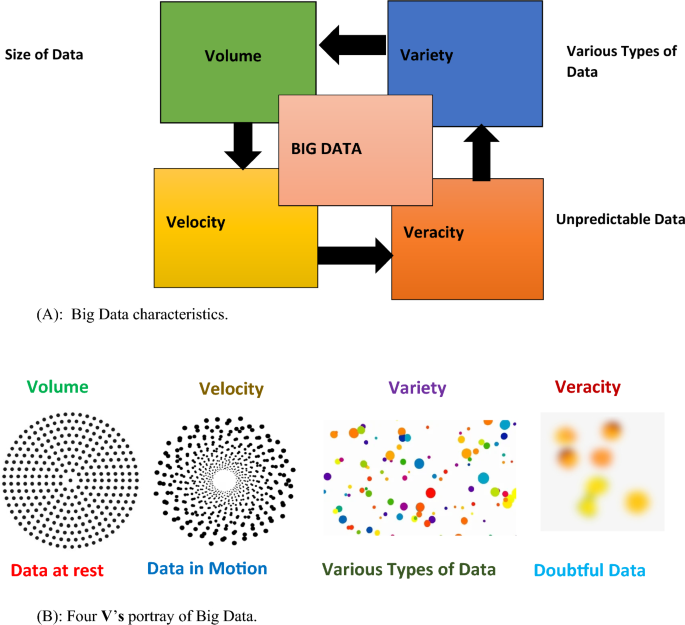
A Big Data characteristics. B Four V’s portray of Big Data
Apart from its several advantages Big Data faces security challenges as well such as attackers can damage or steal information where a large volume of data is stored such as cloud and fog. An attacker can steal data and he/she can attempt to study and analyze data and thereafter can change the outcome of the result accordingly. Therefore special protection and privacy of data such as cryptographic defense mechanisms should be provided so that data can be kept safe and secure (Kaaniche and Laurent 2017 ). The healthcare industry is one of the most promising areas where Big Data may be used to effect change. Large-scale medical data holds great promise for bettering patient outcomes, anticipating epidemics, gaining insightful knowledge, preventing avoidable diseases, lowering healthcare costs, and enhancing overall quality of life. To address security and privacy threats in healthcare, the author has provided some suggested strategies and approaches that have been documented in the literature, while also outlining their drawbacks (Abouelmehdi et al. 2018 ).
5.1.2 Connecting the world: the evolution and impact of the Internet of Things
The development of the Internet of Things has revolutionized the Internet market around the world. The Internet of Things is a device that when connected to the Internet transmits, receives, and stores data over the cloud. The Internet of Things is embedded with several devices such as sensors, physical devices, and software to control the devices. IoT can be device can include anything that contains a UID (Unique Identification Number) that can be used to in identify uniquely over the internet. IoT devices have several benefits such as high efficiency, providing more business opportunities, high productivity, increased mobility, and many more. Apart from the above-mentioned benefits, IoT devices can also be deployed to monitor tool execution and find and diagnose the issues before any major break happens in the functioning of the device, also in addition it reduces maintenance costs and thereby increases the throughput. IoT devices can able to gather large volumes of data beyond any human can think of it. As the world is developing data is considered to be an oil for the development of any country, so to cope with new challenges IoT devices should also be made smarter than traditional devices which can able to guide and make decisions. To achieve such objectives IoT devices should be accompanied by machine learning and artificial intelligence technology to enhance the performance of the device and to make sense of collected data.
Figure 5 illustrates the key components of IoT devices. The components are the building blocks of IoT which is shown in the diagram. These “DGCAU” components collectively facilitate the working of the IoT devices. Each component is significant in terms of productivity, data collection, monitoring, and connectivity. In Fig. 5 ‘D’ stands for IoT Device. IoT devices are those which are such as medical equipment, smart meters, home security systems, smart lights, etc. which are used to collect data. The second ‘G’ stands for Gateway which is similar to a centralized hub that is used to interconnect IoT devices and sensors to the cloud. Advanced gateway facilitates data flow in both directions between IoT devices and the cloud. ‘C’ indicates the cloud aids in the storage of data and simultaneously analyzing data. Rapid processing and strong control mechanisms enable cloud-enabled IoT devices to minimize the risk of attack. User identities and data are protected by strict authentication methods, encryption tools, and biometric authentication in Internet of Things devices. ‘A’ signifies the Analysis of data that was stored in the cloud to determine the outcome. Analysis tool studies large amounts of data and produces useful information, which is helpful in decision-making. The last component ‘U’ represents the user interface or UI module that facilitates the user to administer the IoT device with which they are interacting. it is generally a graphical user interface that includes a display screen, mouse, keyboard, etc.
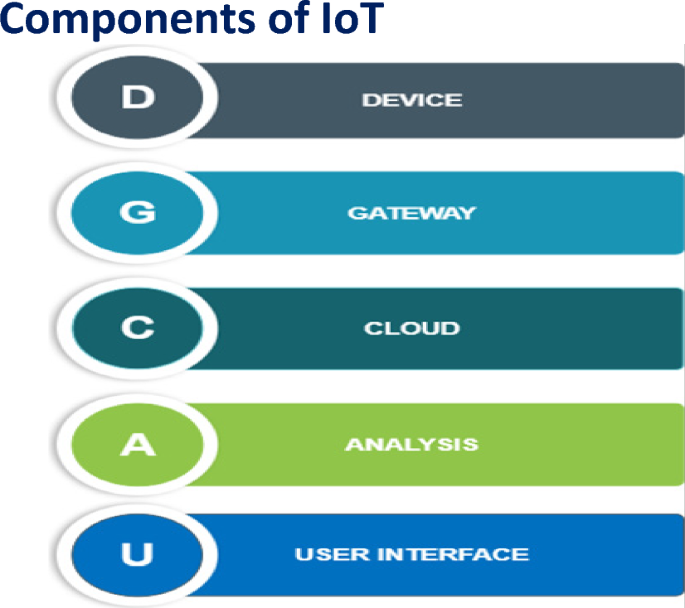
Key components of the Internet of Things
Figure 6 shows the various applications of the IoT which are technology paradigms used to interconnect the devices with the Internet, collect data, share data, transmit data, and act upon data. IoT has enormous application in day-to-day life therefore enabling us to perform our work widely and conveniently . Smart Lighting IoT can be used to operate the light remotely through a smartphone. Transportation IoT is used to track vehicles and goods in real-time. IoT finds application in health which enables doctors to monitor the patients remotely. In Logistics IoT helps to keep track of goods and vehicle devices. IoT is useful for smart framing because IoT sensors can monitor, measure, and track soil moisture, nutrients needed for crop fertilization, and irrigation needs. IoT devices used in retail monitor the department’s real-time inventory level and stock and forward orders when a product is discovered to be out of stock. With features like motion sensors, doorbell cameras, and video surveillance , smart home security systems employ the Internet of Things to monitor and secure houses. IoT is used by smart grids to increase the effectiveness and dependability of electricity delivery. Water quality indicators like pH, turbidity, chlorine levels, and pollutants are continuously monitored by IoT sensors. Smart meters with IoT capabilities allow for real-time monitoring of utility consumption. IoT equipment on autonomous vehicles processes sensor data in real time. This entails reading and assessing the environment to make deft choices regarding safety, navigation, and vehicle control. Wearable gadgets gather information on activities, health, and other topics before sending it for analysis to smartphones or the cloud for processing.
Internet of Things applications
Apart from the benefits of IoT devices in day-to-day life, IoT devices suffer security threats as well. The rapid growth of IoT devices has revolutionized how we interact with technology. As the number of IoT devices increases the security concern also increases simultaneously. The author addresses the issue of sharing sensitive data securely for designated recipients in the context of the Blockchain Internet of Things (B-IoT) (Yin et al. 2022 ). The author has scrutinized the security flaws in computer systems based on cloud, blockchain, IoT, and fog computing (Mishra et al. 2022 ; Yao 2022 ; Abdulkader 2022 ). Security challenges and threats in IoT and cloud environments addressed by various authors are presented in the papers (Pandey et al. 2023 ; Ray and Dutta 2020 ; Bedi et al. 2021 ). Cloud Computing and IoT Using Attribute-Based Encryption approaches are developed by authors found to be very effective in the security domain (Mihailescu et al. 2022 ; Henze et al. 2017 ). The author presents D-CAM, a solution for achieving distributed configuration, authorization, and management across borders between IoT networks (Simsek 2023 ). The study presented by the author is a novel handshake protocol for the broker-based publish/subscribe paradigm in the Internet of Things that offers key exchange-based authentication, authorization, and access control (Shin and Kwon 2020 ; Stergiou et al. 2018 ).The goal of a systematic literature review (SLR) paper is to examine the body of research on cloud computing security, risks, and difficulties that are presented by authors (Wang 2021 ). The primary issue in the cloud environment has been confirmed to be data access, despite the security measures being deemed dependable (Javid et al. 2020 ; Gai et al. 2021 ; Shukla 2022 ). We suggested an effective data access control method that uses optimal homomorphic encryption (HE) to get around this issue (Gnana Sophia et al. 2023 ). The paper highlights the edge computing security and privacy requirements (Yahuza et al. 2020 ). Multiple encryption techniques are presented by the authors which are significant in protecting privacy and data security (Sharma et al. 2019 ; Silva et al. 2018 ; Bertino 2016 ). The author proposes a distributed machine learning-oriented data integrity verification scheme (DML-DIV) to ensure the integrity of training data (Zhao and Jiang 2020 ). The researcher introduced an identity-based (ID-based) RDIC protocol including security against a malicious cloud server which is presented in the paper (Yu et al. 2017 ; Sookhak et al. 2018 ). The authors studied various security challenges concerning IoT devices, Big Data generated by IoT devices, and cloud and presented them in the paper (Akmal et al. 2021 ; Awaysheh et al. 2022 ; Tang 2020 ; Shi 2018 ).
5.2 Navigating the cloud: exploring the world of cloud computing
Cloud Computing refers to Internet-based computing, where shared resources data, software, and information are to the customer and devices on demand. The term “cloud” used to appear on the Internet. Huge memory space and inexpensive, high-performance computing are made possible by the cloud computing paradigm. Users can get cost savings and productivity benefits to manage projects and develop collaborations by moving their local data management system to cloud storage and utilizing cloud-based services. Information and knowledge extraction is greatly aided by computing infrastructure, particularly cloud computing. The services for cloud computing are provided using the network, generally the Internet. The characteristics of cloud computing include broad network access, on-demand service, rapid elasticity, and many more. With the help of the cloud, numerous services are accessible to clients. Broadly there are three types of services offered that enable the client to use software, platform, and infrastructure. Several types of cloud can be subscribed to by anyone as per the requirement of an individual or any organization. These include private cloud, public cloud, and hybrid cloud. Private cloud solely owned by any business houses. In this type of cloud infrastructure software is preserved on a private network and hardware and software entirely belong to the organization. Public clouds are commonly cloud services that are allotted to various subscribers. Third-party owned and operated the cloud resource.
The public cloud is mostly used for online office applications, testing, development, etc. A hybrid cloud is a combination of public and private clouds, which is implemented by a couple of interrelated organizations. Common types of cloud services are presented through the 3-layer architecture of Cloud Services in Fig. 7 and each one is discussed.
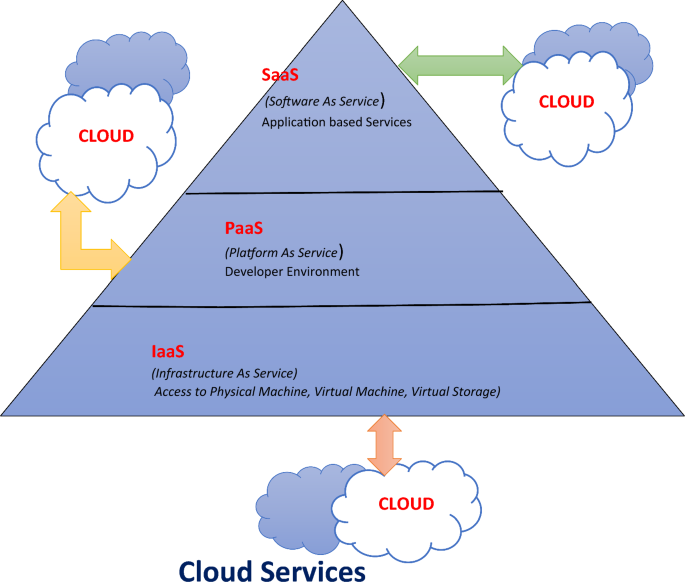
3-Layer architecture of cloud services
Figure 7 exhibits the different types of cloud and services provided by the cloud. The figure conveys the three-layer architecture of the cloud. IaaS makes virtualized computing resources available via the internet, enabling customers to pay-as-you-go access and manage the essential parts of the infrastructure. These resources often include storage, networking, virtual machines, and other things. Platform as a Service (PaaS) is a cloud computing architecture that offers developers a platform and environment to create, deploy, and manage applications. PaaS provides a variety of tools and services that speed up and improve the efficiency of the application development process. A cloud computing approach called Software as a Service (SaaS) allows users to access software programs online. SaaS has many benefits, including affordability, scalability, and accessibility.
Because crucial data is processed and stored on the cloud, for instance in Internet of Things applications, it also poses security and privacy issues (Alouffi et al. 2021 ; Hamzah Amlak and Kraidi Al-Saedi 2023 ; Yu et al. 2022 ). Cloud security is an important area where authors have tried to find the best possible solution through their research they have highlighted the challenges of possible solutions to the problem through finding and investigation in the paper (Gupta et al. 2022 ; Chaowei et al. 2017 ; Wang et al. 2021 ).
To ensure the integrity of data kept in the cloud, the author’s study proposes an effective public auditing technique that makes use of Third third-party auditor (TPA) (Reddy 2018 ; Hiremath and Kunte 2017 ; Yan and Gui 2021 ). The author proposes an efficient certificate-based data integrity auditing protocol for cloud-assisted WBANs (wireless body area networks (Li and Zhang 2022 ). The author proposed a secure architecture by associating DNA cryptography, HMAC, and a third-party auditor to provide security and privacy (Kumar 2021 ; Duan et al. 2019 ). Adversaries are always coming up with new ways to get access to users’ devices and data through developing technologies like the cloud, edge, and IoT. The author discussed various attacks along with security solutions (Pawlicki et al. 2023 ). The paper highlights the research challenges and directions concerning cyber security to build a comprehensive security model for Electronic health records (Chenthara et al. 2019 ; Hou et al. 2020 ; Ishaq et al. 2021 ; Jusak et al. 2022 ). The author mentioned the research and analysis of privacy-preserving data mining (PPDM) and classified using various approaches for data modification in the research paper (Binjubeir et al. 2020 ).
Even with all the benefits mentioned, there are security and privacy issues while using cloud computing (Nanda et al. 2020 ; Himeur et al. 2022 ). The issue of data security and privacy for Big Data is complicated by the use of cloud computing for Big Data management, storage, and applications. Since cloud services are typically offered on a common infrastructure, there is always potential for new attacks, both internal and external, such as password theft or application programming interface (API) flaws. The author has proposed a software architecture model by using approaches like hardware security extensions (Intel SGX) and homomorphic encryption. To improve data security in large data cloud environments and defend against threats, a virtualization design and related tactics are suggested by the author. The TID (Token Identification) model developed by the author provides security to the data. The user has various access rights as a client. The authentication access token establishes a connection with the user account after the user logs into the cloud network. The researchers have developed the Remote Data Checking (RDC) technique, which uses the sampling technique to evaluate the integrity of data that is outsourced across remote servers. Authors developed the techniques for remote data auditing that are very beneficial in ensuring the integrity and dependability of the data that is outsourced. Data, auditing, monitoring, and output these elements are all included in the DAMO taxonomy. The author in his paper offers a unique security-by-design framework for the implementation of BD (Big Data) frameworks via cloud computing (Big Cloud) (Ye et al. 2021 ). Various data security issues in the Big Data cloud computing environment are addressed by the authors in his paper. Various methods for safeguarding privacy and data security in public clouds are covered in the article (Jain et al. 2016 ). A multi-cloud architecture with privacy and data security enabled is suggested by the author. To increase user security on SNg (Social Networking) by utilizing techniques that can give data about BD technology (Big Data) greater privacy. This approach is described by the author in the paper along with various metrics and usage-related outcomes. The author examines financial risk analysis and related regulatory studies using blockchain and Big Data technologies. A secure cloud environment can be achieved by using a hybrid cryptographic system (HCS), which combines the advantages of symmetric and asymmetric encryption.
Figure 8 shows a hierarchical structure created to handle and process data and applications efficiently depending on how close they are to the user or the source of the data. “Hierarchical edge computing” refers to the interplay between these three layers, cloud, fog, and edge. The Cloud Layer is a centralized data processing center that provides abundant computing and storage capacity for handling and storing enormous volumes of data as well as running sophisticated applications. The growths of the Internet and its associated ideas, such as edge computing, cloud computing, and the Internet of Things, have had a permanent impact. The cloud layer is a highly scalable data center that is perfect for managing large-scale applications and services because they can extend horizontally to manage increased workloads.
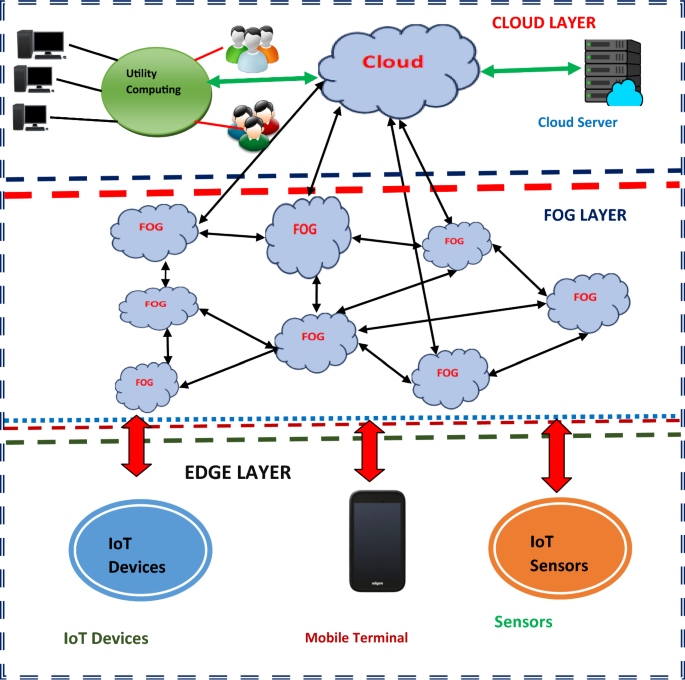
Hierarchical edge computing
The fog Layer is an intermediate layer after the cloud layer which spreads and distributes processing responsibilities among several local servers or devices, which can be very useful for IoT applications with many data sources. Fog computing is ideal for latency-sensitive applications that demand quick responses. Virtual components called cloudlets are employed in fog computing. Fog computing has emerged as a promising paradigm in overcoming the growing challenges (e.g., low latency, location awareness, and geographic distribution) arising from many real-world IoT applications, by extending the cloud to the network edge. To facilitate data offloading and computation, these virtual computers offer a micro data centre close to mobile devices (Lu et al. 2020 ). Fog computing offers new insights into the extension of cloud computing systems by procuring services to the edges of the network. It shortens the time it takes for data to go to the cloud and back by processing it closer to the source. The edge layer, which is frequently located adjacent to IoT medical devices themselves (Muzammal et al. 2018 ), is the one that is nearest to the data source or end users. A promising paradigm that expands on cloud computing capabilities is edge computing. It processes data instantly, allowing for extremely quick replies devices, sensor devices, and industrial machinery, mobile terminals are examples of edge devices that can function autonomously and make decisions in the present without relying on a central cloud infrastructure (Ghaffar et al. 2020 ; Jiang et al. 2016 ). Big Data applications are a risk for cyber security assaults, as these attacks directly affect applications utilized across several sectors, such as Big Data analytics. The authors presented a novel data encryption approach, which is known as Dynamic Data Encryption Strategy (D2ES) to protect and safeguard the data which proves promising in cloud computing. Encrypted data can be obtained by cryptography methods, enabling secure communication links within the networking system. Researchers suggested the blockchain-based Shamir threshold cryptography solution for IIoT (Industrial Internet of Things) data protection. An improved data security in mobile edge computing, the Fine-Grained Access Control mechanism (FGAC) is suggested to guarantee data security during data access (Ahmed et al. 2021 ).To analyze and investigate the data reduction at the fog level, researchers attempted to create a model. This researcher has successfully applied methods including artificial intelligence, principal component analysis (PCA), and the Naïve Bayesian classifier for data reduction.
6 Exploring the complex landscape of Cloud-IoT threats: an in-depth analysis
Security concerns are growing along with the integration of Cloud Computing and the IoT. Numerous dangers and vulnerabilities that might compromise the availability, confidentiality, and integrity of data and services are brought about by the junction of these two technologies. We examine the subtleties, possible effects, and vital necessity of strong security measures to protect against changing hazards in interconnected environments as we delve into the complex nature of Cloud-IoT security concerns in this analysis.
Figure 9 illustrates the numerous types of attacks that can take place in the cloud. These Attacks can harm the cloud service provider as well as cloud customers. The attacker is an individual who attempts to use a cloud infrastructure, platform, or service’s vulnerabilities or flaws for nefarious reasons in the world of cloud computing. Because they frequently house significant data and offer computational resources that may be used for a variety of purposes, such as launching cyber-attacks, stealing confidential information, or causing disruption, cloud systems are very alluring targets for attackers. For different purposes, including data theft, service interruption, or resource exploitation, attackers target cloud environments. To breach cloud systems, attackers use a range of methods and tactics. These attack methods can include insider threats, sniffer attacks password change SQL-Ingestion, Eavesdropping, malware, distributed denial-of-service (DDoS) attacks, phishing, and more (Basit et al. 2021 ; Ullah et al. 2019 ; Jahromi et al. 2021 ).
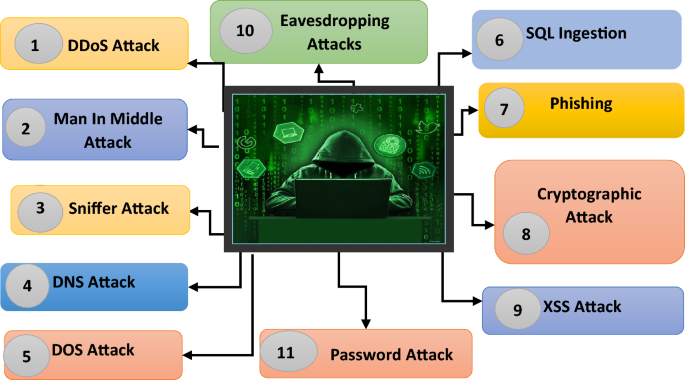
Threats in cloud computing environment
DDOS Attack A distributed denial-of-service attack aims to disrupt regular network operations by flooding the network with traffic. Denial-of-service attacks aim to prevent end users from accessing the network.
Man-in-Middle Attack In a man-in-middle attack, the attacker generally modifies the conversation between the two parties. In a man-in-the-middle attack, attackers generally eavesdrop on sensitive information and alter the conversation. The integrity and security of sensitive data are seriously threatened by MitM attacks.
Sniffer Attack It is an attack in which an unauthorized person intercepts and gains control over network traffic. The goal is to capture and examine the data when it passes over the network.
DNS Attack The domain name system attacks the domain name system, which is responsible for converting human name readable to IP address. DNS attacks have the potential to affect the DNS infrastructure’s availability, integrity, and confidentiality, which could cause interruptions to internet services.
DOS Attack A Denial of Service (DoS) assault involves the exploitation of a single source, typically a compromised device or computer, to overwhelm a target’s resources and cause a loss of service.
SQL Ingestion In SQL (Structure Query Language Ingestion), attackers ingest harmful code inside the parameters of a web application. The main goal of attackers is to manipulate SQL databases. In this type of attack, the attacker gains the advantage of bad input, which enables the attacker to execute the SQL command.
Phishing Attack In Phishing attackers use some trick to expose delicate information, for example, username, personal information, password, and credit card details. Phishing attacks sometimes use the personas of reliable companies, banks, or websites to trick people into doing things that could jeopardize their security.
Cryptographic Attacks Cryptography is important to ensure confidentiality and integrity and authenticate the user. The attacker exploits vulnerability or weakness in the existing system. Attackers compromise the security of cryptographic systems.
XSS Attacks Cross-site scripting (XSS) is one of the serious attacks that occur when vulnerable code which is in the form of a script is injected into the web page of the user. The objective of the attacker is to steal sensitive information about the user by running the scripting code in the user’s browse.
Eavesdropping Attacks Eavesdropping is a kind of attack in which attacker unauthorized person tries to listen to or sniff the conversation between two people and steal information. In this type of attack, the attacker even manipulates the information.
Password Change Request Interception Attack The assailant attempts to intercept legitimate users’ password changes. Interception of this kind could happen during a browser-server conversation.
7 Exploring research trends and areas of focus
As technology continues to evolve at a rapid pace, researchers and academics are continually exploring new trends and areas of focus within their respective fields. To keep ahead of new difficulties, seize opportunities, and encourage innovation, this investigation is essential. We explore the current research trends and areas of attention in a variety of disciplines in this overview, offering insight into the cutting-edge subjects that are influencing the direction of technological and scientific advancement. After scrutinizing the number of published research papers we came across various domains in which researchers have worked and proposed various security frameworks.
Table 1 represents the research work and focus of various researchers in field security. From the table above it can be concluded that researcher have focused on Cloud Computing and their finding are more concentrated on Cloud security and the Internet of Things. The researcher primarily focused on the development of security algorithms to protect the data from being damaged or corrupted by cyber attackers. Through study, it was found that researchers have developed innovative techniques by making use of machine learning techniques, and blockchain technology to safeguard data developed for the Internet of Things.
Cryptography is another eminent way to protect our data. Researchers have created algorithms to encrypt and decrypt data prominently so that data can be safely transmitted over the network. A method like PSEBVC: Provably Secure ECC and Biometric Based Authentication Framework is developed by the author as a countermeasure for attacks.
In the digital landscape, the risks of cyber-attacks are growing enormously which is becoming a challenge for both organizations and individuals. A comprehensive examination of attack vectors and mitigation strategies is essential for understanding and effectively countering these attacks (Wylde et al. 2022a , b ). Through an analysis of numerous attack pathways and related mitigation techniques including artificial intelligence-based solutions discussed in paper (Al Hamid et al. 2017 ; Abed and Anupam 2022 ). This research paper aims to offer important insights on how to enhance security and defend against cyber threats in a constantly changing security environment. The objective of this analysis is to provide individuals and organizations with the necessary knowledge and tools to improve their digital security and minimize risks in the constantly changing threat landscape. To do this, each attack mechanism is thoroughly examined, and appropriate remedies are explored through Table 2 .
Table 2 is a complete description of the investigation of the several research papers related to security threats that exist, various categories of attackers that occur on the cloud, and countermeasures that can be taken to prevent attacks summarized in the Table by the author. The table shows how attacks affect the data and what standard approaches were developed by researchers to protect data.
8 Unveiling the intricacies of digital forensics in Cloud-IoT environments
Digital Forensics is a branch of forensic science that concentrates on recovery of data, analysis of data and exhibit the digital evidence that is found on electronic devices. The IoT Forensics can be identified as part of Digital Forensics. The objective of IoT Forensics is to explore digital information in an authorized manner. IoT forensics data can be accumulated through IoT devices, sensors, networks, and cloud. There are some differences between security, IoT, and forensics. The protection against physical and logical security threats is provided by IoT security adopts multiple methods to protect from threats and minimize attacks (Unal et al. 2018 ). Forensics examines the data present in the devices and recreates the happenings by utilizing investigative methods to preserve and analyze digital data. Post-mortem examinations are the main focus of forensics i.e. discovering shortcomings that emerged from the event. Forensic experts obtain digital proof throughout the actual event with the help of standard approaches used in forensic analyses of physical proofs of electronic data to determine and reframe the events by storing and analysis of digital information using different methods of investigation. Some authors have presented detailed studies to investigate the forensic issues in cloud computing and provide possible solutions, and guidelines, including existing case studies (Morioka and Sharbaf 2016 ; Al-Dhaqm et al. 2021 ). The paper offers an enhanced blockchain-based IoT digital forensics architecture that builds the Blockchain’s Merkle tree using the fuzzy hash in addition to the traditional hash for authentication (Mahrous et al. 2021 ). Authors Almutairi and Moulahi ( 2023 ) trained models locally using federated learning on data stored on the IoT devices using a dataset created to simulate attacks in the IoT environment. In order to make the blockchain lightweight, the authors next carried out aggregation via blockchain by gathering the parameters from the IoT gateway (Almutairi and Moulahi 2023 ).
The IoT has revolutionized various sectors through seamless device interactions, yet it has introduced significant security and privacy challenges. Traditional security measures often fall short due to IoT’s distinct characteristics like heterogeneity and resource limitations. Danish Javed et al. ( 2024a ) explored the synergy of quantum computing, federated learning, and 6G networks to bolster IoT security. Quantum computing enhanced encryption, while federated learning preserved data privacy by keeping training data on local devices. Leveraging 6G’s high-speed, low-latency capabilities allows for secure, real-time data processing among IoT devices. The study also reviewed recent advancements, proposed a framework for integrating these technologies, and discussed future directions for IoT security. Recent innovations in network communication have revolutionized the industrial sector with automatic communication through the Industrial Internet of Things (IIoT) . Despite its benefits, the increased connectivity and use of low-power devices in IIoT heighten vulnerability to attacks, and its diverse nature complicates centralized threat detection. To tackle this, authors Javed et al. ( 2023 ) proposed a fog-based Augmented Intelligence (IA) defense mechanism that uses GRU and BiLSTM deep learning classifiers for anomaly detection and secure communication. This framework (Cu-GRU-BiLSTM), which achieved up to 99.91% accuracy, surpassed existing threat detection methods, proving its effectiveness for securing IIoT environments (Javeed et al. 2023 ).
Further, the hybrid approach proposed by Danish Javed et al. ( 2024b ) enhances intrusion detection in federated learning (FL) for IoT by addressing existing limitations. Here, CNNs identify local intrusion patterns by extracting spatial features, while BiLSTM captures sequential patterns and temporal dependencies. Using a zero-trust model, data stays on local devices, and only the learned weights are shared with the centralized FL server. The server then combines updates to improve the global model’s accuracy. Tests on CICIDS2017 and Edge-IIoTset datasets show this method outperforms centralized and federated deep learning-based IDS.
9 Advancements in security threat detection and avoidance
With the constant advancement in sophistication of cyber attacks, enterprises, and individuals alike are obliged to use innovative methods and technologies to detect, prevent, and mitigate potential security breaches. Threat detection is seeing tremendous breakthroughs, enabling defenders to keep one step ahead of malicious actors. These advancements include machine learning algorithms and behavior analysis methodologies. This ongoing change emphasizes how crucial it is to take preventative action to protect sensitive data and maintain digital trust in an environment where dangers are becoming more complicated.
9.1 Harnessing the power of machine learning
Machine learning is a subset of artificial intelligence (AI) that focuses on developing models and algorithms that enable computers to learn from data and make decisions or predictions without having to be explicitly programmed to do so. As a result, machine learning algorithms are beneficial when dealing with vast amounts of data since, after being trained on the data (Ali et al. 2020 ), the trained model uses its learning experience to present precise outcomes on new data. Data generated by IoT devices may suffer from threats (Safaei Yaraziz et al. 2023 ). Today Machine Learning proves to be one of the strongest tools to identify threats and maintain the integrity of data in transmission. The foundation of machine learning is the algorithms that are used to train the models. The first step in using machine learning to address a problem is gathering data. Next come tasks like data preparation, data analysis, training, testing, and eventually deploying the model for real-world application. Two types of ML problems can be solved by supervised machine learning algorithms: regression and classification. Classification is used to solve problems with binary target variables ( yes / no ), while Regression ML algorithms are used to address problems of similar nature when the target variable is continuous. A phishing attack has become one of the most prominent attacks faced by internet users, and governments. The attacker(s) transmits URL(s) to the intended victims via text messaging, social networking, or spam messages. They do this by mimicking the behavior of authentic websites when creating website pages. Malware attack during data in transit is a common type of attacks that can manipulate the data and damage the data. To prevent such attacks ML model can be one of the tools to identify such attacks and prevent them to such extents. Machine Learning algorithms have been used to build several intrusion detection systems, improving the systems’ ability to identify threats and enabling uninterrupted business operations (Pathak et al. 2023 ). Despite many benefits that SDN(Software-Defined Networking) offers such as offer nimble and adaptable network growth, malicious attacks that can eventually prevent network services are unavoidable (Unal et al. 2018 ). Machine learning has been used in several studies to detect distributed denial of service (DDoS) threats in SDN (Software-Defined Networking) environments (Morioka and Sharbaf 2016 ). ML models are being trained on numerous datasets to build models that can detect cloud attacks with elevated accuracy. Various classifier is implemented in the ML model to identify attacks such as SVM, Decision tree, K-NN (K-Nearest Neighbour), Convolutional Neural Networks (CNNs), Recurrent Neural Networks (RNNs), random forests, and many more. The use of random forest and K-NN classification approaches enables malware detection method proofs to be 99.7% accuracy and 99.9% in several cases (Abed and Anupam 2022 ; Morioka and Sharbaf 2016 ). These classifiers can be used with different feature engineering and feature selection strategies to create machine learning models that effectively handle certain security issues and enhance overall cyber security posture.
Figure 10 represents security threat detection using machine learning algorithms and models. The automatic detection of potential security threats and abnormalities within a file system using machine learning techniques uses a predictive model to identify the threat and classifies it as a malware file or harmless file over the system. Data breaches and other security problems can be prevented because of their ability to assist enterprises in detecting and responding to threats more quickly and effectively. In this process, it involves two important stages. The first stage is the Training stage where the model is being trained using different files. Files are sent as input to train the model. Numerous machine learning algorithms, such as decision trees, random forests, support vector machines (SVM), neural networks, and others, can be used for training the model. After the model is trained, then comes to the security stage where an unknown file is given to the model for analysis the file. For the detection of security threats, supervised learning techniques like classification and regression are frequently used. The machine learning model generates notifications for security professionals to investigate when it spots a potential security danger or abnormality. Automated responses to lessen or control the crisis may also be triggered based on how serious the threat is. Deep learning approach is used to detect pirated software and malware-infected files across the IoT network. Using color picture visualization, the deep CNN is utilized to identify harmful infections in Internet of Things networks. Secure video transmission over the cloud is discussed in the paper (Hossain et al. 2018 ). Researchers have developed Holistic Big Data Integrated Artificial Intelligent Modelling (HBDIAIM) to provide and improve privacy and security in data management (Chen et al. 2021 ). The previously developed model falls short in providing adequate data privacy and security, keeping this shortcoming in mind author (Yazdinejad et al. 2024a ) developed an Auditable Privacy-Preserving Federated Learning (AP2FL) model tailored for electronics in healthcare. AP2FL model provides secure training and aggregation processes on the server side as well as the client side. Thereby protecting and minimizing the risk of data leakage. Researchers primarily focus on Machine learning-based threat detection models to address the challenges within Consumer IoT. Using Federation Learning (FL) techniques data privacy in Consumer IoT is maintained (Namakshenas et al. 2024 ). The author suggests an approach to attack detection that makes use of deep learning (DL) algorithms to identify false data injection (FDI) assaults (Sakhnini et al. 2023 ). In the research paper, the author utilizes federated learning to automatically search for threats in blockchain-based IIoT (Industrial Internet of Things) networks using a threat-hunting framework we call block hunter (Yazdinejad et al. 2022 ).
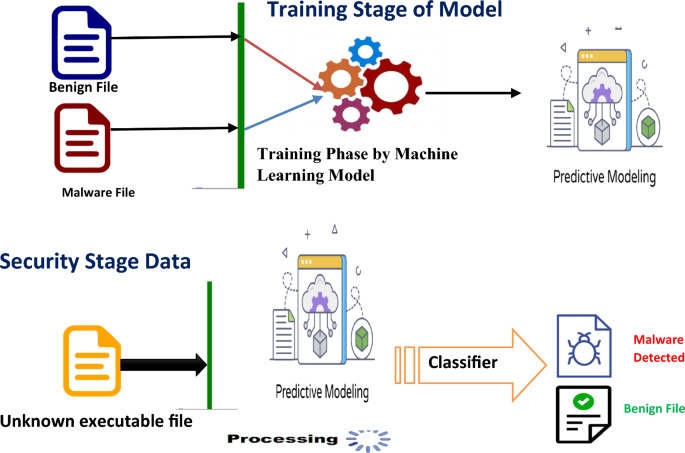
Security threat detection using machine learning technique
Real-life applications of machine learning in malware detection
AT&T Uses machine learning to protect networks and find malware that targets telecom infrastructure.
Mayo Clinic A healthcare organization that implements machine learning techniques to safeguard patient data from malware attacks and unauthorized access.
Bank of America Employs AI and machine learning to improve cyber security safeguards, identifying malware and averting breaches in data.
Cylance A cyber security firm that heavily relies on machine learning to identify and eradicate malware. To identify threats instantly, its algorithm is trained on an extensive dataset of both malicious and benign files.
Amazon Web Services (AWS) AWS uses machine learning techniques to identify threats, examining the logs and network traffic.
Symantec An American consumer-based software company that employs machine learning techniques to identify and categorize malware.
National Security Agency (NSA) To improve national cyber security, the National Security Agency (NSA) uses cutting-edge machine learning algorithms to identify and analyze malware.
9.2 Unlocking the power of blockchain: a cutting-edge safeguard technique for enhanced security in the digital landscape
Blockchain is an emerging decentralized technology that securely stores and authenticates transactions across a network of computers. Its decentralized and open structure makes it a viable option for many companies looking to improve digital security, efficiency, and trust. Although cloud computing is becoming more and more popular for processing and storing data, security, and privacy are still big issues because of the possibility of hostile assaults on wireless and mobile communication networks. Data transfer privacy and system security are improved by using blockchain technology. To put it briefly, a blockchain is auditable, can function as a distributed ledger with digitally signed data, and allows changes to be tracked back to the original data to ensure security. This demonstrates that the security of data may be guaranteed by blockchain technology (Safaei Yaraziz et al. 2023 ). The suggested IAS protocol is developed on top of blockchain technology to guarantee the security and authenticity of data transmission in cloud computing. A potential solution to the security and privacy problems in the Internet of Things is blockchain technology (Williams et al. 2022 ; Waheed et al. 2020 ). For every transaction including proper authentication, data can pass through the blockchain distributed ledger thanks to blockchain technology, which does away with the idea of an IoT central server. Blockchain technology could provide a more effective answer to the issues that IoT systems confront. Transactional privacy, decentralization, the immutability of data, non-repudiation, transparency, pseudonymity, and traceability, as well as integrity, authorization, system transparency, and fault tolerance, are the primary security features of blockchain technology. The Smart contact is verified, put into use, and then shared as a Distributed Ledger Technology (DLT) over a Pier-to-Pier (P2P) network as a function of blockchain (Wylde et al. 2022b ). The authors created and put into use smart, secure fuzzy blockchain architecture. This framework makes use of a unique fuzzy DL model, improved adaptive neuro-fuzzy inference system (ANFIS)-based attack detection, fuzzy matching (FM), and fuzzy control system (FCS) for network attack detection (Yazdinejad et al. 2023 ).
Figure 11 illustrates the specification of blockchain technology concerning cloud environment. Blockchain is a distributed ledger across a peer-to-peer network. Blockchain features can help cloud services reach their full potential and address the many problems that arise. A collection of connected building blocks that are coupled and arranged in an appropriate linear sequence is used to keep a detailed record of all transactions. Decentralization, Security, transparency, availability, traceability, and many more are the essential features of blockchain technology which is highlighted by the figure presented by the author.
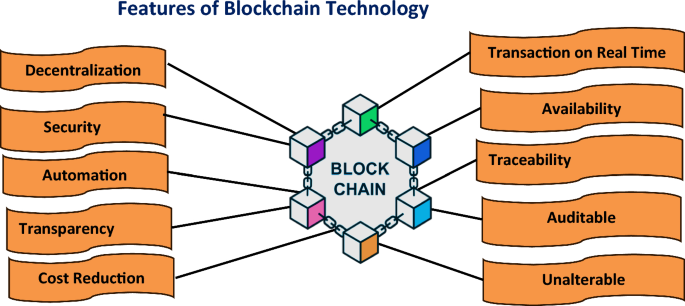
Specifications of blockchain technology
Decentralization Decentralization in blockchain technologies refers to the dividing of control and decision-making across the network users instead of concentrating on the centralized entity. It addresses the limitations of a centralized system in which security is compromised.
Security The network architecture of blockchain technology provides security by minimizing the risk of failure. The allocated characteristics of blockchain strengthen the security. Attacks on any nodes are less likely to put the entire network at risk.
Automation An intelligent system automates the carrying out of the consensus, and removes the requirement of human intervention. Smart contact enhances transaction efficiency. It automatically implements the terms and conditions of the agreement whenever conditions or terms are fulfilled.
Transparency The transactions made on blockchain appeared to every participant over the network. The method not only provides trust and security to the data but also promotes accountability which helps to gain the faith of the user.
Cost Reduction In conventional systems, the settlement of financial transactions might take several days, causing delays and capital lockups. Blockchain eliminates the need for drawn-out clearing and settlement procedures by enabling very immediate transaction settlement.
Transaction in Real Time Transactions in real time can be made over the network. Real-time transaction implements techniques like Proof-of-stake to attain quick acknowledgment of transactions. This technique permits fast agreement among nodes on the validity of transactions.
Availability Transaction availability guarantees a user’s ability to communicate with the network and complete transactions dependably. Availability may still be impacted by network maintenance, upgrades, and sporadic problems.
Traceability Traceability features of blockchain enable to provide of transparent transactions. The transaction can be can be traced by the user. Blockchain is helpful in industries where the origin, transportation, and ownership of assets need to be accurately recorded and validated because of its traceability capabilities.
Auditable Real-time transaction auditing is made possible by the blockchain ledger’s transparency and immutability. At any time, participants can check the transaction history.
Unalterable The ability of blockchain to keep a safe and impenetrable record of transactions is one of its unchangeable features. Once information is posted to the blockchain, it is impossible to change, guaranteeing the information’s integrity and immutability.
Figure 12 portrays the basic components of blockchain. These components work in agreement to form a secure ledger system. Blockchain technology comprises those elements that work in agreement to formulate a secure and decentralized ledger. Supply chain management, decentralized applications, voting systems, healthcare, and property registration are the major applications of technology. Each component plays an important role in blockchain functioning.
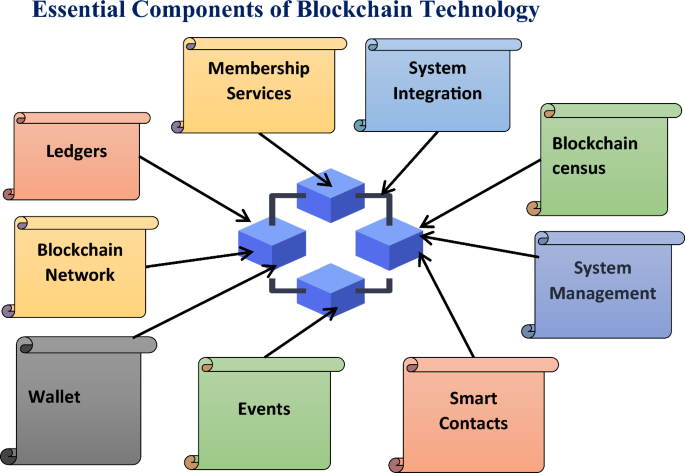
Basic building blocks for blockchain
Ledgers Ledgers in blockchain technology are used to maintain transparency of the record in transactions. Every node contains a replica of the complete ledger, protecting it from being altered or any kind of fraud. The ledger with the help of a chain of blocks carries out transactions; blocks represent every transaction in ledgers.
Blockchain Network In a Blockchain network, the user is referred to as nodes. All the users collectively validate the transaction and record the transaction in a synchronized manner. Blocks are depositors for a cluster of transactions. Blocks contain a timestamp, which is of location of preciously occurred transactions and a cryptographic has for the current blocks.
Wallet Blockchain technology wallets are tools that let users manage and store funds safely. It enables users to access the public and private keys, facilitating the blockchain’s ability to transfer and receive crypto-currency. There are two types of wallets Hot Wallets: Easy for frequent transactions and internet-connected. Cold wallets are offline and thought to be safer for storing money over time.
Events Events are essential for improving the automation, transparency, and usability of blockchain systems. They give decentralized networks a way to communicate and update in real time. The execution of smart contracts or modifications to the ledger’s current state is frequently linked to blockchain events.
Smart Contacts The blockchain records the complete history of smart contract execution, making it transparent and auditable. It has numerous applications such as in supply chain, finance, etc. Based on predetermined criteria, smart contracts carry out actions.
System Management Blockchain technology’s system management characteristics include a variety of operations and procedures meant to guarantee the safety, effectiveness, and appropriate operation of the blockchain network. These characteristics are essential to preserving the dependability and integrity of decentralized systems.
Blockchain Census The blockchain’s consensus techniques, like Proof of Work (PoW) and Proof of Stake (PoS), help make the system resistant to censorship. By requiring a distributed agreement from all network users, these mechanisms make it more difficult for one party to control or restrict transactions.
System Integration Establishing seamless connectivity between different blockchain networks and between blockchain technology and traditional systems is the aim of blockchain system integration. The successful communication and information sharing between diverse systems is greatly dependent upon standards, protocols, and APIs (Application Programming Interfaces).
Membership Services Membership services features of blockchain technology a functions and features for a member or participant management in a blockchain network. It is used to manage access control, rights, and user identity on the network. The elements of the blockchain ecosystem enhance its overall security, governance, and usefulness.
Figure 13 shows the internal workings of the blockchain technology which is used to perform any kind of transaction over the cloud securely. The figure above is a step-by-step explanation of how the transaction takes place over the cloud. In step 1 , first of all, the transaction is generated by any one of the users and request is the directed to the server for processing further. In step 2 , the server after receiving the transaction request creates a block that can appear for the transaction. Next step i.e. step 3 a chain or interconnect block is created using algorithms to authenticate the user and ensure that the request is being made by the authenticated user. Further, in step 4 , this block is distributed to other users or groups of users to grant permission for the transaction to happen. Once the group of users grants permission the transaction or block will be successfully added to the existing blocks that are shown in step 5 in the above figure. If any user disapproves or denies it, then the block will not be added to the existing chain. The modification that has taken place is permanent and cannot be modified further. Therefore, it ensures data security in the cloud environment.
Functioning of blockchain technology in Cloud IoT systems
Real-World Applications of Blockchain Technology in Enhancing Security and Data Protection is as follows:
Walmart Walmart one of the retail companies collaborated with IBM to implement blockchain technology to track the movement of products, maintain food safety, and minimizes the possibility of contamination.
MedRec MedRec is an MIT-developed blockchain-based electronic medical record system that gives individuals more control over their health information while maintaining confidentiality and privacy.Allows for real-time transactions and decentralized energy management by utilizing blockchain to increase the security and efficiency of energy distribution.
Ripple Ripples operates in the financial sector. It uses blockchain techniques to protect the data and enables real-time secure payment.
Follow My Vote Follow My Vote creates a safe, open, and verifiable online voting system using blockchain technology.
uPort uPort is a blockchain-based self-governing identity platform that empowers people to take control of their online personas while improving security and privacy.
10 Unveiling the challenges: addressing current issues in data security and privacy within the Cloud IoT environment
10.1 open ended problems.
The open-ended problems and primary issues about data security and privacy in cloud IoT systems are summarized in Table 3 . Table 3 also provides targeted solutions to address each challenge, thereby ensuring a robust and secure cloud-IoT ecosystem.
10.2 Research gaps
The research gaps of data security and privacy preservation in cloud-IoT technologies are described in Table 4 .
11 Conclusions
The IoT is on the verge of substantial expansion, necessitating secure data transfer and robust cloud storage solutions. As IoT devices become more widespread, the need for enhanced cloud security is critical. Current methods, while helpful, do not fully address modern threats, thus requiring the development of more advanced protective systems. Manufacturers can improve security by creating products grounded in a detailed assessment of IoT security risks and objectives. Effective measures include the implementation of strong authentication methods like One Time Password (OTP) features and robust cryptographic systems. While Machine Learning (ML) is widely used for data protection in various sectors, it faces challenges such as scalability issues with small data sets. Integrating ML with homomorphic encryption shows promise but needs further development. The evolving sophistication of hackers compels reliance on ML and AI for defense strategies. Additionally, blockchain technology, supported by platforms like Ethereum and Hyper-ledger Fabric, offers considerable potential for enhancing security, though more research is necessary to standardize these techniques.
The authors recommend three key solutions:
Develop new security standards and frameworks for cloud-based and IoT devices to tackle modern security challenges.
Create more efficient ML models for real-time attack prediction.
Design robust privacy protection protocols for blockchain technology to safeguard sensitive data.
The authors encountered several limitations during their research, including restricted access to relevant literature, challenges in avoiding plagiarism, difficulties in summarizing a large body of research, integrating information logically, and keeping up with the latest studies.
Data availability
The data and material used in this paper are appropriately referred to and described in this paper.
Code availability
The source code/custom code/software application will be provided when required.
Abdulkader ZA (2022) Cloud data security mechanism using the lightweight cryptography. Optik 271:170084
Article Google Scholar
Abdulsalam YS, Hedabou M (2021) Decentralized data integrity scheme for preserving privacy in cloud computing. In 2021 International conference on security, pattern analysis, and cybernetics (SPAC), Chengdu, China, pp 607–612
Abed AK, Anupam A (2022) Review of security issues in the Internet of Things and artificial intelligence-driven solutions. Internet Technol Lett. https://doi.org/10.1002/spy2.285
Abouelmehdi K, Beni-Hessane A, Khaloufi H (2018) Big healthcare data: preserving security and privacy. J Big Data 5:1
Ahmed W et al (2021) Security in next generation mobile payment systems: a comprehensive survey. IEEE Access 9:115932–115950
Ahmad W, Rasool A, Javed AR, Baker T, Jalil Z (2022) Cyber security in IoT-based cloud computing: a comprehensive survey. Electronics 11:16
Akmal M, Syangtan B, Alchouemi A (2021) Enhancing the security of data in cloud computing environments using Remote Data Auditing. In: 2021 IEEE 6th International conference on innovative technology in intelligent system and industrial applications (CITISIA), Sydney, Australia, pp 1–10
Alabdulatif A, Thilakarathne NN, Kalinaki K (2023) A novel cloud enabled access control model for preserving the security and privacy of medical Big Data. Electronics 12:2646
Albugmi A, Alassafi MO, Walters R, Wills G (2016) Data security in cloud computing. 2016 Fifth International conference on future generation communication technologies (FGCT), London, UK, pp. 55–59
Al-Dhaqm A et al (2021) Digital forensics subdomains: the state of the art and future directions. IEEE Access 9:152476–152502
Al Hamid HA, Rahman SMM, Hossain MS, Almogren A, Alamri A (2017) A security model for preserving the privacy of medical Big Data in a healthcare cloud using a fog computing facility with pairing-based cryptography. IEEE Access 5:22313–22328
Ali J, Roh BH, Lee B, Oh J, Adil M (2020) A machine learning framework for prevention of software-defined networking controller from DDoS attacks and dimensionality reduction of Big Data. In: 2020 International conference on information and communication technology convergence (ICTC), Jeju, Korea (South), pp 515–519
Almutairi W, Moulahi T (2023) Joining federated learning to blockchain for digital forensics in IoT. Computers 12:157
Alnaim AK, Alwakeel AM (2023) Machine-learning-based IoT–edge computing healthcare solutions. Electron MDPI 12:1027
Google Scholar
Alouffi B, Hasnain M, Alharbi A, Alosaimi W, Alyami H, Ayaz M (2021) A systematic literature review on cloud computing security: threats and mitigation strategies. IEEE Access 9:57792–57807
Alrasheed SH, Aiedalhariri M, Adubaykhi SA, El Khediri S (2022) Cloud computing security and challenges: issues, threats, and solutions. In: 2022 5th Conference on cloud and Internet of Things (CIoT), Marrakech, Morocco, pp 166–172
Alzoubi YI, Ahmad AAA, Jaradat A (2021) Fog computing security and privacy issues, open challenges, and blockchain solution: an overview. Int J Electr Comput Eng (IJECE) 11(6):5081–5088
Andrew J, Karthikeyan J (2019) Privacy-preserving Internet of Things: techniques and applications. Int J Eng Adv Technol (IJEAT) 8(6):3229
Arora A, Khanna A, Rastogi A, Agarwal A (2017) Cloud security ecosystem for data security and privacy. In: 2017 7th International conference on cloud computing, data science & engineering - confluence, Noida, India, IEEE, pp 288–292
Atiewi S, Al-Rahayfeh AA, Almiani M, Yussof S, Alfandi O, Abugabah A, Jararweh Y (2020) Scalable and secure Big Data IoT system based on multifactor authentication and lightweight cryptography. IEEE Access 8:113498–113511
Awaysheh FM, Aladwan MN, Alazab M, Alawadi S, Cabaleiro JC, Pena TF (2022) Security by design for Big Data frameworks over cloud computing. IEEE Trans Eng Manage 69(6):3676–3693
Ayofe Azeez NA, Vyver CVD (2019) Security and privacy issues in e-health cloud-based system: a comprehensive content analysis. Egyptian Inform J 20(2):97–108
Basit A, Zafar M, Liu X et al (2021) A comprehensive survey of AI-enabled phishing attacks detection techniques. Telecommun Syst 76:139–154
Bedi RK, Singh J, Gupta SK (2021) An efficient and secure privacy-preserving multi-cloud storage framework for mobile devices. Int J Comput Appl 43:1–11
Bertino E (2016) Big Data security and privacy. In: 2016 IEEE International conference on Big Data (Big Data), Washington, DC, USA, pp 3–3
Binjubeir M, Ahmed AA, Ismail MAB, Sadiq AS, Khurram Khan M (2020) Comprehensive survey on Big Data privacy protection. IEEE Access 8:20067–20079
Butpheng C, Yeh K-H, Xiong H (2020) Security and privacy in IoT-cloud-based e-health systems—a comprehensive review. Symmetry MDPI 12:1191
Campos EM, Saura PF, González-Vidal A, Hernández-Ramos JL, Bernabé JB, Baldini G, Skarmeta A (2022) Evaluating federated learning for intrusion detection in Internet of Things: review and challenges. Comput Netw 203:108661
Cha SC, Hsu TY, Xiang Y, Yeh K-H (2019) Privacy enhancing technologies in the Internet of Things: perspectives and challenges. IEEE Internet Things J 6(2):2159–2187
Chaowei Y, Qunying H, Zhenlong L, Kai L, Fei H (2017) Big Data and cloud computing: innovation opportunities and challenges. Int J Digit Earth. https://doi.org/10.1080/17538947.2016.1239771
Chen J, Ramanathan L, Alazab M (2021) Holistic Big Data integrated artificial intelligent modelling to improve privacy and security in data management of smart cities. Microprocess Microsyst 81:103722
Chen Q, Wu L, Jiang C (2022) ES-PPDA: an efficient and secure privacy-protected data aggregation scheme in the IoT with an edge-based XaaS architecture. J Cloud Comp 11:20
Chenthara S, Ahmed K, Wang H, Whittaker F (2019) Security and privacy-preserving challenges of e-health solutions in cloud computing. IEEE Access 7:74361–74382
Choudhury T, Gupta A, Pradhan S, Kumar P, Rathore YS (2017) Privacy and security of Cloud-Based Internet of Things (IoT). In: 2017 3rd International conference on computational intelligence and networks (CINE), Odisha, India, pp 40–45
Duan H, Zheng Y, Wang C, Yuan X (2019) Treasure collection on foggy islands: building secure network archives for Internet of Things. IEEE Internet Things J 6(2):2637–2650
Dutkiewicz L et al (2022) Privacy-preserving techniques for trustworthy data sharing: opportunities and challenges for future research. In: Curry E, Scerri S, Tuikka T (eds) Data spaces. Springer, Cham
Gai K, Qiu M, Zhao H (2021) Privacy-preserving data encryption strategy for Big Data in mobile cloud computing. IEEE Transact Big Data 7(4):678–688
Ghaffar Z, Ahmed S, Mahmood K, Islam SH, Hassan MM, Fortino G (2020) An improved authentication scheme for remote data access and sharing over cloud storage in cyber-physical-social-systems. IEEE Access 8:47144–47160
Gnana Sophia S, Thanammal KK, Sujatha SS (2023) Secure storage and accessing the data in the cloud using optimized homomorphic encryption. J Control Decision. https://doi.org/10.1080/23307706.2022.2078436
Gupta I, Singh AK, Lee C-N, Buyya R (2022) Cloud computing research center, secure data storage and sharing techniques for data protection in cloud environments: a systematic review, analysis, and future directions. IEEE Access. https://doi.org/10.1109/ACCESS.2022.3188110
Hamzah Amlak GM, Kraidi Al-Saedi KH (2023) Data mining techniques for cloud privacy preservation. Int J Intell Syst Appl Eng 11(6s):246–256
Hassija V, Chamola V, Saxena V, Jain D, Goyal P, Sikdar B (2019) A survey on IoT security: application areas, security threats, and solution architectures. IEEE Access 7:82721–82743
Henze M, Wolters B, Matzutt R, Zimmermann T, Wehrle K (2017) Distributed configuration, authorization and management in the cloud-based Internet of Things. 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, NSW, Australia, pp 185–192
Himeur Y, Sohail SS, Bensaali F, Amira A, Alazab M (2022) Latest trends of security and privacy in recommender systems: a comprehensive review and future perspectives. Comput Secur 118:102746
Hiremath S, Kunte S (2017) A novel data auditing approach to achieve data privacy and data integrity in cloud computing. In: 2017 International conference on electrical, electronics, communication, computer, and optimization techniques (ICEECCOT), Mysuru, India, pp 306–310
Hong-Yen T, Jiankun H (2019) Privacy-preserving Big Data analytics a comprehensive survey. J Parallel Distribut Comput 134:207–218
Hossain MS, Muhammad G, Abdul W, Song B, Gupta BB (2018) Cloud-assisted secure video transmission and sharing framework for smart cities. Futur Gener Comput Syst 83:596–606
Hou Y, Garg S, Hui L, Jayakody DNK, Jin R, Hossain MS (2020) A data security enhanced access control mechanism in mobile edge computing. IEEE Access 8:136119–136130
Hurrah NN, Parah SA, Sheikh JA, Al-Turjman F, Muhammad K (2019) Secure data transmission framework for confidentiality in IoTs. Ad Hoc Netw 95:101989
Ishaq A, Qadeer B, Shah MA, Bari N (2021) A comparative study on securing electronic health records (EHR) in cloud computing. In: 2021 26th International conference on automation and computing (ICAC), Portsmouth, United Kingdom, pp 1–7
Jahromi AN, Karimipour H, Dehghantanha A, Choo K-KR (2021) Toward detection and attribution of cyber-attacks in iot-enabled cyber-physical systems. IEEE Internet Things J 8(17):13712–13722
Jain SK, Kesswani N (2023) A noise-based privacy-preserving model for the Internet of Things. Complex Intell Syst 9:3655–3679
Jain P, Gyanchandani M, Khare N (2016) Big Data privacy: a technological perspective and review. J Big Data 3:25
Jain P, Gyanchandani M, Khare N (2019) Enhanced secured map reduce layer for Big Data privacy and security. J Big Data 6:30
Javeed D, Gao T, Saeed MS, Khan MT (2023) FOG-Empowered augmented-intelligence-based proactive defensive mechanism for IoT-enabled smart industries. IEEE Internet Things J 10(21):18599–18608. https://doi.org/10.1109/JIOT.2023.3288563
Javeed D, Saeed MS, Ahmad I, Adil M, Kumar P, Najmul Islam AKM (2024a) Quantum-empowered federated learning and 6G wireless networks for IoT security: Concept, challenges and future directions. Futur Gener Comput Syst 160:577–597. https://doi.org/10.1016/j.future.2024.06.023
Javeed D, Saeed MS, Adil M, Kumar P, Jolfaei A (2024b) A federated learning-based zero trust intrusion detection system for Internet of Things. Ad Hoc Netw 162:103540. https://doi.org/10.1016/j.adhoc.2024.103540
Javid T, Faris M, Beenish H, Fahad M (2020) Cybersecurity and data privacy in the cloudlet for preliminary healthcare Big Data analytics. In: 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, pp 1–4
Jeong J, Joo JWJ, Lee Y, Son Y (2019) Secure cloud storage service using bloom filters for the Internet of Things. IEEE Access 7:60897–60907
Jiang Q, Kumar N, Ma J, Shen J, He D, Chilamkurti N (2016) A privacy-aware two-factor authentication protocol based on elliptic curve cryptography for wireless sensor networks. Int J Network Mgmt. https://doi.org/10.1002/nem.1937
Jusak J, Mahmoud SS, Laurens R, Alsulami M, Fang Q (2022) A new approach for secure cloud-based electronic health record and its experimental testbed. IEEE Access 10:1082–1095
Kaaniche N, Laurent M (2017) Data security and privacy preservation in cloud storage environments based on cryptographic mechanisms. Comput Commun 111:120–141
Kabir AA, Elmedany M, Sharif W, Saeed M (2023) Securing IoT devices against emerging security threats: challenges and mitigation techniques. J Cyber Secur Technol. https://doi.org/10.1080/23742917.2023.2228053
Karie NM, Sahri NM, Yang W, Valli C, Kebande VR (2021) A review of security standards and frameworks for IoT-based smart environments. IEEE Access 9:121975–121995
Kaur K, Syed A, Mohammad A, Halgamuge MN (2017) Review: an evaluation of major threats in cloud computing associated with Big Data. In: 2017 IEEE 2nd International conference on Big Data analysis (ICBDA), Beijing, China, pp 368–372
Khan S, Parkinson S, Qin Y (2017) Fog computing security: a review of current applications and security solutions. J Cloud Comp 6:19
Khan HK, Pradhan R, Chandavarkar BR (2021) Hybrid cryptography for cloud computing. In: 2021 2nd International conference for emerging technology (INCET), Belagavi, India, pp 1–5
Krishnaraj N, Sangeetha S (2022) A study of data privacy in Internet of Things using privacy preserving techniques with its management. Int J Eng Trends Technol 70(3):54–65
Kumar S, Tiwari P, Zymbler M (2019) Internet of Things is a revolutionary approach for future technology enhancement: a review. J Big Data 6:111
Kumar A (2021) Framework for data security using DNA cryptography and HMAC technique in cloud computing. In: 2021 Second International conference on electronics and sustainable communication systems (ICESC), Coimbatore, India, pp 898-903
Kumar V, Alameemi AMA, Kumari A, Ahmad M, Falah MW, Abd El-Latif AA (2022) PSEBVC: provably secure ECC and biometric based authentication framework using smartphone for vehicular cloud environment. IEEE Access 10:84776–84789
Kumar A, Khan SB, Pandey SK et al (2023) Development of a cloud-assisted classification technique for the preservation of secure data storage in smart cities. J Cloud Comp 12:92
Li Y, Zhang F (2022) An efficient certificate-based data integrity auditing protocol for cloud-assisted WBANs. IEEE Internet Things J 9(13):11513–11523
Lin J, Yu W, Zhang N, Yang X, Zhang H, Zhao W (2017) A survey on Internet of Things: architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J 4(5):1125–1142
Loai AT, Gokay S (2021) Reconsidering Big Data security and privacy in cloud and mobile cloud systems. J King Saud Univ Comput Inform Sci 33(7):810–819
Lone AN, Mustajab S, Alam M (2023) A comprehensive study on cybersecurity challenges and opportunities in the IoT world. Secur Privacy 6:e318
Lu X, Pan Z, Xian H (2020) An efficient and secure data sharing scheme for mobile devices in cloud computing. J Cloud Comp 9:60
Mahfoudhi S, Frehat M, Moulahi T (2019) Enhancing cloud of things performance by avoiding unnecessary data through artificial intelligence tools. In: 2019 15th International wireless communications & mobile computing conference (IWCMC), Tangier, Morocco, pp 1463–1467
Mahrous WA, Farouk M, Darwish SM (2021) An enhanced blockchain-based IoT digital forensics architecture using fuzzy hash. IEEE Access 9:151327–151336
Majeed A, Khan S, Hwang SO (2022) Toward privacy preservation using clustering based anonymization: recent advances and future research outlook. IEEE Access 10:53066–53097
Mei R, Yan HB, He Y, Wang Q, Zhu S, Wen W (2022). Considerations on evaluation of practical cloud data protection. CONCERT 2022. In: Communications in computer and information science, vol 1699. Springer, Singapore
Mihailescu MI, Nita SL, Asalomia BL, Rogobete MG, Racuciu C (2022) Customized authorization process for cloud computing and IoT using attribute-based encryption. In: 2022 14th International conference on electronics, computers and artificial intelligence (ECAI), IEEE Ploiesti, Romania, pp 1–4
Mishra JK, Janarthanan MC (2023) Cloud computing security: machine and deep learning models analysis. Macromol Symp 407:2100521
Mishra K, Bhattacharjee V, Saket S et al (2022) Cloud and Big Data security system’s review principles: a decisive investigation. Wireless Pers Commun 126:1013–1050
Mishra A, Jabar TS, Alzoubi YI, Mishra KN (2023) Enhancing privacy-preserving mechanisms in cloud storage: a novel conceptual framework. Concurr Computat Pract Exper. https://doi.org/10.1002/cpe.7831
Moqurrab SA, Tariq N, Anjum A et al (2022) A Deep learning-based privacy-preserving model for smart healthcare in Internet of medical things using fog computing. Wireless Pers Commun 126:2379–2401
Morioka E, Sharbaf MS (2016) Digital forensics research on cloud computing: An investigation of cloud forensics solutions. In: 2016 IEEE symposium on technologies for homeland security (HST), Waltham, MA, USA, pp 1–6
Moulahi T, El Khediri S, Ullah Khan R, Zidi S (2021) A fog computing data reduction level to enhance the cloud of things performance. Int J Commun Syst 34(9):e4812
Muzammal SM et al (2018) Counter measuring conceivable security threats on smart healthcare devices. IEEE Access 6:20722–20733
Nadian-Ghomsheh A, Farahani B, Kavian M (2021) A hierarchical privacy-preserving IoT architecture for vision-based hand rehabilitation assessment. Multimed Tools Appl 80:31357–31380
Namakshenas D, Yazdinejad A, Dehghantanha A, Srivastava G (2024) Federated quantum-based privacy-preserving threat detection model for consumer Internet of Things. IEEE Trans Consum Electron. https://doi.org/10.1109/TCE.2024.3377550
Nanda P, He X, Yang LT (2020) Security, trust and privacy in cyber (STPCyber): future trends and challenges. Futur Gener Comput Syst 109:446–449
Nasiraee H, Ashouri-Talouki M (2022) Privacy-preserving distributed data access control for CloudIoT. IEEE Trans Dependable Secure Comput 19(4):2476–2487
Navin Prasad S, Rekha C (2023) Blockchain-based IAS protocol to enhance security and privacy in cloud computing. Measur Sens 28:100813
Niu L, Wang F, Li J, Han T, Liu D (2019) Development of agricultural Internet of Things monitoring system combining cloud computing and WeChat technology. In: 2019 IEEE 8th Joint international information technology and artificial intelligence conference (ITAIC), Chongqing, China, pp 1457–1460
Ogunniye G, Kokciyan N (2023) A survey on understanding and representing privacy requirements in the Internet-of-Things. J Art Intell Res 76:163–192
Pandey NK, Kumar K, Saini G et al (2023) Security issues and challenges in a cloud of things-based applications for industrial automation. Ann Oper Res. https://doi.org/10.1007/s10479-023-05285-7
Pathak M, Mishra KN, Singh SP, Mishra A (2023) An automated smart centralised vehicle security system for controlling the vehicle thefts/hacking using IOT and facial recognition. In: 2023 International conference on computational intelligence and knowledge economy (ICCIKE), Dubai, United Arab Emirates, pp 516–521
Pawlicki M, Pawlicka A, Kozik R, Choraś M (2023) The survey and meta-analysis of the attacks, transgressions, countermeasures, and security aspects common to the Cloud Edge and IoT. Neurocomputing 551:126533
Pioli L, Dorneles CF, de Macedo DDJ et al (2022) An overview of data reduction solutions at the edge of IoT systems: a systematic mapping of the literature. Computing 104:1867–1889
Quach S, Thaichon P, Martin KD et al (2022) Digital technologies: tensions in privacy and data. J of the Acad Mark Sci 50:1299–1323
Rachit BS, Ragiri PR (2021) Security trends in Internet of Things: a survey. SN Appl Sci 3:121
Radoglou Grammatikis PI, Sarigiannidis PG, Moscholios ID (2019) Securing the Internet of Things: challenges, threats and solutions. Internet of Things 5:41–70
Rahman SMM, Hossain MA, Hassan MM, Alamri A, Alghamdi A, Pathan M (2016) Secure privacy vault design for distributed multimedia surveillance system. Futur Gener Comput Syst 55:344–352
Ram Mohan P, Murali Krishna S, Siva Kumar AP (2018) Privacy preservation techniques in Big Data analytics: a survey. J Big Data 5:33
Ravi Kumar P, Herbert Raj P, Jelciana P (2018) Exploring data security issues and solutions in cloud computing. Procedia Comput Sci 125:691–697
Ray SM, Dutta S (2020) Big Data security issues from the perspective of IoT and cloud computing: a review. Recent Adv Comput Sci Commun. https://doi.org/10.2174/2666255813666200224092717
Reddy Y (2018) Big Data security in cloud environment. In: 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International conference on high performance and smart computing, (HPSC) and IEEE international conference on intelligent data and security (IDS), Omaha, NE, USA, pp 100–106
Rejin PR, Paul RD, Alavi AH (2019) Verification of data integrity and co-operative loss recovery for secure data storage in cloud computing. Cogent Eng. https://doi.org/10.1080/23311916.2019.1654694
Rodríguez E, Otero B, Canal R (2023) A survey of machine and deep learning methods for privacy protection in the Internet of Things. Sensors 23:1252
Roslin Dayana K, Shobha Rani P (2023) Secure cloud data storage solution with better data accessibility and time efficiency. Automatika J Control Measur Electron Comput Commun 64(4):751–758
Sadhu PK, Yanambaka VP, Abdelgawad A (2022) Internet of Things: security and solutions survey. MDPI Sens 22:7433
Safaei Yaraziz M et al (2023) Recent trends towards privacy-preservation in the Internet of Things, its challenges and future directions. IET Circuits Devices Syst 17(2):53–61
Sakhnini J et al (2023) A generalizable deep neural network method for detecting attacks in industrial cyber-physical systems. IEEE Syst J 17(4):5152–5160
Sarwar K, Yongchareon S, Jian Yu, Rehman SU (2021) A survey on privacy preservation in fog-enabled Internet of Things. ACM Comput Surv 55(1):2
Schiller E, Andy A, Jara F, Jonathan S, Michael Z, Burkhard S (2022a) Landscape of IoT security. Comput Sci Rev 44:100467
Schiller E, Aidoo A, Fuhrer J, Stahl J, Ziörjen M, Stiller B (2022b) Landscape of IoT security. Comput Sci Rev Internet Things 44:100467
Selvarajan S, Srivastava G, Khadidos AO et al (2023) An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J Cloud Comp 12:38
Sharma Y, Gupta H and Khatri S. K. (2019) A Security Model for the Enhancement of Data Privacy in Cloud Computing. 2019 Amity international conference on artificial intelligence (AICAI), Dubai, United Arab Emirates, IEEE, pp 898–902
Shi Y (2018) Data security and privacy protection in public cloud. In 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, pp 4812–4819
Shin S, Kwon T (2020) A privacy-preserving authentication, authorization, and key agreement scheme for wireless sensor networks in 5G-integrated Internet of Things. IEEE Access 8:67555–67571
Shukla RS (2022) IoT based designing of secure data storage system in distributed cloud system with Big Data using cryptography algorithm. In: 2022 11th International conference on system modeling & advancement in research trends (SMART), Moradabad, India, pp 264-270
Sicari S, Rizzardi A, Coen-Porisini A (2022) Insights into security and privacy towards fog computing evolution. Comput Secur 120:102822
Silva LV, Barbosa P, Marinho R (2018) Security and privacy aware data aggregation on cloud computing. J Internet Serv Appl 9:6
Simsek I (2023) Zero-knowledge and identity-based authentication, authorization, access control, and key exchange for publish/subscribe in Internet of Things. In: 2023 6th conference on cloud and Internet of Things (CIoT), Lisbon, Portugal, pp 47–54
Singh N, Singh AK (2018) Data privacy protection mechanisms in cloud. Data Sci Eng 3:24–39
Sookhak M, Yu FR, Zomaya AY (2018) Auditing Big Data storage in cloud computing using divide and conquer tables. IEEE Trans Parallel Distrib Syst 29(5):999–1012
Stergiou C, Psannis KE, Xifilidis T, Plageras AP, Gupta BB (2018) Security and privacy of Big Data for social networking services in the cloud. IEEE INFOCOM 2018—IEEE conference on computer communications workshops (INFOCOM WKSHPS), Honolulu, HI, USA, pp 438–443
Sumithra R, Parameswari R (2022) Data privacy and data protection security algorithms for Big Data in the cloud. Int J Health Sci 6(S2):7613–7621
Sun PJ (2019) Privacy protection and data security in cloud computing: a survey, challenges, and solutions. IEEE Access 7:147420–147452
Tahirkheli AI, Shiraz M, Hayat B, Idrees M, Sajid A, Ullah R, Ayub N, Kim K-I (2021) A survey on modern cloud computing security over smart city networks: threats, vulnerabilities, consequences, countermeasures, and challenges. Electronics 10:1811
Tang Z (2020) A preliminary study on data security technology in Big Data cloud computing environment. In: 2020 International conference on Big Data & artificial intelligence & software engineering (ICBASE) IEEE, Bangkok, Thailand, pp 27–30
Thabit F, Alhomdy S, Jagtap S (2021) A new data security algorithm for cloud computing based on genetics techniques and logical-mathematical functions. Int J Intell Netw Sci Direct 2:18–33
Tian Y, Kaleemullah MM, Rodhaan MA, Song B, Al-Dhelaan A, Ma T (2019) A privacy-preserving location service for cloud-of-things system. J Parallel Distrib Comput 123:215–222
Ullah F et al (2019) Cyber security threats detection in Internet of Things using deep learning approach. IEEE Access 7:124379–124389
Unal E, Sen-Baidya S, Hewett R (2018) Towards prediction of security attacks on software defined networks: a Big Data analytic approach. In: 2018 IEEE International conference on Big Data (Big Data), Seattle, WA, USA, pp 4582–4588
Waheed N, He X, Ikram M, Usman M, Hashmi SS, Usman M (2020) Security and privacy in IoT using machine learning and blockchain: threats and countermeasures. ACM Comput Surv 53(6):122
Wang H (2021) Research on risk and supervision of financial Big Data application based on cloud computing. In: 2021 IEEE International conference on advances in electrical engineering and computer applications (AEECA), Dalian, China, pp 507–510
Wang F, Wang H, Xue L (2021) Research on data security in Big Data cloud computing environment. In: 2021 IEEE 5th advanced information technology, electronic and automation control conference (IAEAC), Chongqing, China, pp 1446–1450
Wang Y, Ni K, Wang X, Zhu J (2022) Design of automatic weather monitoring and forecasting system based on Internet of Things and Big Data. In: 2022 International conference on sustainable computing and data communication systems (ICSCDS), Erode, India, pp 979–982
Wazid M, Das AK, Hussain R, Succi G, Rodrigues JJPC (2019) Authentication in cloud-driven IoT-based Big Data environment: survey and outlook. J Syst Architect 97:185–196
Williams P, Dutta IK, Daoud H, Bayoumi M (2022) A survey on security in the Internet of Things with a focus on the impact of emerging technologies. Internet Things 19:100564
Wylde V, Rawindaran N, Lawrence J et al (2022a) Cybersecurity, data privacy, and blockchain: a review. SN Comput Sci 3:127
Wylde V, Rawindaran N, Lawrence J, Balasubramanian R, Prakash E, Jayal A, Khan I, Hewage C, Platts J (2022b) Cybersecurity, data privacy, and blockchain: a review. SN Comput Sci 3:127
Xiao Y, Jia Y, Liu C, Cheng X, Yu J, Lv W (2019) Edge computing security: state of the art and challenges. Proc IEEE 107(8):1608–1631
Xie Q, Zhang C, Jia X (2023) Security-aware and efficient data deduplication for edge-assisted cloud storage systems. IEEE Trans Serv Comput 16(03):2191–2202
Yahuza M et al (2020) Systematic review on security and privacy requirements in edge computing: state of the art and future research opportunities. IEEE Access 8:76541–76567
Yan H, Gui W (2021) Efficient identity-based public integrity auditing of shared data in cloud storage with user privacy preserving. IEEE Access 9:45822–45831
Yao H (2022) Data storage security system based on cloud computing. In: 2022 IEEE 2nd International conference on electronic technology, communication and information (ICETCI), Changchun, China, pp 1220–1223
Yazdinejad A, Dehghantanha A, Parizi RM, Hammoudeh M, Karimipour H, Srivastava G (2022) Block hunter: federated learning for cyber threat hunting in blockchain-based IIoT networks. IEEE Trans Industr Inf 18(11):8356–8366
Yazdinejad A, Dehghantanha A, Parizi RM, Srivastava G, Karimipour H (2023) Secure intelligent fuzzy blockchain framework: effective threat detection in IoT networks. Comput Ind 144:2023
Yazdinejad A, Dehghantanha A, Srivastava G (2024a) AP2FL: auditable privacy-preserving federated learning framework for electronics in healthcare. IEEE Trans Consum Electron 70(1):2527–2535
Yazdinejad A, Dehghantanha A, Srivastava G, Karimipour H, Parizi RM (2024b) Hybrid privacy-preserving federated learning against irregular users in next-generation Internet of Things. J Syst Architect 148:103088
Ye C, Cao W, Chen S (2021) Security challenges of blockchain in Internet of Things: systematic literature review. Trans Emerging Tel Tech 32:e4177
Yin H, Chen E, Zhu Y, Zhao C, Feng R, Yau SS (2022) Attribute-based private data sharing with script-driven programmable ciphertext and decentralized key management in blockchain Internet of Things. IEEE Internet Things J 9(13):10625–10639
Yu Y et al (2017) Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans Inf Forensics Secur 12(4):767–778
Yu K et al (2022) A blockchain-based shamir’s threshold cryptography scheme for data protection in industrial Internet of Things settings. IEEE Internet Things J 9(11):8154–8167
Zaman S et al (2021) Security threats and artificial intelligence based countermeasures for Internet of Things networks: a comprehensive survey. IEEE Access 9:94668–94690
Zarandi MA, Dara Rozita A, Evan F (2020) A survey of machine learning-based solutions to protect privacy in the Internet of Things. Comput Secur 96:101921
Zhang J, Chen B, Zhao Y, Cheng X, Hu F (2018) Data security and privacy-preserving in edge computing paradigm: survey and open issues. IEEE Access 6:18209–18237
Zhang W, Jin S (2020) Research and application of data privacy protection technology in cloud computing environment based on attribute encryption. In: 2020 IEEE International conference on power, intelligent computing and systems (ICPICS), Shenyang, China, pp 994–996
Zhao X-P, Jiang R (2020) Distributed machine learning oriented data integrity verification scheme in cloud computing environment. IEEE Access 8:26372–26384
Zhou J, Cao Z, Dong X, Vasilakos AV (2017) Security and privacy for cloud-based IoT: challenges. IEEE Commun Mag 55(1):26–33
Zhu H et al (2019) A secure and efficient data integrity verification scheme for Cloud-IoT based on short signature. IEEE Access 7:90036–90044
Download references
Author information
Authors and affiliations.
Department of Computer Science & Engineering, Birla Institute of Technology, Jharkhand, India
Mayank Pathak, Kamta Nath Mishra & Satya Prakash Singh
You can also search for this author in PubMed Google Scholar
Contributions
Mayank Pathak, Kamta Nath Mishra and Satya Prakash Singh have equally contributed in writing this paper after having various discussions.
Corresponding author
Correspondence to Kamta Nath Mishra .
Ethics declarations
Conflicts of interest.
Being the corresponding author I declare that there is no conflict of interest with any person or organization for this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Pathak, M., Mishra, K.N. & Singh, S.P. Securing data and preserving privacy in cloud IoT-based technologies an analysis of assessing threats and developing effective safeguard. Artif Intell Rev 57 , 269 (2024). https://doi.org/10.1007/s10462-024-10908-x
Download citation
Accepted : 06 August 2024
Published : 27 August 2024
DOI : https://doi.org/10.1007/s10462-024-10908-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Blockchain technologies
- Cloud computing
- Data breach
- Data securities
- Digital forensic
- Fog computing
- Internet of Things
- Machine learning
- Privacy protection
- Find a journal
- Publish with us
- Track your research
Advertisement
Republicans Gain Edge as Voters Worry About Economy, Times/Siena Poll Finds
With elections next month, independents, especially women, are swinging to the G.O.P. despite Democrats’ focus on abortion rights. Disapproval of President Biden seems to be hurting his party.
- Share full article

By Shane Goldmacher
- Oct. 17, 2022
Republicans enter the final weeks of the contest for control of Congress with a narrow but distinct advantage as the economy and inflation have surged as the dominant concerns, giving the party momentum to take back power from Democrats in next month’s midterm elections, a New York Times/Siena College poll has found.
The poll shows that 49 percent of likely voters said they planned to vote for a Republican to represent them in Congress on Nov. 8, compared with 45 percent who planned to vote for a Democrat. The result represents an improvement for Republicans since September, when Democrats held a one-point edge among likely voters in the last Times/Siena poll. (The October poll’s unrounded margin is closer to three points, not the four points that the rounded figures imply.)
With inflation unrelenting and the stock market steadily on the decline, the share of likely voters who said economic concerns were the most important issues facing America has leaped since July , to 44 percent from 36 percent — far higher than any other issue. And voters most concerned with the economy favored Republicans overwhelmingly, by more than a two-to-one margin.
Which party’s candidate are you more likely to vote for in this year’s election for Congress?

Likely voters
65 and older
BY RACE/ETHNICITY
BY EDUCATION
Bachelor’s
degree or higher
No bachelor’s
Don’t know/refused to answer

Democratic candidate
Republican candidate
18 to 29 years old
Bachelor’s degree
No bachelor’s degree
Both Democrats and Republicans have largely coalesced behind their own party’s congressional candidates. But the poll showed that Republicans opened up a 10-percentage point lead among crucial independent voters, compared with a three-point edge for Democrats in September, as undecided voters moved toward Republicans.
The biggest shift came from women who identified as independent voters. In September, they favored Democrats by 14 points. Now, independent women backed Republicans by 18 points — a striking swing given the polarization of the American electorate and how intensely Democrats have focused on that group and on the threat Republicans pose to abortion rights.
4 Takeaways From the Campaign Trail

With elections less than a month away, our reporters are across the country following candidates. Scandal roiled the Los Angeles City Council, Mitch McConnell affirmed his support for Herschel Walker, and Senate and governor candidates in Nevada sought endorsements.
Here’s a look at the week in political news →
Los Angeles was rocked by news that three City Council members took part in a secretly recorded conversation involving racist comments . Faced with swirling public condemnation, including from President Biden, the Council president, Nury Martinez, resigned, while the other two officials have so far stayed put.
In the critical swing state of Nevada, the Democratic Senate incumbent, Catherine Cortez Masto, received an endorsement from 14 family members of her Republican opponent, Adam Laxalt. In the governor’s race, the state’s largest teachers’ union announced that it wouldn’t endorse either candidate.
Polling in Georgia found less support among female, Black and independent voters for Herschel Walker, the Republican Senate candidate. He trails Senator Raphael Warnock, but by just three points, within the margin of error. Senator Mitch McConnell said he’d “stick with Walker,” an anti-abortion candidate who has been accused of paying for an abortion.
Two Democratic groups said they would pour millions of dollars into local races in a half dozen states before the midterms in hopes of winning back legislatures. The groups, the States Project and the National Democratic Redistricting Committee, are particularly focused on protecting voting and abortion rights .
Catch up on more political news.

We are having trouble retrieving the article content.
Please enable JavaScript in your browser settings.
Thank you for your patience while we verify access. If you are in Reader mode please exit and log into your Times account, or subscribe for all of The Times.
Thank you for your patience while we verify access.
Already a subscriber? Log in .
Want all of The Times? Subscribe .

IMAGES
COMMENTS
This review collected some important reports and scientific papers on the emerging environmental problems that will feature prominently in the future. Global renewable power production (2017 ...
Increasing demands on ecosystems, decreasing biodiversity, and climate change are among the most pressing environmental issues of our time. As changing weather conditions are leading to increased vector-borne diseases and heat- and flood-related deaths, it is entering collective consciousness: environmental issues are human health issues. In public health, the field addressing these issues is ...
Environmental Research is a multi-disciplinary journal publishing high quality and novel information about anthropogenic issues of global relevance and applicability in a wide range of environmental disciplines, and demonstrating …. View full aims & scope. $3590. Article publishing charge. for open access.
Previous research has suggested that people's economic interests can lead to a crowding out of concerns for the environment if there is a perceived trade-off between the two issues 33,34.
Addressing the Global Environmental Crisis: Strategies for Sustainable Development. August 2023. West Science Social and Humanities Studies 1 (02):63-75. DOI: 10.58812/wsshs.v1i02.190. License. CC ...
Many nations have embraced burning wood pellets to produce electricity — under the assumption that it is carbon neutral. But research shows this approach can boost greenhouse-gas emissions and ...
Original Paper 01 August 2024 Pages: 443 - 451 Climate risks and adaptation strategies: the perspectives of farmers in coastal Ghana ... Environmental Studies and Sciences Podcast covers some of the latest research on environmental issues and hot topics in the environmental field, with leading academics and upcoming environmental researchers ...
Secondary data is used to identify sustainability issues such as environmental, social, and economic viability. To better understand the problem, gathered the information in this report from various media outlets, research agencies, policy papers, newspapers, and other sources. This review is a sectorial assessment of climate change mitigation ...
18 AbSTrACT. four environmental dimensions of energy security—climate change, air pollution, water availability and quality, and land-use change—and the environmental impact of. 13 energy systems on each are discussed in this paper. Climate change threatens more land, people, and economies in Asia and small Pacific island states than any ...
The Environmental Challenges, a companion journal of Journal of Environmental Management, is an international, multidisciplinary journal dedicated to advancing research and understanding in various fields of environmental management and environmental science.The primary aim of this journal is to provide a platform for the publication of original research findings, review articles, and ...
Today's Wicked Problems . A number of complex issues have been identified by the scientific community as wicked problems: Climate change. In 2015, 195 countries adopted the first universal climate agreement, noting the need for an effective and progressive response to the urgent threat of climate change (United Nations 2015).An increasing range of global adverse effects from climate change ...
Environmental pr oblems, espe-. cially human-induced climat e change, contin ue. to have a prominen t place on the international. policy agenda. "Environmental p roblems" is a ubiqui tous. but ...
Our policy data are publicly available to spur further research on ex post climate policy evaluation. ... A structured and harmonised climate policy database to monitor countries' mitigation action" (OECD Environment Working Papers 203, OECD, ... Purchase this issue in print. Buy a single issue of Science for just $15 USD. Media Figures ...
2 Research Department, Institute for Social and Environmental Research Nepal (ISER-N), ... physical conditions but are interpreted through social and cultural layers of understanding that shape environmental issues. This paper investigates environmental and climate-relevant perceptions within two communities in the Terai region of Nepal; the ...
Our review involved analysing 78 research papers published internationally and in Australia over the past 20 years. We wanted to assess how ecological resilience was addressed in nature-based ...
Abstract. This paper advances two arguments about environmental problems. First, it interrogates the strength and limitations of empiricist accounts of problems and issues offered by actor-network theory. Drawing on the work of C.S. Peirce, it considers how emerging environmental problems often lead to abductive inferences about the existence ...
First craft a paper outline with your main ideas organized, and a thesis statement. A logical outline will make it easy to gradually flesh out ideas and eventually produce complete paragraphs with good transitions between them. Make sure all the sections serve the purpose of the paper outlined in the thesis statement.
Environmental education is a process aimed at developing a world population that is aware of and concerned about the total environment and its associated problems and which has the knowledge, attitudes, commitments and skills to work individually and collectively towards the. ISSN: 2146-0329. *E-mail: [email protected].
Research by historians, political scientists and environmental scientists is increasingly showing that the environmental effects of war have long-term humanitarian consequences. Conflicts ...
This comprehensive list of environmental issues research paper topics provides a wide range of areas to choose from for your research. The topics cover major environmental issues, from climate change and air pollution to biodiversity loss and overpopulation. Each of these topics can be explored from various angles, providing a rich source of ...
The „environmental crisis‟ is caused due to environment and ecological changes as a result of. developmental process of the 'economic and technological man" of the present century. In fact if ...
This virtual special issue (VSI) of Environmental Research considers papers from the 16th International Conference on Mercury as a Global Pollutant held in Cape Town, South Africa, 21-26 July 2024. The conference theme "From Minamata to Africa and Beyond: Addressing Mercury Challenges in Global Environment Change" provides a timely ...
This sample environmental issues research paper features: 6700 words (approx. 22 pages), an outline, and a bibliography with 39 sources. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced writers for help.
In Progress Issue: February 2023. Journal of Environmental Issues and Climate Change (JEICC) is an open-access, peer-reviewed journal that publishes original research articles in English, triannually in February, June and October, that are focused on natural and climatic elements of environmental studies.The journal emphasizes interdisciplinary approaches that combine techniques from ...
The Special Issue "Exclusive Papers of the Editorial Board Members and Topical Advisory Panel Members of Catalysts in Section "Catalytic Materials" contains 14 peer-reviewed research articles and 1 review paper (Contributions 1-15), which broadly focus on the field of homogeneous and heterogeneous catalysis, with an emphasis on synthesis, physico-chemical characterizations, and ...
they operate as an eective strategy for addressing many environmental. issues like soil degradation, global warming, and ecological imbalance. Thus, this paper aimed to close a research and ...
The Crimson Historical Review at the University of Alabama is a nationally acclaimed, highly selective, peer-reviewed, undergraduate, historical research journal that is now accepting submissions for its thirteenth issue. Publishing with the CHR offers bright researchers an opportunity to experience the rigors of the publication process in a supportive environment.
A few issues were discovered by authors after analysis and assessments of various aspects of the published research papers. The research analysis reveals that the existing methods need to be further improved to address the contemporary dangers related to data security and privacy. Based on the research reports, it can be stated that safe end-to ...
Hemlata et al. [21] listed local environmental issues as desertification, water scarcity, water contamination, soil contamination, noise pollution, heat, and dust. Global environmental issues, on ...
With elections next month, independents, especially women, are swinging to the G.O.P. despite Democrats' focus on abortion rights. Disapproval of President Biden seems to be hurting his party.